

VLAN Network Segmentation and Security- Chapter 5. This is Chapter 5 in Tom Olzak‘s book, “Enterprise Security: A practitioner’s guide.”
Chapter 4 is available here:Attack Surface Reduction – Chapter 4 Chapter 3 is available here: Building the Foundation: Architecture Design – Chapter 3 Chapter 2 is available here: Risk Management – Chapter 2 Chapter 1 is available here: Enterprise Security: A practitioner’s guide – Chapter 1 In Chapter 4, we examined system attack surface reduction. The next step is moving out from systems to the network attack surface. Traditional flat networks present a single surface to the outside and almost nothing to internal threats. By segmenting a network, and applying appropriate controls, we can break a network into a multi-layer attack surface that hinders threat agents/actions from reaching our hardened systems. Implémentation de MPLS avec Cisco.
Configuring IP Access Lists. Introduction This document describes how IP access control lists (ACLs) can filter network traffic.
It also contains brief descriptions of the IP ACL types, feature availability, and an example of use in a network. Access the Software Advisor (registered customers only) tool in order to determine the support of some of the more advanced Cisco IOS® IP ACL features. contains assigned numbers of well-known ports. RFC 1918 contains address allocation for private Internets, IP addresses which should not normally be seen on the Internet.
Note: ACLs might also be used for purposes other than to filter IP traffic, for example, defining traffic to Network Address Translate (NAT) or encrypt, or filtering non-IP protocols such as AppleTalk or IPX. Prerequisites Requirements There are no specific prerequisites for this document. Components Used This document discusses various types of ACLs. The information in this document was created from the devices in a specific lab environment.
CCNA R&S Study Sessions. Greg Cote - Greg Coté is the Product Manager for the Routing and Switching, Design, and Wireless career certification tracks.
As a certification PM, Greg is responsible for planning and coordinating revisions to these certs as well as the related trainings. Prior to this role he's worked in various Cisco BUs as a marketing product manager on several routing platforms including the ASR1000, ASR9000, and ISR over my 12+ years at Cisco. Nikita Singh - Nikita holds a CCIE in Routing and Switching. She has worked with Cisco TAC and is now a Content Engineer in Cisco Learning.
She has closely worked on designing the new CCNP v2 Routing and Switching Courses. David Major- Marketing Manager, Cisco Wendell Odom - Wendell (CCIE No. 1624) is one of the most respected author of Cisco networking books in the world. André Laurent - My focus over the past decade has been to provide business relevant solutions for my customers regardless of my position. Windows - Add secondary IP addresses to interface - SomoIT.net. Sometimes it is neccesary to configure a network interface to listen on more than one IP (for example, web servers containing multiple SSL certificates…) After adding the new secondary IPs, If not explicitly avoided, outgoing traffic can be generated also by these instead of only by the primary.
These can lead to connection errors (for example firewall receiving unexpected IPs instead of the primary). There are multiple methods to add new IPs to an interface: Network configuration GUI The usual method in the “Network and sharing center” – “Change adapter settings” section. But this method creates the interface with the “SkipAsSource” attribute as “false” by default. Comprendre les différences entre la fibre Gpon, P2P, Active Ethernet, FTTLA. Comprendre les différences entre la fibre "FTTH Gpon", "FTTH P2P", "FTTH Active Ethernet" et "FTTLA"+ une synthèse des réponses des 4 grands FAI (France Telecom, SFR, Free et Bouygues Telecom) à la consultation publique de l'ARCEP concernant les modalités d’accès au FTTH en dehors des zones très denses.
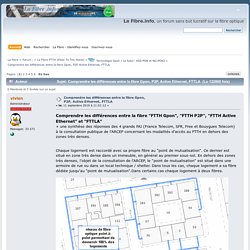
Chaque logement est raccordé avec sa propre fibre au "point de mutualisation". Ce dernier est situé en zone très dense dans un immeuble, en général au premier sous-sol. En dehors des zones très denses, l'objet de la consultation de l'ARCEP, le "point de mutualisation" est situé dans une armoire de rue ou dans un local technique / shelter. Quel ports Ouvrir pour Communiquer en VOIP (SIP) ? - Blog de Partage IT.
QoS. NAT. Tier 1 network. Calculateur de Masque IPv4. Calculatrice IP. 1.
Présentation Cette calculatrice IP a pour but de faciliter la gestion des masques réseaux dans une infrastructure. Donc, si vous avez une adresse IP et un masque réseau, quelque soit son format, vous pouvez utiliser la calculatrice générale ci-dessous, et ainsi vérifiez si 2 adresses sont bien dans le même réseau ou non, et par conséquent si elles peuvent utiliser la même gateway ou non, les mêmes accès réseaux... L'autre partie de cette page vous permet, à partir de 2 adresses IP distinctes de calculer le masque réseau le plus petit contenant les 2 equipements, et vous affiche le masque réseau sous ses différentes formes. 2. ABC RESEAU : Les bases pour comprendre et créer un réseau local.
Le Monde des Réseaux. Internetworking Technology Handbook. From DocWiki Creating a PDF of the Internetworking Technology Handbook Create a PDF of the Internetworking Technology Handbook that you can save on your computer and print.
Internetworking Basics An internetwork is a collection of individual networks, connected by intermediate networking devices, that functions as a single large network. Internetworking refers to the industry, products, and procedures that meet the challenge of creating and administering internetworks.