

Flashlight apps are spying on users Android, iOS, Windows Phone smartphones, is yours on the list? Many of the top downloadable flashlight apps are accessing sensitive user data and compromising the safety of your device.
Here’s a rundown of the top offenders and what to do about it. (Photo : Google Play | Tech Times) Android apps that fail to validate SSL - Google Sheets. Popular Android Apps with SSL Certificate Validation Failure. Background CERT tested many Android apps in 2014, and notified the authors of SSL certificate validation vulnerabilities.
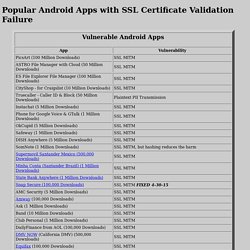
I found that "snap secure" was still vulnerable to a trivial MITM attack, and wrote a homework project for my students. I decided to test more apps on the CERT list, just to see what I could find. Here are details of the CERT test and notification, from 9/3/2014: Finding Android SSL Vulnerabilities with CERT Tapioca. Top 10 External and Internal Vulnerabilities. Windows Security: Vulnerabilities in Windows. Vulnerabilities in Windows Update Windows | Windows Alternatives | ActiveX All Windows Versions are Vulnerable Ignore Windows security at your own peril.

Beware of the Human Factor People are too trusting of any warning that appears on their computer, particularly when visiting websites with their browser. Most vulnerable operating systems and applications in 2014. See update at the end of this post An average of 19 vulnerabilities per day were reported in 2014, according to the data from the National Vulnerability Database (NVD).
The NVD provides a comprehensive list of software security vulnerabilities. In this article, I look at some of the trends and key findings for 2014 based on the NVD’s database. Some of the questions asked are: Heartbleed Bug. The 10 most common Windows security vulnerabilities. We all know that Windows-based systems have plenty of potential security risks.
But are your systems vulnerable? Likely so. Any given network is chock full of Windows vulnerabilities. It's a law of nature and a side effect of doing business using networked computers. Every Version of Windows Is Affected By This Vulnerability - What You Can Do About It. What would you say if we told you that your version of Windows is affected by a vulnerability that dates back to 1997?
You’d laugh, right? Surely, after all, Microsoft would have patched the fault prior to releasing Windows 98, or at the latest, Windows 2000? Top 10 Windows Vulnerabilities. By understanding Windows based vulnerabilities, organizations can stay a step ahead and ensure information availability, integrity, and confidentiality.
Listed below are the Top 10 Windows Vulnerabilities: Web Servers - misconfigurations, product bugs, default installations, and third-party products such as php can introduce vulnerabilities. Microsoft SQL Server - vulnerabilities allow remote attackers to obtain sensitive information, alter database content, and compromise SQL servers and server hosts. Passwords - user accounts may have weak, nonexistent, or unprotected passwords.