

Network traffic analysis. Master-Key Cryptosytems. Decrypting TLS Browser Traffic With Wireshark – The Easy Way! Intro Most IT people are somewhat familiar with Wireshark.
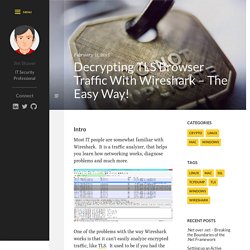
It is a traffic analyzer, that helps you learn how networking works, diagnose problems and much more. One of the problems with the way Wireshark works is that it can’t easily analyze encrypted traffic, like TLS. It used to be if you had the private key(s) you could feed them into Wireshark and it would decrypt the traffic on the fly, but it only worked when using RSA for the key exchange mechanism.
As people have started to embrace forward secrecy this broke, as having the private key is no longer enough derive the actual session key used to decrypt the data. Session Key Logging to the Rescue! Well my friends I’m here to tell you that there is an easier way! Setting up our Browsers We need to set an environmental variable. On Windows: Go into your computer properties, then click “Advance system settings” then “Environment Variables…” On Linux or Mac OS X: You can also add this to the last line of your on Linux, or.
Ssldump – An SSL/TLS network protocol analyzer. Sponsored Link ssldump is an SSL/TLS network protocol analyzer.
It identifies TCP connections on the chosen network interface and attempts to interpret them as SSL/TLS traffic. When it identifies SSL/TLS traffic, it decodes the records and displays them in a textual form to stdout. If provided with the appropriate keying material, it will also decrypt the connections and display the application data traffic. ssldump has been tested on FreeBSD, Linux, Solaris, and HP/UX.
How to Decrypt SSL and TLS Traffic Using Wireshark. Warning — Popular 'Hot Patching' Technique Puts iOS Users At Risk. Do you know?
… Any iOS app downloaded from Apple’s official App Store has an ability to update itself from any 3rd-party server automatically without your knowledge. Yes, it is possible, and you could end up downloading malware on your iPhone or iPad. Unlike Google, Apple has made remarkable efforts to create and maintain a healthy and clean ecosystem of its official App Store. Top 10 Password Crackers. SecTools.Org: Top 125 Network Security Tools For more than a decade, the Nmap Project has been cataloguing the network security community's favorite tools.
In 2011 this site became much more dynamic, offering ratings, reviews, searching, sorting, and a new tool suggestion form . Introduction to Hacking. Let’s Encrypt Brings Free HTTPS to the World: 2015 in Review. When we look back at 2015, we will remember this as the year we launched our most ambitious technology project to date.
EFF, Mozilla, and our partners gave the world the Let's Encrypt certificate authority. Certificates became available to the public on December 3. Let's Encrypt makes getting a digital certificate for an Internet site fast, free, and easy, so sites can easily enable HTTPS encryption (and some other encrypted protocols). We think this is a vital step in getting Web connections routinely encrypted, by reducing the cost and difficulty of getting a certificate that browsers require when making secure connections.
We know online encryption is essential. So for the past three years, EFF and our partners from Mozilla and the University of Michigan, plus a range of sponsors, pursued a plan to automate the process, removing financial cost and technical challenge. The World of IT & Cyber Security: ehacking.net. Security_wk_3.docx - Microsoft Word Online. Norse - Live Attack Intelligence. Traditional signature- and policy-based network security systems are reactive and often rely on incomplete data that is not up to date.

As the effectiveness of these solutions continues to decline, organizations are being exposed to increased risk of security breaches, data exfiltration, loss of reputation and revenue from today's advanced cyber threats. Norse DarkViking™ is a patented SaaS service that gathers "dark intelligence" from the parts of the Internet where bad actors operate and delivers an actionable risk score that enables organizations to drastically increase their overall security posture.
DarkViking delivers machine-readable threat intelligence (MRTI) that can be integrated with an organization's existing security products and network devices. Through a flexible RESTful API or direct solution level integration, DarkViking improves existing security solutions' ability to detect and block today's cyber threats and advanced malware before they enter the network. Equation Group: Meet the NSA 'gods of cyber espionage' Over the last couple of years we have been hearing about ever more sophisticated pieces of malware.

From Stuxnet and Flame to Gauss and most recently Regin, all have shown increasing levels of technical prowess and all have been linked in some way with the US government. These were thought to be the pinnacle of a huge investment in offensive cyber capabilities by the world's wealthiest country. That was, until we learned about Equation. Described by Kaspersky Lab, the Moscow-based security company which uncovered it, as "an almost omnipotent cyberespionage organisation", the group has been called the "God of cyberespionage" and may have been operating undetected for almost two decades.
While Kaspersky's report reveals much about the group, it barely touches the surface of the capabilities of what is likely the most highly-prized jewel in the NSA's cyberespionage crown. Security War Games. Information security keeps evolving, but our educational methods are not evolving rapidly enough to win the cold cyberwar.

Top 50 Hacking Tools That You Must Have. Whether you are a Penetration tester, a hacker or an aspiring newbie trying to learn Cyber Security, you must have a nice catalogue of tools to make your life easier.
While these tools do make working simpler but cannot compensate for the vast amount of knowledge required in this field. Top 50 Hacking Tools That You Must Have. 10-more-hacking-and-security-software. Ettercap is a console-based network sniffer/interceptor/logger that is capable of intercepting traffic on a network segment, capturing passwords, and conducting active eavesdropping against a number of common protocols. Ettercap supports active and passive dissection of many protocols (including ciphered ones) and provides many features for network and host analysis. Ettercap also has the ability to actively or passively find other poisoners on the LAN. * Nikto Nikto is a web server scanner that is known to perform comprehensive tests against web servers for multiple items, including over 3500 potentially dangerous files/CGIs, versions on over 900 servers, and version specific problems on over 250 servers.
It performs generic and server type specific checks. . * OpenSSH OpenSSH is a Free and Open Source version of the SSH connectivity tools providing encrypted communication sessions over a computer network. Forensics & Investigations. Net cat. Sniffers. Go Deep. Lists of reserved ports, ICMP types and codes, and Internet protocols. Security.