

Computer Programming Algorithms Directory. University lectures computer science. Whether your goal is to earn a promotion, graduate at the top of your class, or just accelerate your life, lectures can help get you there.
Our archives of lectures cover a huge range of topics and have all been handpicked and carefully designed by experienced instructors throughout the world who are dedicated to helping you take the next step toward meeting your career goals. Lifelong learns can turn their free time turn into self-improvement time. The online lectures on this list are more than lecture notes or a slideshow on a topic -- they were designed for audiences like you, with carefully sequenced themes and topics taught by veteran educators, and often with additional resources for your own independent study. The lectures are available to anybody, completely free of charge. Lecture courses are a valid and vital learning tool, and may be one of the best methods of learning available.
A Stick Figure Guide to the Advanced Encryption Standard (AES) (A play in 4 acts.
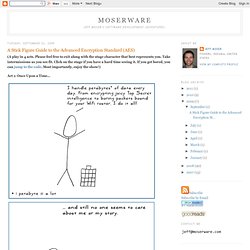
Please feel free to exit along with the stage character that best represents you. Take intermissions as you see fit. Click on the stage if you have a hard time seeing it. If you get bored, you can jump to the code. Most importantly, enjoy the show!) Act 1: Once Upon a Time... Act 2: Crypto Basics Act 3: Details Act 4: Math! Epilogue I created a heavily-commented AES/Rijndael implementation to go along with this post and put it on GitHub. The Design of Rijndael is the book on the subject, written by the Rijndael creators. Please leave a comment if you notice something that can be better explained. Update #1: Several scenes were updated to fix some errors mentioned in the comments.Update #2: By request, I've created a slide show presentation of this play in both PowerPoint and PDF formats.
Low Level Bit Hacks You Absolutely Must Know. I decided to write an article about a thing that is second nature to embedded systems programmers - low level bit hacks.
Bit hacks are ingenious little programming tricks that manipulate integers in a smart and efficient manner. Instead of performing some operation (such as counting the 1 bits in an integer) by looping over individual bits, these programming nuggets do the same with one or two carefully chosen bitwise operations. To get things going I'll assume that you know what the two's complement binary representation of an integer is and also that you know all the the bitwise operations.
I'll use the following notation for bitwise operations in the article: & - bitwise and | - bitwise or ^ - bitwise xor ~ - bitwise not << - bitwise shift left >> - bitwise shift right The numbers in the article are 8 bit signed integers (though the operations work on arbitrary length signed integers) that are represented as two's complement and they are usually named 'x'.
Here we go. Bit Hack #1. 1. 2. Egyptian Maths Bit Twiddling Hacks. By Sean Eron Anderson seander@cs.stanford.edu Individually, the code snippets here are in the public domain (unless otherwise noted) — feel free to use them however you please.

The aggregate collection and descriptions are © 1997-2005 Sean Eron Anderson. The code and descriptions are distributed in the hope that they will be useful, but WITHOUT ANY WARRANTY and without even the implied warranty of merchantability or fitness for a particular purpose. As of May 5, 2005, all the code has been tested thoroughly. Thousands of people have read it. Contents About the operation counting methodology When totaling the number of operations for algorithms here, any C operator is counted as one operation.
Compute the sign of an integer The last expression above evaluates to sign = v >> 31 for 32-bit integers. Alternatively, if you prefer the result be either -1 or +1, then use: sign = +1 | (v >> (sizeof(int) * CHAR_BIT - 1)); // if v < 0 then -1, else +1 sign = (v ! Patented variation: f = v && ! Sean A. Ethiopian multiplication. Ethiopian multiplication You are encouraged to solve this task according to the task description, using any language you may know. A method of multiplying integers using only addition, doubling, and halving. Method:
Binary - it's digitalicious! Binary Game. Skip to Content | Skip to Footer Cisco Binary Game The Cisco Binary Game is the best way to learn and practice the binary number system.
It is great for classes, students and teachers in science, math, digital electronics, computers, programming, logic and networking. It is also a LOT of fun to play for anyone who likes to play fast-paced arcade games. Stephen Wolfram: A New Kind of Science. A compendium of NP optimization problems. AI. Turing. Quantum computing.