

Free Rainbow Tables » Distributed Rainbow Table Generation » LM, NTLM, MD5, SHA1, HALFLMCHALL, MSCACHE. List of Rainbow Tables. This page lists the rainbow tables we generated.
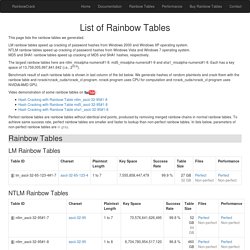
LM rainbow tables speed up cracking of password hashes from Windows 2000 and Windows XP operating system. NTLM rainbow tables speed up cracking of password hashes from Windows Vista and Windows 7 operating system. MD5 and SHA1 rainbow tables speed up cracking of MD5 and SHA1 hashes, respectively. The largest rainbow tables here are ntlm_mixalpha-numeric#1-9, md5_mixalpha-numeric#1-9 and sha1_mixalpha-numeric#1-9. Each has a key space of 13,759,005,997,841,642 (i.e., 253.6).
An Unprecedented Look at Stuxnet, the World's First Digital Weapon. This recent undated satellite image provided by Space Imaging/Inta SpaceTurk shows the once-secret Natanz nuclear complex in Natanz, Iran, about 150 miles south of Tehran.

AP Photo/Space Imaging/Inta SpaceTurk, HO In January 2010, inspectors with the International Atomic Energy Agency visiting the Natanz uranium enrichment plant in Iran noticed that centrifuges used to enrich uranium gas were failing at an unprecedented rate. The cause was a complete mystery—apparently as much to the Iranian technicians replacing the centrifuges as to the inspectors observing them. Five months later a seemingly unrelated event occurred.
A computer security firm in Belarus was called in to troubleshoot a series of computers in Iran that were crashing and rebooting repeatedly. Stuxnet, as it came to be known, was unlike any other virus or worm that came before. How the NSA's Firmware Hacking Works and Why It's So Unsettling. One of the most shocking parts of the recently discovered spying network Equation Group is its mysterious module designed to reprogram or reflash a computer hard drive’s firmware with malicious code.
The Kaspersky researchers who uncovered this said its ability to subvert hard drive firmware—the guts of any computer—“surpasses anything else” they had ever seen. The hacking tool, believed to be a product of the NSA, is significant because subverting the firmware gives the attackers God-like control of the system in a way that is stealthy and persistent even through software updates. The module, named “nls_933w.dll”, is the first of its kind found in the wild and is used with both the EquationDrug and GrayFish spy platforms Kaspersky uncovered. It also has another capability: to create invisible storage space on the hard drive to hide data stolen from the system so the attackers can retrieve it later.
Hacking and Security Articles / Tutorials / White Papers at HellBound Hackers. The Best Hacking Tutorial Sites - Learn Legal Hacking - StumbleUpon. Hacking. The Ethical Hacker Network. How to Hack: Ethical Hacking and Cyber Security. Top 10 Web hacking techniques of 2010 revealed. Network World - A Web hack that can endanger online banking transactions is ranked the No. 1 new Web hacking technique for 2010 in a top 10 list selected by a panel of experts and open voting.

Called the Padding Oracle Crypto Attack, the hack takes advantage of how Microsoft's Web framework ASP.NET protects AES encryption cookies. FROM THE SECURITY WORLD: Quirky moments at Black Hat DC 2011 If encryption data in the cookie has been changed, the way ASP.NET handles it results in the application leaking some information about how to decrypt the traffic. With enough repeated changes and leaked information, the hacker can deduce which possible bytes can be eliminated from the encryption key.
Hack This Site! Kali Linux "NetHunter" — Turn Your Android Device into Hacking Weapons. The developers of one of the most advance open source operating system for penetration testing, 'KALI Linux' have announced yesterday the release of a new Kali project, known as NetHunter, that runs on a Google Nexus device.
Kali Linux is an open source Debian-based operating system for penetration testing and forensics, which is maintained and funded by Offensive Security, a provider of world-class information security training and penetration testing services. It comes wrapped with a collection of penetration testing and network monitoring tools used for testing of software privacy and security. After making its influence in hacker and security circles, Kali Linux has now been published with Kali Nethunter, a version of the security suite for Android devices. The tool is a mobile distribution designed to compromise systems via USB when installed and run on an Android phone. How To Use Google Chrome For Hacking? Up till now, firefox was widely used by hackers and pentesters for their day to day job due to tremendous plugins that would make their work much easier for them.
However now a days i prefer google chrome more than firefox, due to wide variety of interesting extensions that may provide a great aid in hacking and pentration testing. Their are lots and lots of google chrome extension that can be used for hacking, however i have complied a list of my favorite ones, which i use frequently in order to test different types of web applications for security vulnerabilities. How To Use Google Chrome For Hacking - Extensions XSS Rays Xss rays would certainly be at the top of my list, XSS rays includes a scanner, XSS reverser and a DOM inspection tool. Although it does makes the browser a bit unstable when you are performing heavy scans, However it's really handy in detecting XSS attacks. XSS Rays is a security tool to help pen test large web sites.