

XKEYSCORE: NSA's Google for the World's Private Communications. Illustrations by Blue Delliquanti and David Axe for The Intercept One of the National Security Agency’s most powerful tools of mass surveillance makes tracking someone’s Internet usage as easy as entering an email address, and provides no built-in technology to prevent abuse.
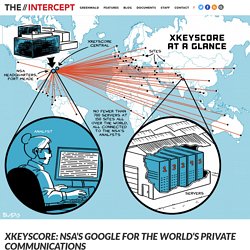
Today, The Intercept is publishing 48 top-secret and other classified documents about XKEYSCORE dated up to 2013, which shed new light on the breadth, depth and functionality of this critical spy system — one of the largest releases yet of documents provided by NSA whistleblower Edward Snowden. The NSA’s XKEYSCORE program, first revealed by The Guardian, sweeps up countless people’s Internet searches, emails, documents, usernames and passwords, and other private communications. XKEYSCORE is fed a constant flow of Internet traffic from fiber optic cables that make up the backbone of the world’s communication network, among other sources, for processing. Inside the NSA's War on Internet Security. When Christmas approaches, the spies of the Five Eyes intelligence services can look forward to a break from the arduous daily work of spying.
In addition to their usual job -- attempting to crack encryption all around the world -- they play a game called the "Kryptos Kristmas Kwiz," which involves solving challenging numerical and alphabetical puzzles. The proud winners of the competition are awarded "Kryptos" mugs. Encryption -- the use of mathematics to protect communications from spying -- is used for electronic transactions of all types, by governments, firms and private users alike. But a look into the archive of whistleblower Edward Snowden shows that not all encryption technologies live up to what they promise. One example is the encryption featured in Skype, a program used by some 300 million users to conduct Internet video chat that is touted as secure. For the NSA, encrypted communication -- or what all other Internet users would call secure communication -- is "a threat".
U.S. threatened massive fine to force Yahoo to release data. The U.S. government threatened to fine Yahoo $250,000 a day in 2008 if it failed to comply with a broad demand to hand over user communications — a request the company believed was unconstitutional — according to court documents unsealed Thursday that illuminate how federal officials forced American tech companies to participate in the National Security Agency’s controversial PRISM program.
The documents, roughly 1,500 pages worth, outline a secret and ultimately unsuccessful legal battle by Yahoo to resist the government’s demands. The company’s loss required Yahoo to become one of the first to begin providing information to PRISM, a program that gave the NSA extensive access to records of online communications by users of Yahoo and other U.S. -based technology firms. “We already knew that this was a very, very important decision by the FISA Court of Review, but we could only guess at why,” said Stephen Vladeck, a law professor at American University. Carol D. US given heads up about newspaper data destruction. WASHINGTON (AP) — The Obama administration knew in advance that the British government would oversee destruction of a newspaper's hard drives containing leaked National Security Agency documents last year, newly declassified documents show.
The White House had publicly distanced itself on whether it would do the same to an American news organization. The Guardian newspaper, responding to threats from the British government in July 2013, destroyed the data roughly a month after it and other media outlets first published details from the top secret documents leaked by former NSA contractor Edward Snowden. After news of the Guardian incident broke the following month, White House spokesman Josh Earnest said it would be "very difficult to imagine a scenario in which that would be appropriate.
" NSA seeks to build quantum computer that could crack most types of encryption. [Read an annotated description of the Penetrating Hard Targets project] The development of a quantum computer has long been a goal of many in the scientific community, with revolutionary implications for fields such as medicine as well as for the NSA’s code-breaking mission.

With such technology, all current forms of public key encryption would be broken, including those used on many secure Web sites as well as the type used to protect state secrets. Leaked memos reveal GCHQ efforts to keep mass surveillance secret. The UK intelligence agency GCHQ has repeatedly warned it fears a "damaging public debate" on the scale of its activities because it could lead to legal challenges against its mass-surveillance programmes, classified internal documents reveal.
