

David Hughes
Thesp0nge/ciphersurfer - GitHub. Cyber War. Feature Column from the AMS. In this article, I'll just describe how to unpack the simplest outermost level of security...
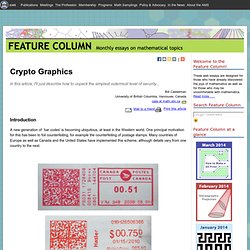
Introduction A new generation of `bar codes' is becoming ubiquitous, at least in the Western world. One principal motivation for this has been to foil counterfeiting, for example the counterfeiting of postage stamps. Many countries of Europe as well as Canada and the United States have implemented this scheme, although details vary from one country to the next. In the near future, all pharmaceutical products sold in Europe will require similar authentication. In addition, correspondence from the IRS frequently includes data matrices but here, too, the purpose is not known to me. Data matrices are not actually bar codes, which are one-dimensional. Assembling the bytes Every data matrix encodes an array of bytes, which may roughly be considered as the smallest interpretable units inside computers. The first question, however, is how is the array of bytes to be found? Interpreting the bytes.
50 Best Portable Apps (Windows/Mac/Linux) Do you travel very often to client place and use different computers?
If yes, then make sure your USB drive is loaded with some common tools that can make your life much easier. I have compiled a list of 50 portable tools that you can carry on your USB or flash drive. 1. Foxit PDF Reader – What if Acrobat Viewer is not installed on customer’s PC. Always carry Foxit reader to read PDF files. 2. 3. uTorrent – Always carry a torrent client in your flash drive. 4. 5. 6. 7. 6 Types Of Blogposts That Will Get Your Retweets Through The Roof. 461 Flares Filament.io 461 Flares × This was always the most important question for me, when I started out blogging.
It is something which took me quite a while to figure out and I am by no means at a stage where I have completely understood it. Yet, over the past months, I have seen a clear pattern here on the Buffer blog. Last week, we had a look at which Tweets get retweeted the most. So today, we will have a look at: Which Types Of Blogposts Get Retweeted The Most? Here are the 6 different typs of blogposts that have performed the best here on our blog. 1.)
The first type of posts I have seen perform extraordinarily well here on the Buffer blog are actionable list posts. If you and I see such a list post, we know that we can quickly browse through each of the Tips and see if there is anyone amongst them that could help us immediately. Here is an example post that did very well based on these factors: 5 Tips To Make Your Personal Twitter Account Stand Out 2.) You're Gonna Miss Me- Lulu and the Lampshades (Cover) Video. Log in Dame You're Gonna Miss Me- Lulu and the Lampshades (Cover) This is the best version of this song I have heard to date, it is CONSIDERABLY better than the original if you ask me.
I absolutely love her voice. posted 3 years ago © 2014 Redux, Inc. About redux | contact us | copyright | legal. Beginning Perl (free) - www.perl.org. By Simon Cozens What does this book cover?
Installing Perl on Windows and UNIX Making use of online Perl resources like CPAN First principles in programming and the Perl syntax Working with files and databases Writing web pages in Perl Using Perl as an object-oriented language Book overview Perl is a well-established programming language that has been developed through the time and effort of countless free software programmers into an immensely powerful tool that can be used on pratically every operating system in the world. Perl started out as the "Swiss army knife" of computer languages and was used primarily by system administrators, but over time it's grown into an immensely robust language used by web-developers and programmers worldwide.
"There's more than one way to do it" is the motto of Perl, but this book aims to take you through them all. PirateBox DIY - David Darts Wiki. Portable Antivirus – Ultimate List of Best USB Anti Virus. This post is part of our "Largest List of Best Free Security Software".
Check the rest of them. Why You May Need Portable Antivirus Applications: Present day antivirus and security software operate on post-event basis. First a virus or malware is discovered, then the antivirus database is updated to include its signature, then it is expected that the user will download the antivirus update and after that only, the user is secured against that virus. But it is often too late. To further complicate the situation, present day malware often make modifications to the system files and corrupt your security software. In such a case, your only solution may to use some Portable Antivirus software, stored on a removable media like USB, Pen Drive or CD ROM, make it write protected and use it to clean your infected system. What Are Portable Antivirus Software: Portable Antivirus Software are often stripped down version of their full-featured counterparts.
Portlandia: Allergy Pride. #3038363.
Information Security.