

Storing Passwords - done right! Written by: Christoph Wille Translated by: Bernhard Spuida First published: 1/5/2004 Viewed 257725 times. 1766 ratings, avg. grade 4.76 In very many - not to say almost all - Web applications user data is administered, from Web forum to Web shop.
These user data encompass login information of the users which contain the password besides the user name - and this in plain text. A security leak par excellence. Why is storing the user name and password in plain text a security leak? Well, imagine a cracker gaining system access through eventual OS or server software errors, and being able to read the user database. How can this security risk be eliminated? InfoSec Handlers Diary Blog - Hashing Passwords. After talking about SQL Injection, this is the second part of the mini series to help you protect yourself from simple persistent attacks as we have seen them in the last couple months.
A common MO employed in these attacks is to steal passwords from a database via sql injection. Later, the attacker will try to use these passwords to break into other sites for which users may choose the same password. Cryptography - Windows 7 Password Hash Security. 6 Steps to Create an Effective BYOD Plan (Infographic) With workplaces more mobile and interconnected than ever, many employees have the ability to work from home or on the go.
While at first glance, having a bring your own device (BYOD) policy in your office can help with flexibility and cutting costs, it could also lead to security issues and major IT headaches if businesses aren't too careful. So what can managers and IT departments do to ensure the safety of company data and productivity of their employees? Well, actually a lot. Related: A Lack of Communication on Cyber Security Will Cost Your Business Big Computing and security company Bitglass recommends investing in strategy that lets employees choose whatever device they like, keeping in mind that while software and hardware are replaceable, company data is not. For more on connectivity, growth and keeping private and company data separate, check out Bitglass' six-step infographic on creating a BYOD plan that is helpful to everyone. Love infographics » Submit, promote and share infographics. » Find out how to secure your WIFI Network. 41Find out how to secure your WIFI Network Infographic PreviousNext Internet Infographics Leave a reply You must be logged in to post a comment.
Related posts Read more → Computer Virus Google Global market Share Infographic The Most Popular CMS for Your Business Needs The infographic provides a summary of the fundamentals of content management systems, the industries in which they are used and the various types of CMSs available. History Of Apple Timeline Infographic. How to keep your business safe – the one checklist all SMBs should have - McAfee. Last week our nation celebrated the contributions and achievements of small businesses with the 50th anniversary of National Small Business Week.
President Obama paid tribute to the spirit of small business owners in his kickoff speech, highlighting the critical role that SMBs play in the U.S. economy. There are over 28 million small businesses in the U.S. today, making up nearly 45% of total U.S. private payroll. Combine these statistics with the vulnerabilities of small businesses with regards to cybercrime: limited IT support / expertise, limited awareness of cybercrime techniques and limited budgets – make small businesses prime targets for cyber criminals.
How To Add a Second Layer of Encryption to Dropbox [Updated] I started using BoxCryptor, which is mentioned in this thread.
![How To Add a Second Layer of Encryption to Dropbox [Updated]](http://cdn.pearltrees.com/s/pic/th/encryption-dropbox-updated-12931442)
Free for up to 2Gb. Basically, it mounts an encrypted drive on your computer, and whatever you drop there gets encrypted and sent to another folder, which can be your Dropbox folder. If you're going to get your encrypted material somewhere else, you'll need BoxCryptor installed there as well. How To Build A Strong & Perfect Password. With the recent security breach at LinkedIN, with millions of passwords being leaked online, it seems fitting to find out what makes a super secure password.
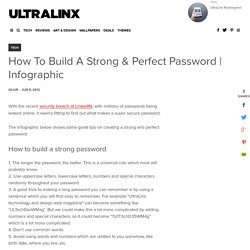
The infographic below shows some great tips on creating a strong and perfect password. 1. The longer the password, the better. This is a universal rule which most will probably know. 2. Use uppercase letters, lowercase letters, numbers and special characters randomly throughout your password. 3. Advertisement — Continue reading below. Vpn News, Videos, Reviews and Gossip - Lifehacker. A Beginner's Guide to Encryption: What It Is and How to Set it Up. How To Set Up a VPN (and Why You Should) How to Encrypt and Hide Your Entire Operating System from Prying Eyes. Public-key cryptography. An unpredictable (typically large and random) number is used to begin generation of an acceptable pair of keys suitable for use by an asymmetric key algorithm.
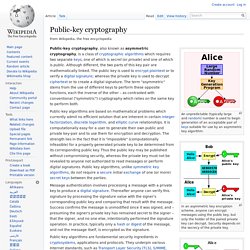
In an asymmetric key encryption scheme, anyone can encrypt messages using the public key, but only the holder of the paired private key can decrypt. Security depends on the secrecy of the private key. In the Diffie–Hellman key exchange scheme, each party generates a public/private key pair and distributes the public key. After obtaining an authentic copy of each other's public keys, Alice and Bob can compute a shared secret offline. The shared secret can be used, for instance, as the key for a symmetric cipher.