

Twitter Bots Create Surprising New Social Connections. Short Film of the Day: Stuxnet: Anatomy of a Computer Virus. Why Watch?
Because we should challenge how we define a film. Most of the shorts featured in this column are either easy to spot as stories or completely experimental. Even when a documentary short is in the spotlight, it tells a clear tale of people doing things. This short, is none of those things. Stuxnet: Anatomy of a Computer Virus is an informational film made entirely of voice over narration and motion graphics. It’s beautiful, compelling, and it does tell a story, but it’s nothing like most short films. What does it cost?
Check out Stuxnet: Anatomy of a Computer Virus for yourself: Trust us. Exploiting Unexploitable XSS. XSS that are protected by CSRF protection or where other mitigating factors are present are usually considered to be unexploitable or of limited exploitability.

This post details real world examples of exploiting “unexploitable” XSS in Google and Twitter. While the XSS detailed in this post are site specific the methods that were used to exploit them could be applied to other websites with similar implementations. Alex’s (kuza55) Exploiting CSRF Protected XSS served as inspiration for this post. Google Google has services deployed across many different domains and subdomains and as a result requires a way to seamlessly authenticate members who are logged in to their Google Account. Hacked Gadgets - DIY Tech Blog. Protect The Business - Enable Access.
Hexxeh's Blog - Home of…um, well, Hexxeh… The Internet map. The map of the Internet Like any other map, The Internet map is a scheme displaying objects’ relative position; but unlike real maps (e.g. the map of the Earth) or virtual maps (e.g. the map of Mordor), the objects shown on it are not aligned on a surface.
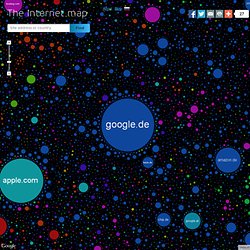
Mathematically speaking, The Internet map is a bi-dimensional presentation of links between websites on the Internet. Every site is a circle on the map, and its size is determined by website traffic, the larger the amount of traffic, the bigger the circle. Users’ switching between websites forms links, and the stronger the link, the closer the websites tend to arrange themselves to each other. Charges and springs To draw an analogy from classical physics, one may say that websites are electrically charged bodies, while links between them are springs. Also, an analogy can be drawn from quantum physics. Anyway, the real algorithm of plotting The Internet map is quite far from the analogies given above. Semantic web. Hack-World.net - The Popular Computer Security Education Site. The War On Cyber. CyberTerrorists - The War On Cyber: CyberTerrorists - The War On Cyber Join us now to get access to all our features.
Once registered and logged in, you will be able to create topics, post replies to existing threads, give reputation to your fellow members, get your own private messenger, and so, so much more. Subscribe to topics and forums to get automatic updates Welcome to CyberTerrorists - The War On Cyber, like most online communities you must register to view or post in our community, but don't worry this is a simple free process that requires minimal information. Take advantage of it immediately, Register Now or Sign In . Looking for Developers !! Autodesk Revit Structure 2012 Build 2315 + Portable by Today, 05:46 AM Application Pack for iPad and iPhone by Today, 05:16 AM p777 God z da Shortest distance from Zero to INFiNiTY.........!!! Locon i want access to TRACK2.NAME ONLINE DUMP SHOP Toggle this category ..:: CT Global Rules, Announcements, News & Feedback ::..
InterN0T - Underground Security Training. iExploit. The Best Hacking Tutorial Sites - Learn Legal Hacking - StumbleUpon. Exploiting Unexploitable XSS. Hacking. Stuxnet - Cyber Warfare. Ritter's Crypto Glossary and Dictionary of Technical Cryptography. Copyright 1995 to 2007 Terry Ritter.

All Rights Reserved. Or use the browser facility "Edit / Find on this page" to search for particular terms. This Glossary started as a way to explain the terms on my cryptography web pages describing my: The value of a definition is insight. But: Consider the idea that cryptography is used to keep secrets: We expect a cipher to win each and every contest brought by anyone who wishes to expose secrets.
Even though the entire reason for using cryptography is to protect secret information, it is by definition impossible to know whether a cipher can do that. Consider the cryptographer who says: "My cipher is strong," and the cryptanalyst who says: "I think your cipher is weak. " The situation is inherently unbalanced, with a bias against the cryptographer's detailed and thought-out claims, and for mere handwave first-thoughts from anyone who deigns to comment. Unfortunately, for users to benefit from cryptography they have to accept some strength argument.
New Hacking Tools Pose Bigger Threats to Wi-Fi Users. Web Performance Analysis. HTTP/Web Security.