

The state of Android updates: Who’s fast, who’s slow, and why. New mobe market data finds Android, Android, über alles. Build a business case: developing custom apps Android runs on 84.7 per cent of the 301 million mobile phones the world created in the second quarter of 2014, according to market-watcher IDC.
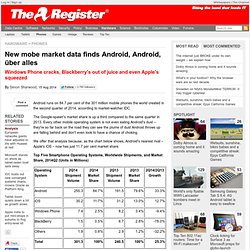
The Google-spawn's market share is up a third compared to the same quarter in 2013. Every other mobile operating system is not even eating Android's dust – they're so far back on the road they can see the plume of dust Android throws up are falling behind and don't even look to have a chance of choking. We offer that analysis because, as the chart below shows, Android's nearest rival – Apple's iOS – now has just 11.7 per cent market share.
Security. Towelroot, how to root a Android devices with a click. The popular hacker George Hotz, also known as Geohot, has designed a root tool called Towelroot that will let most Android smartphones users to root their device without a particular effort and technical knowledge.
Just one click in in fact allows Android users to root their devices, and this is possible because they run an unpatched version of the Linux kernel. George Hotz is the expert that hacker the PlayStation 3 and for this reason he being sued by Sony, Geohot is also known for unlocking, with his the limera1n jailbreak tool, the iPhone and use the mobile with any wireless carriers Geohot for his Towelroot application has exploited the vulnerability (CVE-2014-3153) which was recently disclosed by another popular hacker Pinkie Pie. The hack is possible because most versions of Android devices are based on the Linux kernel version 3.14.5, let’s remind that the flaw could be exploited by hackers to potentially acquire root access on vulnerable device. Multiple user accounts coming to Android phones 'n' slabs.
Boost IT visibility and business value It looks like user accounts are coming to Android.
This thread in the Android developer preview mailing list includes a post in which a user asks (with spelling and punctuation anomalies) for a feature the feature that behaves like this: “Tablets are able to have multiple accounts for multiple users, allowing the users to install an app only for themselfes . Storage space of phones is growing, 32GB or even 64GB. For example, some families are sharing their phones with their kids for gaming. That suggestion prompts a response from an Android development project team member to the effect that “The development team has implemented this feature and it will be available as a part of the next public build.”
Accounts with different levels of user privilege are a time-honoured way of controlling the resources users can access, so there's nothing new in this feature coming to Android. Android 5.0 Lollipop, thoroughly reviewed. Android updates don't matter anymore—or at least that's what many people think.
Back-to-back-to-back Jelly Bean releases and a KitKat release seemed to only polish what already existed. When Google took the wraps off of "Android L" at Google I/O, though, it was clear that this release was different. Android 5.0 Lollipop is at least the biggest update since Android 4.0, and it's probably the biggest Android release ever. The update brings a complete visual overhaul of every app, with a beautiful new design language called "Material Design. " How to Turn Off Safe Mode on Android. Installing Burp's CA Certificate in an Android Device. On your computer with Burp running, visit in and click the "CA Certificate" link.
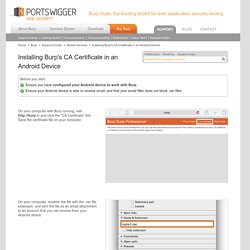
Save the certificate file on your computer. On your computer, rename the file with the .cer file extension, and sent the file as an email attachment to an account that you can access from your Android device. Check your email on the Android device. Open the email and tap the attachments button. Then tap the save button. Find your “My Files” folder. Configuring your Browser to work with Burp.
Burp is designed to be used alongside your browser.
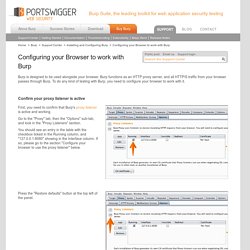
Burp functions as an HTTP proxy server, and all HTTP/S traffic from your browser passes through Burp. To do any kind of testing with Burp, you need to configure your browser to work with it. Confirm your proxy listener is active. Android has some critical remotely-exploitable security holes. But can you get the patch? On Monday, Google released the latest security update for Nexus devices running Android, as part of its previously announced plan to roll-out over-the-air patches on a monthly basis.
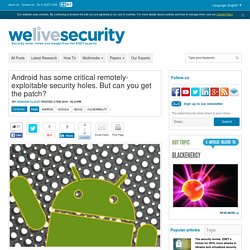
The most serious flaws, given a severity rating of critical, could lead to remote code execution – with malicious hackers running code on your device, without your permission or knowledge, without needing physical access. For instance, the bug in Mediaserver could mean that simply opening an email, browsing a website or receiving a media file via MMS could mean that in the blink of an eye, malicious code is being run on your Android device.
Yes, even smart TVs can be hit by Android ransomware. Researchers are actively tracking a ransomware family whose variants can infect all Android devices, including smart TVs.
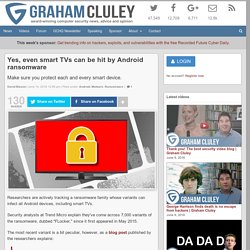
Security analysts at Trend Micro explain they've come across 7,000 variants of the ransomware, dubbed "FLocker," since it first appeared in May 2015. The most recent variant is a bit peculiar, however, as a blog post published by the researchers explains: "The latest variant of FLocker is a police Trojan that pretends to be US Cyber Police or another law enforcement agency, and it accuses potential victims of crimes they didn’t commit. Critical Vulnerability Breaks Android Full Disk Encryption. Most Android Devices Susceptible to Full Device Encryption Bypass A Critical Elevation of Privilege (EoP) vulnerability that affects the majority of Android devices allows an attacker to bypass the Full Device Encryption (FDE) security feature that Google implemented in Android 5.0 Lollipop, researchers discovered.
The security flaw, tracked as CVE-2016-2431, was reported in October 2015, but Google patched it only in May 2016. The issue resides in the Qualcomm Secure Execution Environment (QSEE), a Linux kernel device designed to allow communication between the normal Android operating system and the secure OS that manages protected services and hardware. The issue was discovered by Gal Beniamini, an independent Israeli researcher who previously detailed an EoP vulnerability in the Widevine QSEE TrustZone application. “Full disk encryption is used world-wide, and can sometimes be instrumental to ensuring the privacy of people's most intimate pieces of information. The Android Ransomware Threat has Quadrupled in Just One Year. If you need any more evidence that ransomware has become a major problem, just look at how online criminals are busily developing attacks against platforms other than Windows.
Yes, Windows continues to be the operating system most commonly targeted with ransomware threats – but malware that attempts to extort money out of you is also being actively developed for Android, OS X, and Linux. More mobe malware creeps into Google Play – this time, ransomware. Researchers say a piece of ransomware disguised as a battery app made its way into the Play store. Check Point says one of its customers contracted the malware app, dubbed "Charger," after installing what they thought was a battery monitoring tool called EnergyRescue. Researchers with Check Point Mobile Threat Prevention say the malware activates when EnergyRescue runs, and requires admin access to the device.
Once that permission is granted, the malware checks for location (it does not attack phones in the Ukraine, Belarus, or Russia), then swipes all user contacts and SMS messages and locks down the device.