Memos contained in the cache disclosed by the US whistleblower Edward Snowden detail the agency's long fight against making intercept evidence admissible as evidence in criminal trials – a policy supported by all three major political parties, but ultimately defeated by the UK's intelligence community. Foremost among the reasons was a desire to minimise the potential for challenges against the agency's large-scale interception programmes, rather than any intrinsic threat to security, the documents show. GCHQ and European spy agencies worked together on mass surveillance. The German, French, Spanish and Swedish intelligence services have all developed methods of mass surveillance of internet and phone traffic over the past five years in close partnership with Britain's GCHQ eavesdropping agency.
The bulk monitoring is carried out through direct taps into fibre optic cables and the development of covert relationships with telecommunications companies. A loose but growing eavesdropping alliance has allowed intelligence agencies from one country to cultivate ties with corporations from another to facilitate the trawling of the web, according to GCHQ documents leaked by the former US intelligence contractor Edward Snowden. Data Pirates of the Caribbean: The NSA Is Recording Every Cell Phone Call in the Bahamas. Photo credit: Getty Images The National Security Agency is secretly intercepting, recording, and archiving the audio of virtually every cell phone conversation on the island nation of the Bahamas.
According to documents provided by NSA whistleblower Edward Snowden, the surveillance is part of a top-secret system – code-named SOMALGET – that was implemented without the knowledge or consent of the Bahamian government. Instead, the agency appears to have used access legally obtained in cooperation with the U.S. Drug Enforcement Administration to open a backdoor to the country’s cellular telephone network, enabling it to covertly record and store the “full-take audio” of every mobile call made to, from and within the Bahamas – and to replay those calls for up to a month. All told, the NSA is using MYSTIC to gather personal data on mobile calls placed in countries with a combined population of more than 250 million people. Illustration by Josh Begley. Glenn Greenwald: how the NSA tampers with US-made internet routers. For years, the US government loudly warned the world that Chinese routers and other internet devices pose a "threat" because they are built with backdoor surveillance functionality that gives the Chinese government the ability to spy on anyone using them.
Yet what the NSA's documents show is that Americans have been engaged in precisely the activity that the US accused the Chinese of doing. The drumbeat of American accusations against Chinese internet device manufacturers was unrelenting. In 2012, for example, a report from the House Intelligence Committee, headed by Mike Rogers, claimed that Huawei and ZTE, the top two Chinese telecommunications equipment companies, "may be violating United States laws" and have "not followed United States legal obligations or international standards of business behaviour". GCHQ and NSA Targeted Private German Companies. The headquarters of Stellar, a company based in the town of Hürth near Cologne, are visible from a distance.
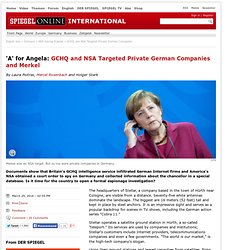
Seventy-five white antennas dominate the landscape. The biggest are 16 meters (52 feet) tall and kept in place by steel anchors. It is an impressive sight and serves as a popular backdrop for scenes in TV shows, including the German action series "Cobra 11. " US tech giants knew of NSA data collection, agency's top lawyer insists. The senior lawyer for the National Security Agency stated on Wednesday that US technology companies were fully aware of the surveillance agency’s widespread collection of data. Rajesh De, the NSA general counsel, said all communications content and associated metadata harvested by the NSA under a 2008 surveillance law occurred with the knowledge of the companies – both for the internet collection program known as Prism and for the so-called “upstream” collection of communications moving across the internet.
In Just 6 Months, the NSA Spied on More Than 59,000 Accounts. Illustration: Patrick George/Getty Images Four tech giants embroiled in the government’s secret PRISM collection program reported today that they had received classified national security demands for the contents of at least 59,000 user accounts during the first half of 2013. In the wake of a legal battle to provide more transparency about the number of government national security requests they receive for customer information, Yahoo reported that between January and June last year, the government sought content for between 30,000 and 40,000 user accounts, mostly using classified court orders from the Foreign Intelligence Surveillance Court.
