

10 Free desktop Search Software. User Ratings: [Total: 0 Average: 0/5] Here are 10 Free Desktop Search software that let you search for all types of files and folders on your PC.
These desktop search software are normally more advanced than the default search that come with Windows. All these desktop search software are completely free. Google Desktop. Codebox Software - BitMeter II. BitMeter 2 is a bandwidth meter - it allows you to visually monitor your internet connection by displaying a scrolling graph that shows your upload and download speed over time.
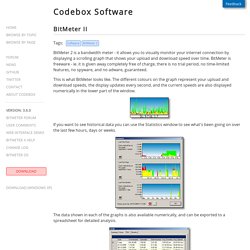
BitMeter is freeware - ie. it is given away completely free of charge, there is no trial period, no time-limited features, no spyware, and no adware, guaranteed. This is what BitMeter looks like. CursorFX - Create custom mouse cursors with CursorFX. Free Mobile Security App for Android. 5 Quick Steps to Manage Software Updates with SUMo. Endpoint Security Manager 3 from Comodo.
Comodo Endpoint Security Manager (ESM) software brings 7 layers of defense – antivirus, firewall, web URL filtering, host intrusion prevention, auto-sandbox (containment), file reputation and viruscope (behavioral analysis) – together under a single offering for customers of all sizes, to protect them from both known and unknown threats.
Whether deployed as a complete security suite or by using the sandbox as a standalone to fortify existing AV solutions, Comodo ESM offers unrivalled endpoint protection for Microsoft Windows servers, desktops, laptops and tablets. The full Comodo Endpoint Security suite brings 7 layers of protection to the point of impact – the endpoint environment. Its disruptive auto-sandbox technology eliminates malware outbreaks and operating system contamination by automatically running untrusted/unknown process in a virtual environment within the existing system and with low system usage requirements. 1 Terms and conditions apply. Features Hardware requirements. Independent Tests of Anti-Virus Software - Real World Protection Test Overview. My thoughts on programming, software and related matters. Sorry, this post is spanish only.
En la tarde de hoy jueves, un compañero de trabajo me comenta que la página principal del sitio www.google.com.py fue modificada. Descartando algún problema con Google en sí (en donde trabajan algunos de los mejores expertos en seguridad del mundo), mi primer sospecha fue que el servicio DNS a nivel Paraguay fue comprometido. Download IObit Freeware. Pdfchain y pdftk. Manipulación de ficheros PDF. ¿Cómo saber si una solución de software libre funcionará bien en tu empresa u organización? Este artículo tiene cerca de 5 años.

Es probable que algunas partes del mismo hayan quedado desactualizadas. 14 terminales en Linux para los fans del intérprete de comandos. Aunque es cierto que para los usuarios nuevos el Terminal es prácticamente un ‘cuco’, no menos cierto es que para muchos constituye la herramienta más poderosa en cualquier sistema de la familia Unix.
Distribuciones hechas para ser Firewall. Los que estamos inmersos en el mundo de GNU/Linux y Software Libre, estamos acostumbrados a que cada día conocemos una distribución distinta, orientadas a cosas muy distintas.

Hoy les traigo un pequeño ejemplo de esto. Pues existen varias (Muchas) Distribuciones basadas o enfocadas en ser FireWall O Cortafuegos. Pero primero.. ¿Que coño es un cortafuegos? Synfig Studio… a que no lo conocías. No soy un diseñador, tampoco soy animador ni nada por el estilo, pero estoy rodeado de ellos, a donde mire tengo un diseñador al lado y esto me hace estar enterado (quiera o no) del mundo del software para diseño y diseño en general, es básicamente una consecuencia, un efecto colateral.

