

Using enterprise social network analysis to discover the informal power players in the company. Visualize your Twitter network. Network Visualization guest lecture at #DataVizQMSS at @Columbia. Social Network Analysis in Two Parts. Using Social Graphs To Understand Your Enterprise Social Network [Video] Study maps Twitter’s information ecosystem.
2013 Getty Images If you are one of Twitter’s 241 million active users, there’s one constant to the network: it can be incredibly vast and remarkably small.
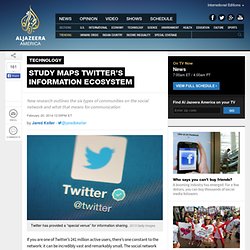
The social network teems with an enormously diverse and intertwined group of people — from journalists and activists to government officials and college students — chatting on a range of topics in an often overwhelming ecosystem of cliques, crews and mobs. Finally, Twitter has something like a map. A report from the Pew Research Internet Project highlights how researchers have developed six general models of the types of communities on the eight-year-old social network. As Pew's researchers see it, these visualizations represent the clearest picture of what civil society looks like when translated into the sprawling wasteland of the Internet. The Pew Research Center normally produces public opinion polls describing American attitudes toward the Internet.
But having a million followers doesn’t necessarily mean you’ll succeed. Social Network Analysis 101. Michael Wu, Ph.D. is Lithium's Principal Scientist of Analytics, digging into the complex dynamics of social interaction and online communities.
He's a regular blogger on the Lithosphere and previously wrote in the Analytic Science blog. You can follow him on Twitter at mich8elwu. Computational Social Networks - Security and Privacy Free Download. Computational Social Networks - Security and Privacy Computational Social Networks - Security and Privacy Ajith Abraham, ISBN: 1447140508 | 2012 | PDF | 351 pages | 6 MB Computational Social Networks - Security and Privacy This book is the second of three volumes that illustrate the concept of social networks from a computational point of view.
Buy Premium Account To Download More Files With Fast Speed. The Potential of Social Network Analysis in Intelligence. Harvesting and Analyzing Tweets. Twitter is a fabulous source for information.
Whenever something is happening, people around the world start tweeting away. Often they include hashtags, allowing us to selectively search for tweets about a certain event or thing. Social network analysis for journalists using the Twitter API. Due to the changed Twitter API, the first part of this course does not work anymore.
We apologize for the inconvenience. Try our new recipe on harvesting and analyzing tweets, which covers much of the same ground. Social Network analysis allows us to identify players in a social network and how they are related to each other. For example: I want to identify people who are involved in a certain topic - either to interview or to understand what different groups are engaging in debate. What you’ll Need: Copyright Images: How to Avoid and Curate Safely. What you should know about Image Licenses Today’s web technology makes it very simple to download any image that you’d like, and then use that image (or a thumbnail) in your own content.
As a good content marketer knows, articles curated with pictures get 47% more click-thru activity than content without, as shown in Curata’s Curation Habits Report 2012. At the same time, some of those images have copyrights and licensing fees associated with them. A select few third party image licensing companies have been known to target unlicensed usage of their images. Not only may they ask you to stop using the images in question, they may attempt to charge retroactive usage fees. There are two ways to proactively protect yourself in such scenarios: Pay royalties for any applicable images you use so that all the images you use are using it in a licensed manner.Avoid copyrighted images. For most cost-conscious curators, the second option is more amenable.
Jessie Coan. How The NSA Uses Social Network Analysis To Map Terrorist Networks. Ever since The Guardian reported that the National Security Agency (NSA) has been collecting the phone record metadata of millions of Americans, the cable talk circuit has been ablaze with pundits demanding answers to what should be obvious questions.

Who knew about the program to collect data? (Apparently, all three branches of government). Who else has been supplying data? (Just about everybody, according to the Washington Post). T N T — The Network Thinkers. The Future of Curation is Evergreen. By Angela Dunn @blogbrevity What is Content Curation?

Content curation is much more than simply collecting things you like. To be an effective curator, you need to have the eye of an editor, a sense of taste like a chef, and your own unique Point of View. How to find communities online using social network analysis. In my last two posts I introduced the Econsultancy Twitter network, and wrote about how we could use social network analysis to identify influencers and innovators in this community.

In this post I'll look at how mapping a network can help us identify sub-groups in the community and target content to them more effectively. Detecting sub-groups in the Econsultancy Twitter network The most famous example of a sharply divided online community is Lada Adamic's analysis of US political bloggers during the 2004 presidential election. Her visualisation clearly shows Democrat (blue) and Republican (red) camps, with very little communication between them. Predictive Policing: Preventing Crime with Data and Analytics. Wednesday, September 18th, 2013 - 14:52 In this report, Dr.
Bachner tells compelling stories of how new policing approaches in communities are turning traditional police officers into “data detectives.” Police departments across the country have adapted business techniques -- initially developed by retailers, such as Netflix and WalMart, to predict consumer behavior -- to predict criminal behavior. The report presents case studies of the experiences of Santa Cruz, CA; Baltimore County, MD; and Richmond, VA, in using predictive policing as a new and effective tool to combat crime. The Key Success Factor in Knowledge Management... What Else? Change...
A Brief Introduction to Social Network Analysis by Orgnet, LLC. Social network analysis [SNA] is the mapping and measuring of relationships and flows between people, groups, organizations, computers, URLs, and other connected information/knowledge entities. The nodes in the network are the people and groups while the links show relationships or flows between the nodes. SNA provides both a visual and a mathematical analysis of human relationships. Management consultants use this methodology with their business clients and call it Organizational Network Analysis [ONA].
ONA allows you to x-ray your organization and reveal the managerial nervous system that connects everything. Immersion: a people-centric view of your email life. Your social networks and the secret story of metadata. Researchers at MIT’s Media Lab have created an application called Immersion, which uses your email to display all of the people you communicate with in a highly visual way. Although it was designed primarily as a way of illustrating a person’s connections and social networks, it has served to highlight the amount of information that is encoded in communication metadata and what can be done with that data without even needing the actual content of emails. This is especially relevant at the moment with the revelations that the US secret service has been engaged in widespread surveillance using email and other personal data sourced from companies such as Google, Apple, Facebook and Microsoft.
Email metadata refers to information such as the sender and recipients of an email. On its own, this information may not be particularly very interesting, especially if as in my case, it is one of 53,129 emails that is in my work Gmail account. EdgeRank Is Dead: Facebook's News Feed Algorithm Now Has Close To 100K Weight Factors. Social-Network Ppt Presentation.