

Understanding Nmap Commands: In depth Tutorial with examples. Article by James Hawkins As we all know, Nmap (Network Mapper) is a stealth port scanner widely used by network security experts (including forensics & Pen-testing Experts).
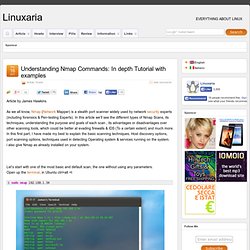
In this article we’ll see the different types of Nmap Scans, its techniques, understanding the purpose and goals of each scan , its advantages or disadvantages over other scanning tools, which could be better at evading firewalls & IDS (To a certain extent) and much more. In this first part, I have made my best to explain the basic scanning techniques, Host discovery options, port scanning options, techniques used in detecting Operating system & services running on the system. i also give Nmap as already installed on your system. Let’s start with one of the most basic and default scan, the one without using any parameters.
Open up the terminal, in Ubuntu ctrl+alt +t This is a basic scan of the local IP address 192.168.1.34, we use sudo to gain administrator privileges, and then we give the target to Nmap. Discovery. Mantra - Free and Open Source Browser based Security Framework. The OSWA-Assistant(tm) - a free standalone wireless auditing toolkit for both IT-professionals and End-Users alike. MoocherHunter™ is a free mobile tracking software tool for the real-time on-the-fly geo-location of wireless moochers, hackers and users of wireless networks for objectionable purposes (e.g. paedophile activity, illegal file downloading, illegal music/video sharing, etc).

(for MoocherHunter™ Law Enforcement Edition, please see below) 100% Made-In-Singapore with ThinkSECURE-proprietary code, MoocherHunter™ was first unveiled to Southeast-Asian law enforcement officials at the Singapore Police Force's invitation-only CyberCrime Investigation Workshop 2008 held in Singapore in April 2008. MoocherHunter™ is licensed under the MoocherHunter™ License as part of the OSWA-Assistant™ wireless auditing LiveCD toolkit (note: only on version 0.9.0.3b and above) which is free for end-user download at MoocherHunter™ identifies the location of an 802.11-based wireless moocher or hacker by the traffic they send across the network.
Download MoocherHunter™ and the OSWA-Assistant™ here. Exploit Search Engine. Chris P.C. srl - ChrisPC Free Anonymous Proxy Software FREE Download - Enjoy your privacy and surf anonymously online and watch TV abroad USA, UK, Hulu, TV.com, iPlayer. ChrisPC Anonymous Proxy Pro is the privacy tool that anybody would need to use to protect their online experience.
Browsing, buying online, watching online TV channels or reading online newspapers are part of our daily life. What is important to know is that when we connect to the Internet we are exposed, our buying/browsing habits and our confidential data are at risk. Of course there are several means and levels of security you can take online, like the ones you have for your home: you have a door lock, you have even a dog barking and you may have also a security system, surveillance system and so on. Every person needs a different level of protection for his/her privacy. Therefore you are in charge with deciding the level of protection you need. But if you would like to protect your privacy and have a low profile on the net, you can start with ChrisPC Anonymous Proxy Pro which can help you in several distinct ways. You will love this filter option since it will make your day easier. The Hackers News.
Apprenez à utiliser Metasploit avec des tutos et des vidéos. Metasploit est une bonne plateforme pour quiconque souhaite tester des failles de sécurité ou réaliser des "exploits" mais il n'est pas simple de l'utiliser et beaucoup se retrouvent vite perdu lorsqu'ils essayent de pousser un peu plus la chose.
Pour vous aider dans votre apprentissage, je vous ai trouvé quelques liens sympa avec des tutoriels et des vidéos expliquant les principes de bases de Metasploit. Tout d'abord, un bon tuto vidéo de chez IronGeek vous montrera (même si vous ne parlez pas anglais), ce qu'il faut faire étape par étape pour utiliser. Ce tuto aborde l'utilisation de Metasploit à partir du Live CD Auditor pour compromettre un Windows XP non patché via la faille RPC DOM. Metasploit chez IronGeek Ce doc est une présentation par HD Moore lui-même au CanSecWest 2006:csw06-moore.pdf Et voici quelques vidéos : Metasploit Unleashed By Offensive Security.