En fin, mas allá de que pueda tener chorrocientos amigos diseñadores (o intentos de los mismos) siempre me terminan metiendo en las típicas discusiones de “eres un friki no se como sobrevives con Linux” (la verdad es que no se como ellos sobreviven con Windows) y además me toca escuchar las mil y un maravillas sobre Adobe y lo “hermosa que es su suite”, que no lo niego, es poderosa. La cosa se pone interesante porque dentro de ese grupo hay un subgrupo que me ha visto trabajar, que ha tenido el privilegio de tocar a mi preciosa (mi pc) y les ha resultado cómodo, atractivo y hasta productivo… a ese grupo los llamo “disidentes hipsters” por cariño.
¿Que pasa con estos disidentes hipsters? Cameyo Presentation. KC Softwares. KC Softwares. Is Your Antivirus Tracking You? You'd Be Surprised At What It Sends. What is ModSecurity and how it works. Soft2Base Automatically Updates 61 Popular Windows Applications. 11 Hidden Windows Secrets and Tricks. TinyWall Brings Advanced Settings To The Windows Firewall. Process Explorer - The Most Powerful Task Manager Replacement [Windows]
Let’s be honest, the Windows Task Manager isn’t that great for understanding and managing the processes running on your computer.
![Process Explorer - The Most Powerful Task Manager Replacement [Windows]](http://cdn.pearltrees.com/s/pic/th/explorer-powerful-replacement-47826481)
Even on Windows 8, where it’s much-improved, the task manager can’t come close to the power of Process Explorer. It’s part of the Sysinternals set of tools that Microsoft purchased – and for good reason. They’re among the most powerful system utilities for Windows. In addition to its power, Process Explorer is also flexible. It’s available from Microsoft as a single .exe file. How To Securely Delete Files From Your HDD Or SSD In Windows. When you hit the delete button, where does that file go?
Does it just evaporate and leave a blank space on your drive? If you’ve been around computers long enough, you know that’s not what happens. But if you’re mostly an email and Facebook type of computer user, you might not know, or not even thought about it. How to Automatically Backup Your Web Server Files With WinSCP over FTP. You’ve heard it time and time again: back up your data. There are plenty of backup solutions, but nothing is better than an easy and free solution.
So with a few lines of code and a very helpful program called WinSCP, we’re going to set up an automatic sync between your FTP server and your home computer. FTP (File Transfer Protocol) is an Internet protocol that allows users to transfer files between computers. Backup your Hard-Drive with SyncBack. I have a mountain of things listed on my Remember The Milk “to-do” list – among them include achieving world peace, eradicating hunger and poverty, finding a cure for cancer and backing up my PC files.
Last week I finally got around to backing up my PC files (the rest will have to wait a while longer unfortunately). I downloaded a program that I have been looking at for a while called SyncBack and I was prompted to finally get it done when I saw SyncBack being profiled on Lifehacker. Five Best Disk Defragmentation Tools. Useful Code Comparing Tools for Web Developers. Developers of many different languages all share the same growing pains.
Buggy source codes will be a nagging problem throughout a developer’s career but a much less-considered issue is in the compiling and the merging of edits from two or more copies of the same source. Luckily there are incredibly helpful tools available for just this type of situation. In looking for software tools to use for code comparisons, you’ll run into a lot of different solutions. Both Windows and Mac OSX have their own free and paid tools, along with a web application which runs universally on all systems. Recommended Reading: Top 10 Free Source Code Editors 1. 10 Tools for Distributed Developer Teams. This series is supported by Rackspace, the better way to do hosting. Learn more about Rackspace's hosting solutions here. 25 Open Source Alternatives For Costly Applications!
25 Font Management Tools Reviewed. If you are one of those people who work with fonts on regular basis, then choosing, comparing and analyzing fonts is a serious business for you. Font management is not always as easy as a walk on the cake. Font management issues like installing and uninstalling fonts, handling missing fonts, taking care of font conflicts always keep graphic designers and typographers on their toes. Also hundreds or thousands of fonts activated on the system can use up considerable amount of system resources which in turn reduces efficiency and productivity. Mac, Windows and Linux platforms have their own font management utilities, but these utilities are not sufficient in a specialized or professional environment.