

Dashboard - ANY.RUN. InstaRecon - Automated Subdomain Discovery Tool. Blog >> Interested in privacy enhancing technology? How to get involved at Open Whisper Systems. If you’re interested in the project, here are some ways to help out Open Whisper Systems: Use the software and provide feedback.
One of the best ways to help is by providing valuable user feedback. Install TextSecure or RedPhone and file bugs you encounter or features you feel are missing on the issue tracker.Help spread the word! Tell a friend.Translate to non-English languages. Black Markets: An Abuse Fighter’s Oracle of Delphi – In the Wyrd. Specialization within the underground hinges on open communication between criminals who advertise goods and services as well as potential buyers.

Forums, chats, storefronts, and freelance labor pages all streamline abuse, but as a consequence expose the broad range of criminal activities to researchers at large. This creates an opportunity for anti-abuse teams to tap into black markets as both a technique for acquiring datasets of bleeding edge threats as well as an early warning system for failing systems. Web services attempt to rate limit the torrent of automatically generated accounts through CAPTCHAs, email verification, and most recently phone verification. While CAPTCHAs and email accounts are trivially available from the underground for relatively low prices, ideally phone numbers represent a scarce resource for criminals that are otherwise globally accessible to legitimate users. Price of phone verified accounts for various services as advertised on the black market.
Hijacking Koobface’s Captcha Solver – In the Wyrd. One of the interesting challenges of propagating malware through social media is the requirement of obtaining new accounts for spamming.

The Koobface botnet automates this process by leveraging zombies to sign up for accounts on Facebook, Gmail, Blogger, and Google Reader. Each of these services requires a solution to a Captcha challenge which Koobface pushes off on a zombie machine’s owner to solve. During the course of infection, a Koobface zombie will repeatedly poll the C&C for Captchas requiring solutions, in turn prompting users with a threat to shutdown unless the Captcha is solved. Security Fix - The Scrap Value of a Hacked PC. Computer users often dismiss Internet security best practices because they find them inconvenient, or because they think the rules don't apply to them.
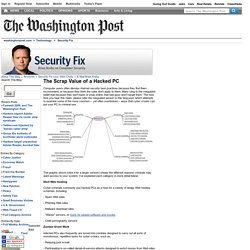
Many cling to the misguided belief that because they don't bank or shop online, that bad guys won't target them. The next time you hear this claim, please refer the misguided person to this blog post, which attempts to examine some of the more common -- yet often overlooked -- ways that cyber crooks can put your PC to criminal use. The graphic above (click it for a larger version) shows the different reasons criminals may want access to your system. I've explained each category in more detail below: The Scrap Value of a Hacked PC, Revisited. A few years back, when I was a reporter at The Washington Post, I put together a chart listing the various ways that miscreants can monetize hacked PCs.

The project was designed to explain simply and visually to the sort of computer user who can’t begin to fathom why miscreants would want to hack into his PC. “I don’t bank online, I don’t store sensitive information on my machine! I only use it to check email. What could hackers possibly want with this hunk of junk? -=HackInfo=- LIFE HACKS INSTITUTE OF HACKING 2. Creating and Curating Your Digital Professional Learning Network. Hello, hackers!

Do you have a digital PLN? If not, this post will explain the concept and share some tips for success. I discovered the concept of the digital PLN (a web-based personal or professional learning network) through an information literacy instruction class I took in Fall 2013. One of the major class projects was to select and curate digital resources to facilitate our lifelong learning as librarians, according to our career goals. What is a PLN? A traditional PLN consists of actual people with whom you have collaborated or shared ideas. Why should I have a PLN? Hacking I Cybersécurité I Privacité I Hacktivism.
Exploits and Security Tools Framework: EaST Framework. CyberPunk » Exploitation Tools Pentest framework environment is the basis of IT security specialist’s toolkit.

