

Windows Firewall Pen Test (Passed 100%) Password Haystacks: How Well Hidden is Your Needle? ... and how well hidden is YOUR needle?

Every password you use can be thought of as a needle hiding in a haystack. After all searches of common passwords and dictionaries have failed, an attacker must resort to a “brute force” search – ultimately trying every possible combination of letters, numbers and then symbols until the combination you chose, is discovered. If every possible password is tried, sooner or later yours will be found. The question is: Will that be too soon . . . or enough later? This interactive brute force search space calculator allows you to experiment with password length and composition to develop an accurate and quantified sense for the safety of using passwords that can only be found through exhaustive search.
<! (The Haystack Calculator has been viewed 8,151,017 times since its publication.) IMPORTANT!!! It is NOT a “Password Strength Meter.” Since it could be easily confused for one, it is very important for you to understand what it is, and what it isn't: Okay. ShieldsUP! — Internet Vulnerability Profiling Your Internet connection's IP address is uniquely associated with the following "machine name": The string of text above is known as your Internet connection's "reverse DNS.
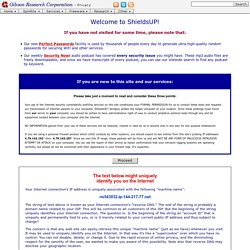
" The end of the string is probably a domain name related to your ISP. This will be common to all customers of this ISP. But the beginning of the string uniquely identifies your Internet connection. The question is: Is the beginning of the string an "account ID" that is uniquely and permanently tied to you, or is it merely related to your current public IP address and thus subject to change? The concern is that any web site can easily retrieve this unique "machine name" (just as we have) whenever you visit. If the machine name shown above is only a version of the IP address, then there is less cause for concern because the name will change as, when, and if your Internet IP changes.
There is no standard governing the format of these machine names, so this is not something we can automatically determine for you. Firewall Leakage Tester Introducing LeakTest This site has been most well-known for its FREE ShieldsUP!
Internet security test. Crucial as it is to protect yourself from malicious hackers outside, those bad guys represent only half of the threat. The Internet has proven to be an extremely fertile transportation medium for all manner of nasty Trojan horse programs, rapidly proliferating viruses, and privacy invading commercial spyware. As a result, it is no longer true that all of the potential problems reside outside the computer. Your Internet connection flows bothways . . . so must your security. Not only must our Internet connections be fortified to prevent external intrusion, they also provide secure management of internal extrusion.
Networking - How to check if a port is blocked on Windows. List of Common TCP/IP port numbers. User Rating: Details Written by Mell Rosandich Email List of Common TCP/IP port numbers Port 21 International Standard FTP port This is the port used for all FTP based file transfers, such as with programs like FTP Voyager, WS_FTP, Cute FTP, FTP NOW, and many more.
Port 22 International Standard SSH Server Listening port port used by Secure Shell servers, SSH, to listen for incoming connections. Port 23 International Standard Telnet port The port used by all Telnet applications. Port 25 International Standard SMTP mail port Standard port used for SMTP mail delivery. Sexy commercial for printers. Windows 7: Location-aware printing. The Story Of The Annoying Printer - Part 2 - The Sentence. The Story Of The Annoying Printer - Part 1 - The Evidence. Common Problems in NoMA - The Printer. Stupid Printer. The Printer. Computer Tricks. Comptia A+ Networking Part 2 - YouTube. Comptia A+ Networking Part 1 - YouTube. A+ Essentials - Peripherals (e.g. docking station, port replicator and media / accessory bay) 2.1 Identify the fundamental principles of using laptops and portable devices Identify names, purposes and characteristics of laptop-specific: Peripherals (e.g. docking station, port replicator and media / accessory bay) 1.
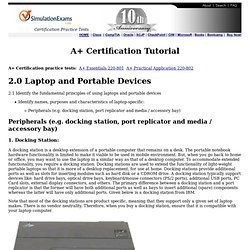
Docking Station: A docking station is a desktop extension of a portable computer that remains on a desk. The portable notebook hardware functionality is limited to make it viable to be used in mobile environment. Note that most of the docking stations are product specific, meaning that they support only a given set of laptop makes. Port Replicator: Usually, a notebook computer will have limited I/O ports due to compact design. As can seen from the figure above, a port replicator will have external ports for connecting a monitor, mouse, keyboard, modem, network card, printer, etc. Download practice tests: A+ Essentials , A+ Practical Technician Copyright © SimulationExams.com practice tests and certification training.
02: Put together a home media server - This Old Nerd. USB Connector Chart: Type A/B,Mini Type B4/5 Position Connectors,Popular,Hard to Find,L.