Google reported that it received FISC requests for content on between 9,000 and 10,000 accounts during the same period. Did Edward Snowden Break His Oath? Should we just stop talking about any form of amnesty for Edward Snowden, because he swore an oath and broke it? In a piece for Slate titled “Why Snowden Won’t (And Shouldn’t) Get Clemency,” Fred Kaplan mentions my suggestion, in a piece for the site, that Jimmy Carter’s pardoning of Vietnam draft dodgers offers “a useful parallel” when thinking of the legal situation of Edward Snowden.
Kaplan writes: This is an odd and flawed argument—logically and legally, but also historically and factually. The errors illustrate how we tend to misremember the past, and misjudge its passions when comparing them to our own. "NSA Scandal" Read a CSEC document that was first acquired by Edward Snowden. In early 2012, Communications Security Establishment Canada analyzed telecommunications flows surrounding Brazil’s Ministry of Mines and Energy. The ministry was described by CSEC as “a new target to develop.” Top-Secret Document Reveals NSA Spied On Porn Habits As Part Of Plan To Discredit 'Radicalizers' WASHINGTON -- The National Security Agency has been gathering records of online sexual activity and evidence of visits to pornographic websites as part of a proposed plan to harm the reputations of those whom the agency believes are radicalizing others through incendiary speeches, according to a top-secret NSA document.
The document, provided by NSA whistleblower Edward Snowden, identifies six targets, all Muslims, as “exemplars” of how “personal vulnerabilities” can be learned through electronic surveillance, and then exploited to undermine a target's credibility, reputation and authority. The NSA document, dated Oct. 3, 2012, repeatedly refers to the power of charges of hypocrisy to undermine such a messenger. Among the vulnerabilities listed by the NSA that can be effectively exploited are “viewing sexually explicit material online” and “using sexually explicit persuasive language when communicating with inexperienced young girls.”
Under J. Adriana Usero and Ryan J. GCHQ Monitors Hotel Reservations to Track Diplomats. When diplomats travel to international summits, consultations and negotiations on behalf of governments, they generally tend to spend the night at high-end hotels. When they check-in, in addition to a comfortable room, they sometimes get a very unique form of room service that they did not order: a thorough monitoring by the British Government Communications Headquarters, or GCHQ in short. Intelligence service documents from the archive of NSA whistleblower Edward Snowden show that, for more than three years, GCHQ has had a system to automatically monitor hotel bookings of at least 350 upscale hotels around the world in order to target, search and analyze reservations to detect diplomats and government officials. How the NSA and GCHQ Spied on OPEC. NSA Spying Scandal - SPIEGEL ONLINE - Nachrichten.
Read all NSA related articles in English - Uppdrag Granskning. PRISM. The NSA's Secret Campaign to Crack, Undermine Internet Encryption. The National Security Agency headquarters at Fort Meade, Md., in January 2010. (Saul Loeb/AFP/Getty Images. NSA Successfully Figured Out How to Tap Into VISA’s ‘Complex Transaction Network’ NSA collects millions of e-mail address books globally. Exclusive: NSA Spies on International Bank Transactions. The National Security Agency (NSA) widely monitors international payments, banking and credit card transactions, according to documents seen by SPIEGEL. Revealed: how US and UK spy agencies defeat internet privacy and security. Explaining the latest NSA revelations – Q&A with internet privacy experts. "NSA Scandal" Members Of Congress Denied Information About NSA. What the N.S.A. Wants in Brazil. One of the more curious revelations from Edward Snowden’s trove of secret N.S.A. documents was a recent report that United States spy agencies have been vacuuming up communications in Brazil.
Glenn Greenwald, who lives in Brazil, broke this story in O Globo, one of that country’s major newspapers, on July 6th. Greenwald, in an follow-up piece in the Guardian, pointed to a rough Google translation of his original July 6th report: In the last decade, people residing or in transit in Brazil, as well as companies operating in the country, have become targets of espionage National Security Agency of the United States (National Security Agency - NSA, its acronym in English). There are no precise figures, but last January Brazil was just behind the United States, which had 2.3 billion phone calls and messages spied.
