

Tools.ietf.org/rfc/rfc5180.txt. The Systems Engineer organized chaos: Arista is recognized as one of the main data center networking vendor. 50+ Open Source Performance Testing Tools. Performance testing is a general term used to describe testing activities where a simulated user load is directed at a system and measurements are gathered. It is designed to meet or exceed a set of system performance goals while maintaining a particular user load profile. It places variable load – from a minimum to a maximum – on the system. The variable load demonstrates what the system can sustain without running out of resource or having transactions perform in a less-than-optimal fashion. Performance testing is a suite of testing that can consists of, but is not limited to, Benchmark Testing, Load Testing, Durability Testing, Volume Testing, Stress Testing, and Scalability Testing.
In some cases a separate Performance Test Plan will be created to explain the details of the Performance Testing effort. NOTE: Transactions above refer to “logical business transactions.” Below are some open source/free tools that can help you with performance testing the application under test (AUT). DNS for Rocket Scientists - Contents. This Open Source Guide is about DNS and (mostly) BIND 9.x on Linux (Fedora Core), BSD's (FreeBSD, OpenBSD and NetBSD) and Windows (Windows 7 and 10).

It is meant for newbies, Rocket Scientist wannabees and anyone in between. This Guide was born out of our first attempts a number of years ago at trying to install a much needed DNS service on an early Redhat Linux system. Protocol Overhead. How fast can you really go using a given media and protocol stack?

We examine how much bandwidth is left for applications. Ethernet Ethernet frame format: 6 byte dest addr 6 byte src addr [4 byte optional 802.1q VLAN Tag] 2 byte length/type 46-1500 byte data (payload) 4 byte CRC An excellent source of ethernet information is Charles Spurgeon's Ethernet Web Site. Notes: IP Packet Overhead. By Richard Hay What does it cost for transport?

This question can be applied to moving goods and delivering services across distances. King Hussein of flew to so he could have his heart operation performed at Johns Hopkins. People will pay to ship expensive Ferrari Enzo super sports cars from to . Similarly, there are costs associated with transporting IP packets. TCP/IP Protocol Sequence Diagrams. 3 way handshake, TCP Three-way handshake, TCP Synchronization. In this lesson, you will learn how two TCP devices synchronize using three way handshake (3 way handshake) and what are the three steps of a TCP three way handshake and how two TCP devices synchronize.
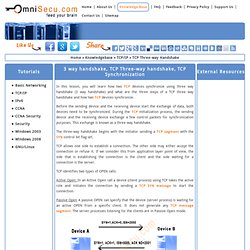
Before the sending device and the receiving device start the exchange of data, both devices need to be synchronized. During the TCP initialization process, the sending device and the receiving device exchange a few control packets for synchronization purposes. TCP Tune. System Specific Notes for System Administrators (and Privileged Users) These notes are intended to help users and system administrators maximize TCP/IP performance on their computer systems.
They summarize all of the end-system (computer system) network tuning issues including a tutorial on TCP tuning, easy configuration checks for non-experts, and a repository of operating system specific instructions for getting the best possible network performance on these platforms. A tcpdump Primer. Ngrep - network grep. Top 10 Wireshark Filters (by Chris Greer) Author Profile - Chris Greer is a Network Analyst for Packet Pioneer.
Chris has many years of experience in analyzing and troubleshooting networks. He regularly assists companies in tracking down the source of network and application performance problems using a variety of protocol analysis and monitoring tools including Wireshark. When he isn’t hunting down problems at the packet level, he can be found teaching various analysis workshops at Interop and other industry trade shows.
Packet Captures. Showing 1 - 25 of 166 nf9-juniper-vmx.pcapng.cap 912 bytes Submitted Dec 10, 2016 by Jb93 Juniper vMX NetFlow. arp_pcap.pcapng.cap 2.2 KB Submitted Mar 11, 2016 by Ashay.
SampleCaptures. Sample Captures So you're at home tonight, having just installed Wireshark.
You want to take the program for a test drive. But your home LAN doesn't have any interesting or exotic packets on it? Here's some goodies to try. Please note that if for some reason your version of Wireshark doesn't have zlib support, you'll have to gunzip any file with a .gz extension. Markofu/pcaps. Traces - SimpleWiki. From this location you can download several traces, including anonymized packet headers (tcpdump/libcap), Netflow version 5 data, a labeled dataset for intrusion detection, and Dropbox traffic traces.
More information on the data collection and on the anonymization procedures can be found below. When using these traces, please refer to the Acceptable Use policy. Cloud Storage Benchmarks You can download from this link the software and data presented in: "Benchmarking Personal Cloud Storage" by Idilio Drago, Enrico Bocchi, Marco Mellia, Herman Slatman and Aiko Pras. Dropbox Traffic Traces You can download from this page the flow data used in the following paper: Download Packet Files. PCAP files from the US National CyberWatch Mid-Atlantic Collegiate Cyber Defense Competition (MACCDC) The U.S.

National CyberWatch Mid-Atlantic Collegiate Cyber Defense Competition (MACCDC) is a unique experience for college and university students to test their cybersecurity knowledge and skills in a competitive environment. The MACCDC takes great pride in being one of the premier events of this type in the United States. While similar to other cyber defense competitions in many aspects, the MA CCDC, as part of the National CCDC, is unique in that it focuses on the operational aspects of managing and protecting an existing network infrastructure. The teams are physically co-located in the same building. Each team is given physically identical computer configurations at the start of the competition. MACCDC official website: TCPDUMP/LIBPCAP public repository. Netsniff-ng toolkit. Technical stuff. InetDaemon.Com. FrameIP, A site for IP specialists - TcpIp - Voip - Vpn - IPv4 - IPv6.
Cisco IOS CLI Shortcuts. Free Resources. SNMP MIB Search & Download. WLAN Book. Tech Stuff.