

DarkReading. DarkReading. Bring-your-own-network phenomenon complicates security in bring-your-own-device environments [Jason Sachowski is a security professional at ScotiaBank.
His content is contributed through the auspices of the (ISC)2 Executive Writers Bureau.] Most security professionals are wrestling with the bring-your-own-device (BYOD) phenomenon, in which end users introduce their own mobile devices -- and a new range of security risks -- to the corporate network. Increasingly, however, the BYOD security environment is further complicated by another emerging phenomonon: bring your own network (BYON). The BYON security problem is a by-product of increasingly common technology that enables users to create their own mobile networks. Like BYOD, the BYON security issue is not solved simply through point solutions.
6 Password Security Essentials For Developers. Use of Cloud Most Common Among Small Firms, ABA Survey Says. Are social media e-discovery's next nightmare? - legal, social media, Internet-based applications and services, internet. Opinion By Barry Murphy August 20, 2012 08:43 AM ET. ZeroNights. Rogue WhatsApp Facebook apps harvest info, lead to malware. Rogue Facebook apps still occasionally pop up, even though they are not nearly as ubiquitous as they used to be.
More often than not they supposedly show users who has been viewing their profile, but these latest ones pose as legitimate WhatsApp Messenger apps. WhatsApp Messenger is a popular cross-platform instant messaging application for smartphones, and while it has a Facebook page, it does not have a Facebook app, and this lack prompted cyber crooks to fill the demand gap: "Now I’m an old man and I don’t really understand this Faceboook thing, but I’m pretty sure there aren’t supposed to be this many WhatsApp Facebook apps on its platform in the first place," says TNW's Robin Wauters, and tells about being introduced to one of those apps via a request by a Facebook friend.
SailPoint updates identity management solution IdentityIQ. Posted on 20 August 2012.

SailPoint announced the release of IdentityIQ 6.0, an enterprise-grade identity management solution that scales to support thousands of business users at a single time. New features include: 92% of the top 100 mobile apps have been hacked. Posted on 20 August 2012.
Ninety-two percent of the Top 100 paid Apple iOS apps and 100 percent of Top 100 paid Android apps have been hacked, according to a new report by Arxan Technologies. They revealed the widespread prevalence of “cracked” mobile apps and the financial impact befalling the multi-billion dollar App Economy due to compromised brands, lost revenues, IP theft, and piracy. The proliferation of mobile devices has created an app-centric global marketplace, ushering in the App Economy that is driving new business models and revenue streams across all industries. Arxan set out to analyze the extent of malicious mobile app hacking by researching hacked versions of top Apple iOS and Android apps from third-party sites outside of the Apple App Store and Google Play marketplaces. Bogus Royal Mail emails deliver malware. UK-based Internet users should be on the lookout for spoofed Royal Mail emails, as cyber crooks have decided to impersonate the institution and try to deliver malware to unsuspecting victims, warns Sophos.
The emails resemble the ones supposedly sent by delivery services, as it tries to trick the recipients into downloading and opening the file in the attachment: The email does have a veneer of legitimacy as the criminals used the Royal Mail logo and spoofed the "From" email address to seem like the message is coming from the organization. The file in the attachment is a ZIP file and supposedly a shipping advisory, and inside it is an executable named royal_mail_shipping.exe. Your Biggest Risk: People With Good Intentions (But Bad Education) Digital Evidence & Discovery (DEAD)
Surveillance device uses Wi-Fi to see through walls. Researchers in England have created a prototype surveillance device that can be used to spy on people inside buildings and behind walls by tracking the frequency changes as Wi-Fi signals generated by wireless routers and access points bounce off people as they move around.
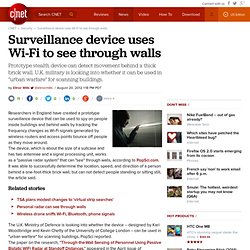
The device, which is about the size of a suitcase and has two antennae and a signal processing unit, works as a "passive radar system" that can "see" through walls, according to PopSci.com. It was able to successfully determine the location, speed, and direction of a person behind a one-foot-thick brick wall, but can not detect people standing or sitting still, the article said. The U.K. Most cyber attacks fly under our radar: Aussie spy chief.
Australia's spy chief, David Irvine, has warned businesses to be on the alert for cyber attacks and corporate espionage.
Irvine, who is the director-general of the Australian Security Intelligence Organisation (ASIO), said that many cyber attacks were going undetected by local security agencies. "I would be very surprised if we, who are active in this area, are picking up the greater proportion of it — in fact, quite the reverse," he told a business conference in Canberra on Monday. Don't Trust That Text Message: Tool Simplifies iOS SMS-Spoofing.