In a way, the N.S.A.’s focus on Brazil seems puzzling. Alexander’s answer was somewhat elliptical (emphasis mine): Alexander’s answer doesn’t seem terribly revealing. Vanee’ M. To hunt Osama bin Laden, satellites watched over Abbottabad, Pakistan, and Navy SEALs. Edward Snowden. Snowdennsa. Edward Snowden: the whistleblower behind the NSA surveillance revelations. U.S. charges Snowden with espionage. Snowden Complaint. Edward Snowden Q and A: NSA whistleblower answers your questions. Edward Snowden. Partner of NSA leaks reporter carried paper with password, says UK. The police’s defence in the Miranda judicial review. Edward Snowden fact-checking: Which surveillance claims were right? Edward Snowden Provides Information on NSA Cyber Spying & Hacking to Hong Kong Newspaper. Druckversion - Cover Story: How the NSA Targets Germany and Europe - SPIEGEL ONLINE - News - International.
The NSA's mass and indiscriminate spying on Brazilians. Revealed: the top secret rules that allow NSA to use US data without a warrant. In Depth Review: New NSA Documents Expose How Americans Can Be Spied on Without A Warrant. Procedures used by NSA to target non-US persons: Exhibit A – full document. Procedures used by NSA to minimize data collection from US persons: Exhibit B – full document. /u/AngryRantingRealist describes PRISM in the context of the "Intelligence Contractors Complex", including allusions (with sources) of a number of related events you should know about via reddit.com. Secret to Prism program: Even bigger data seizure. Is the NSA PRISM leak much less than it seems. PRISM vs Tor. Secret NSA documents show campaign against Tor encrypted network. NSA EgotisticalGiraffe Differ in The Guardian and Washington Post. Jon Pincus - Google+ - +Marc Ambinder , the author, is known for having good…
Yonatan Zunger - Google+ - I have a tremendous number of thoughts about the variou... Solving the mystery of PRISM. Sources: NSA sucks in data from 50 companies. NSA Bombshell Story Falling Apart Under Scrutiny; Key Facts Turning Out to Be Inaccurate. The real story in the NSA scandal is the collapse of journalism. No evidence of NSA's 'direct access' to tech companies. PRISM Program: Obama Administration Held 22 Briefings For Congress On Key FISA Law. White House Defends Phone-Record Tracking as 'Critical Tool'
Obama deflects criticism over NSA surveillance as Democrats sound alarm. Clapper admits secret NSA surveillance program to access user data. Tech Companies Concede to Surveillance Program. U.S. releases details on PRISM. Judge: “NSA exceeded the scope of authorized acquisition continuously” The NSA files. Xbox Live among game services targeted by US and UK spy agencies. NSA files: games and virtual environments paper. World of Spycraft: NSA and CIA Spied in Online Games. Spies Infiltrate a Fantasy Realm of Online Games. NSA considered spying on Australians 'unilaterally', leaked paper reveals. ‘Black budget’ summary details U.S. spy network’s successes, failures and objectives. The Black Budget: Top secret U.S. intelligence funding - Interactive Graphic - Washington Post. Inside the 2013 U.S. intelligence 'black budget'
XKeyscore presentation from 2008 – read in full. XKeyscore: NSA tool collects 'nearly everything a user does on the internet' U.S., British intelligence mining data from nine U.S. Internet companies in broad secret program. Exclusive: NSA pays £100m in secret funding for GCHQ. NSA taps in to systems of Google, Facebook, Apple and others, secret files reveal. NSA infiltrates links to Yahoo, Google data centers worldwide, Snowden documents say. Cringely The Google File System makes NSA's hack blatantly illegal and they know it.
How we know the NSA had access to internal Google and Yahoo cloud data. How the NSA's MUSCULAR program collects too much data from Yahoo and Google. Google encrypts data amid backlash against NSA spying. How Microsoft handed the NSA access to encrypted messages. Boundless Informant: the NSA's secret tool to track global surveillance data. Boundless Informant: NSA explainer – full document text. Boundless Informant NSA data-mining tool – four key slides. 20131104-Mundo-Boundless Informant. 20131104-Mundo-Info Sharing Partners. 20131202-Guardian-DSD Data. NSA slides explain the PRISM data-collection program. NSA files decoded: Edward Snowden's surveillance revelations explained.