This software is essential as for learning and improving of knowledge in IT systems attacks and for inspections and proactive protection. The need of native comprehensive open source pen test framework with high level of trust existed for a long time. Backdoor Android APK: backdoor-apk. Backdoor-apk is a shell script that simplifies the process of adding a backdoor to any Android APK file.
Users of this shell script should have working knowledge of Linux, Bash, Metasploit, Apktool, the Android SDK, smali, etc. This shell script is provided as-is without warranty of any kind and is intended for educational purposes only. Usage: root@kali:~/Android/evol-lab/BaiduBrowserRat# . The recompiled APK will be found in the ‘original/dist’ directory.
Onion Services Security Scan: OnionScan. The purpose OnionScan is to make you a better onion service provider.
You owe it to yourself and your users to ensure that attackers cannot easily deanonymize your service. Looking at dark web markets where people buy and sell drugs, fake IDs, and other illegal content one would expect that these sites have a strong interest in maintaining top-level security. However, often many of the issues that are or can be problematic on the surface web are prevalent throughout the dark web too.
While a hidden service within Tor is not vulnerable in the way a regular website is, the operators can still make mistakes. Security Intelligence Collector: Machinae. Machinae is a tool for collecting intelligence from public sites/feeds about various security-related pieces of data: IP addresses, domain names, URLs, email addresses, file hashes and SSL fingerprints.

