

Emily Lauren
My name is Emily Lauren and I work as Malware Breach Analyst at Comodo. I know the better way of handling malware breaches that happens at point of sale system.
How to alleviate Data Breaches in Enterprise Environment - Welcome - ilearn-lr-blog. Data breaches are rather common these days.

We hear of data breaches- small, big and massively big- happening every now and then. Companies today invest on security like never before because the damages caused by data breaches sometimes tend to be really huge; this includes financial losses as well. Well, what all needs to be done to prevent data breaches or alleviate the damages. There are many vital things to be taken care of. Let's take a look at some of the major security steps that could help in this regard... Have a data security plan in place - It's always advisable to have a data security plan in place. Encrypt sensitive data - It's always good to go for encryption.
Manage data access - All access of data plus any alterations made as regards data must be logged and these logs need to be audited on a regular basis (weekly or so). Delete old, outdated data - Expiring data is always good. Have good endpoint protection system - Have a good endpoint protection system in place. Improve Data Security with POS Security at Point of Sale Terminal.
Compatible With Micros Point of Sales System. Whoops!
There was a problem with your input. Please check: Error – The wage for hours must be between 12 and 50. Error – The hours spent scheduling should be fewer than 999 hours. Error – The hours spent on H.R. tasks should be fewer than 999 hours. A Point of Sale Software Mobile Device for Retail Businesses. Whoops!
There was a problem with your input. Please check: Error – The wage for hours must be between 12 and 50. Improve Staff Performance Using Free POS Reporting Software. Whoops!
There was a problem with your input. Please check: Error – The wage for hours must be between 12 and 50. Tableside Tablets Compatible with Restaurant POS Reporting Software. Whoops!
There was a problem with your input. Please check: Error – The wage for hours must be between 12 and 50. Error – The hours spent scheduling should be fewer than 999 hours. Error – The hours spent on H.R. tasks should be fewer than 999 hours. Improve Data Accuracy and Strengthen Processes in the Restaurant Industry Using a POS Software. Whoops!
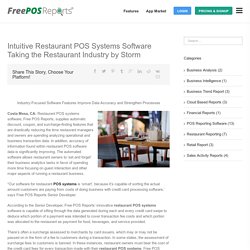
There was a problem with your input. Please check: Error – The wage for hours must be between 12 and 50. Error – The hours spent scheduling should be fewer than 999 hours. Error – The hours spent on H.R. tasks should be fewer than 999 hours. Trend Report Helps You to Revel Your Business Data. Whoops!
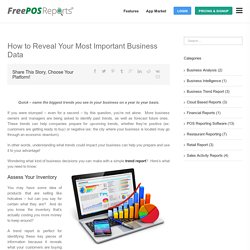
There was a problem with your input. Please check: Error – The wage for hours must be between 12 and 50. Error – The hours spent scheduling should be fewer than 999 hours. Error – The hours spent on H.R. tasks should be fewer than 999 hours. The Benefits of Using a Reporting Software System. Whoops!
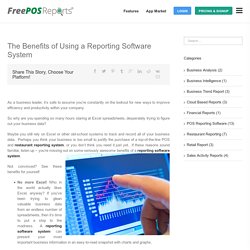
There was a problem with your input. Please check: Error – The wage for hours must be between 12 and 50. Error – The hours spent scheduling should be fewer than 999 hours. Secure your Point of Sale System Today. What is Point of Sale System?
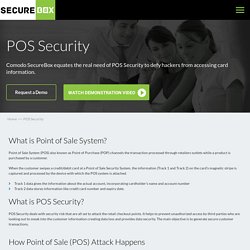
Point of Sale System (POS) also known as Point of Purchase (POP) channels the transaction processed through retailers outlets while a product is purchased by a customer. When the customer swipes a credit/debit card at a Point of Sale Security System, the information (Track 1 and Track 2) on the card's magnetic stripe is captured and processed by the device with which the POS system is attached. Track 1 data gives the information about the actual account, incorporating cardholder’s name and account number Track 2 data stores information like credit card number and expiry date.
What is POS Security? POS Security deals with security risk that are all set to attack the retail checkout points. How Point of Sale (POS) Attack Happens Cybercriminals are prying over customers data punched in through the POS systems. Normal and Infected POS System Securebox Solution for POS Security - An Epitome to Secure Point of Sale Network.