It was inspired by Automater, another excellent tool for collecting information. The Machinae project was born from wishing to improve Automater in 4 areas: Codebase – Bring Automater to python3 compatibility while making the code more pythonicConfiguration – Use a more human readable configuration format (YAML)Inputs – Support JSON parsing out-of-the-box without the need to write regular expressions, but still support regex scraping when neededOutputs – Support additional output types, including JSON, while making extraneous output optional. Google Tips, Tricks & Hacks. From Responder To Credentials: Gladius. Gladius provides an automated method for cracking credentials from various sources during an engagement.
It can currently crack hashes from Responder, secretsdump.py, and smart_hashdump. The usefulness of Gladius is that any sort of file driven event can be captured and triggered. By default, it comes prepackaged with three types of events: Watching for files that match *NTLM* from Responder in Responder’s default directory on Kali:/usr/share/responderWatching for files that match *hashdump* from Metasploit’s smart_hashdump module in/root/.msf*/lootWatching for files that match *secretsdump* from CoreSecurity’s secretsdump.py also in Responder’s default directory What this means, is that once it is started, all one has to do is perform a smart_hashdump in metasploit or pipe the output from secretsdump.py into /usr/share/responder, and the resulting hashes are automatically passed to hashcat to begin cracking. Automatic Local Privilege Escalation Script. CyberPunk » Exploitation Tools An automated script which downloads potential Linux kernel exploits from exploitdb, and compiles them automatically Automatic Local Privilege Escalation Script searches exploitdb and will try to find the latest and applicable Linux privilege escalation exploits for the active kernel version.
It does that by using searchsploit. Auto Backdooring Utility: backdoorme. Backdoorme is a powerful utility capable of backdooring Unix machines with a slew of backdoors. Backdoorme uses a familiar metasploit interface with tremendous extensibility.Backdoorme relies on having an existing SSH connection or credentials to the victim, through which it will transfer and deploy any backdoors. Please only use Backdoorme with explicit permission. Backdoorme comes with a number of built-in backdoors, modules, and auxiliary modules. Backdoors are specific components to create and deploy a specific backdoor, such as a netcat backdoor or msfvenom backdoor. Modules can be applied to any backdoor, and are used to make backdoors more potent, stealthy, or more readily tripped. To start backdoorme, first ensure that you have the required dependencies. $ python dependencies.py.
Deep Spying. Spying using Smartwatch and Deep Learning Wearable technologies are today on the rise, becoming more common and broadly available to mainstream users. In fact, wristband and armband devices such as smartwatches and fitness trackers already took an important place in the consumer electronics market and are becoming ubiquitous. By their very nature of being wearable, these devices, however, provide a new pervasive attack surface threatening users privacy, among others. In the meantime, advances in machine learning are providing unprecedented possibilities to process complex data efficiently. Firmware Analysis Tool: Binwalk. Binwalk is a fast, easy to use tool for analyzing and extracting firmware images Firmware Analysis Tool Binwalk supports Python 2.7 – 3.x.
Although most systems have Python2.7 set as their default Python interpreter, binwalk does run faster in Python3. Installation. Opensource RAT: Pupy. CyberPunk » Maintaining Access. Web Pen-Test Practice Application: OWASP Mutillidae. Mutillidae can be installed on Linux and Windows using LAMP, WAMP, and XAMMP for users who do not want to administrate a webserver. It is pre-installed on SamuraiWTF, Rapid7 Metasploitable-2, and OWASP BWA. Chrome Keylogger Extension: ChromeLogger. A keylogger and form grabber for Google Chrome that runs as an extension ChromeLogger is a keylogger and form grabber that runs as a Google Chrome extension. Since it’s a Chrome addon, it’s compatible with the latest version of Chrome on all OS’s (Windows, Mac, Linux).
Distributed Password Cracking: CrackLord. Over the past several years the world of password cracking has exploded with new tools and techniques. These new techniques have made it easier than ever to reverse captured password hashes. With the addition of powerful techniques, from GPGPU cracking to rainbow tables, it is easier than ever to access the plaintext for fun and profit. Furthermore, during our day jobs we have found that many other processes can benefit from distributed access to the resources of high powered systems.
With many people requesting access to this, CrackLord was born. Ransomware Crypter Kit: eda2. Appie – Android Pentesting Portable Integrated Environment. Automatically Brute Force All Services - BruteX. CyberPunk » Password Attacks. Automates Vulnerability Scanning: Seccubus. Seccubus automates regular vulnerability scans with vrious tools and aids security people in the fast analysis of its output, both on the first scan and on repeated scans. Awesome Windows Exploitation Resources. Fast Parallel Login Brute-forcer: Medusa. Medusa is intended to be a speedy, massively parallel, modular, login brute-forcer Medusa 2.2 (Release Candidate 2) Released Medusa 2.2 will be the first release in over three years.
While there are no major changes to the core of the application, it does include many bug-fixes throughout the code base and numerous incremental improvements. Samurai - The Web Testing Security Framework. Phishing Campaign Toolkit: King Phisher. King Phisher is a tool for testing and promoting user awareness by simulating real world phishing attacks. Pentesting Distribution for Wireless Security: Xiaopan OS. The Social-Engineer Toolkit: SET. Integrated Penetration-Test Environment: Faraday. MITMf - Man-In-The-Middle Attack Framework. Black-Box CAN Network Analysis Framework: CANToolz. Open Source GPS Tracking System: Traccar. Rogue WiFi Access Point Attack: WiFi-Pumpkin. Adventures of an apprentice. InfoSec Resources - IT Security Training & Resources by InfoSec Institute. Nobody Can Stop Information Insemination.
Exploit.IN. Malware Analysis: The Final Frontier. Database. Malware URL. NoThink! Open Malware. Malware - Clean MX - realtime. Buster Sandbox Analyzer. Sandboxes / Online Link checkers. List of Malware Sources. Index page. Antionline Forums - Maximum Security for a Connected World. Internet Storm Center - Internet Security. Open Threat Exchange (OTX) Security-Onion-Solutions/security-onion. GrayHat Hacking Security Exploits : How To Use MetaGooFil.
Penetration Testing Tools. Edge-security group. Operator « US System Administration. PythonHackers Community. Parrot Security OS. Kali Linux NetHunter - Kali NetHunter. Hacker 10 - Security Hacker. World Best Hacking & Cracking Forum! ANTICHAT.RU - ANTICHAT.RF. Legit carding forum. Carding Forum. Hack Forums. Writing a stealth web shell - Just Another Hacker. Security Tools & Info. Ethical Hacking. WiFinspect. Start - netsec. DarkComet RAT Official Website. Let them Find us. Resources. How to Become an Ethical Hacker. Welcome to SecurityTube.net. Zone-H.org - Unrestricted information. Pastebin password list. Reverse Engineering. HackRead – Latest Cyber Crime – Information Security – Hacking News. Cryptography. Hacking. Zeroday : Weaponizing code. Blackhat academy: "ok guys so _hypothetically_..."
Things: We'll be doing them again soon! DEF CON® Hacking Conference - Archive of Hacking Tools Released at DEFCON. About Darknet. SecTools.Org Top Network Security Tools. Top 15 Security/Hacking Tools and Utilities. Cheating Network.
How to phish(tutorial inside) Wonder How To » Show & Tell for Creators & Doers. Black Hat ® Technical Security Conference: USA 2010 // Archives. Blackbuntu Linux - Penetration Testing Distribution.