

IBM : les 5 innovations qui changeront nos vies dans les 5 prochaines années. Dans le cadre de ses prédictions annuelles, IBM Research a dévoilé cinq technologies d'avenir, notamment ce qu'il présente comme le plus petit ordinateur du monde, dont la taille est inférieure à celle d'un grain de riz.
Celui-ci se destine à l'Internet des objets et aux applications de blockchain. Le géant américain a par ailleurs dévoilé ses autres prévisions quant aux technologies amenées à s'imposer dans les cinq prochaines années. Cela vous intéressera aussi [EN VIDÉO] Interview : comment est née l'intelligence artificielle ? L’intelligence artificielle vise à mimer le fonctionnement du cerveau humain, ou du moins sa logique lorsqu’il s’agit de prendre des décisions. Chaque année, IBM Research dévoile cinq prédictions technologiques basées sur ses travaux de recherche et développement.
QuickHash.com: MD5, CRC32, SHA1, SHA256, Hash Online, Online Hash Generator, Hash Calculator. AES Encryption Flaw Exposes ASP.NET Sites. News UPDATED: Security Hack Exposes Forms Authentication in ASP.NET For more on this story, please see: Microsoft To Release Out-of-Band Patch for ASP.NET Security Flaw Two security researchers, Thai Duong and Juliano Rizzo, have discovered a bug in the default encryption mechanism used to protect the cookies normally used to implement Forms Authentication in ASP.NET.
Using their tool (the Padding Oracle Exploit Tool or POET), they can repeatedly modify an ASP.NET Forms Authentication cookie (normally encrypted using AES) and, by examining the errors returned, determine the Machine Key used to encrypt the cookie. The process is claimed to be 100 percent reliable and takes between 30 and 50 minutes for any site. Once the Machine Key is determined, attackers can create bogus forms authentication cookies. On a Web farm, these changes will have to be made on all the servers in the farm. A video, posted Thursday, Sept. 16 on YouTube shows Thai Duong demonstrating the attack using POET. DNSCrypt project official homepage. Backdoor threatens Diffie-Hillman encryption used in hundreds of millions of messages. It took two months, but employing as many as 3,000 CPUs, researchers have found a way to place backdoors in the cryptographic keys that protect websites, virtual private networks and internet servers, according to Ars Technica.
By injecting the undetectable backdoor in the 1,024-bit keys used in the Diffie-Hellman key exchange, hackers would be able to "decrypt hundreds of millions of encrypted communications as well as cryptographically impersonate key owners," the article stated Once believed impenetrable because of its use of large prime numbers, researchers devised a special prime that made the process easier. The implication is that actors looking to decrypt communications might now have a way to unscramble the discrete logarithm. "We are showing that trapdoored primes that would allow an adversary to efficiently break 1,024-bit keys are completely feasible," Nadia Heninger, one of the researchers at the University of Pennsylvania participating in the study, told Ars.
Learn Cryptography - Frequency Analysis. Frequency analysis is the study of letters or groups of letters contained in a ciphertext in an attempt to partially reveal the message.
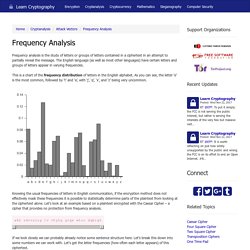
The English language (as well as most other languages) have certain letters and groups of letters appear in varying frequencies. This is a chart of the frequency distribution of letters in the English alphabet. As you can see, the letter ‘e’ is the most common, followed by ‘t’ and ‘a’, with ‘j’, ‘q’, ‘x’, and ‘z’ being very uncommon. Knowing the usual frequencies of letters in English communication, if the encryption method does not effectively mask these frequencies it is possible to statistically determine parts of the plaintext from looking at the ciphertext alone. Let’s look at an example based on a plaintext encrypted with the Caesar Cipher – a cipher that provides no protection from frequency analysis.
'First ever' SHA-1 hash collision calculated. All it took were five clever brains... and 6,610 years of processor time. Google researchers and academics have today demonstrated it is possible – following years of number crunching – to produce two different documents that have the same SHA-1 hash signature.

This proves what we've long suspected: that SHA-1 is weak and can't be trusted. This is bad news because the SHA-1 hashing algorithm is used across the internet, from Git repositories to file deduplication systems to HTTPS certificates used to protect online banking and other websites. SHA-1 signatures are used to prove that blobs of data – which could be software source code, emails, PDFs, website certificates, etc – have not been tampered with by miscreants, or altered in any other way.
Now researchers at CWI Amsterdam and bods at Google have managed to alter a PDF without changing its SHA-1 hash value. That makes it a lot easier to pass off the meddled-with version as the legit copy. Home DE - CrypTool Portal. Portrait d'un savant : Alan Turing. Alan Mathison Turing naît le 23 juin 1912 à Londres.

Son père est administrateur colonial à Madras en Inde. Au Malborough Collège, ses dons hors du commun sont vite reconnus. La machine Enigma : simulateur. Useful Cryptography Resources – A Few Thoughts on Cryptographic Engineering. This page is an attempt to compile some of the top technical crypto and security blogs, textbooks, and websites.

It’s very much a work in progress. If you think something is missing, please leave a note in comments or drop me a line. Top Cryptography and Security Blogs Schneier on security. One of the oldest and most famous security blogs. Root Labs rdist. Bristol Cryptography Blog. Travis Goodspeed. Cours-crypto-070206.pdf.
Cryptographie. Un article de Wikipédia, l'encyclopédie libre.
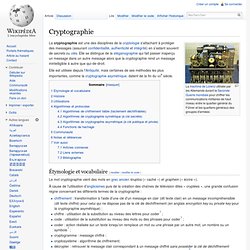
La machine de Lorenz utilisée par les Allemands durant la Seconde Guerre mondiale pour chiffrer les communications militaires de haut niveau entre le quartier-général du Führer et les quartiers-généraux des groupes d'armées Elle est utilisée depuis l'Antiquité, mais certaines de ses méthodes les plus importantes, comme la cryptographie asymétrique, datent de la fin du XXe siècle.
Cryptologie. Un article de Wikipédia, l'encyclopédie libre.
La cryptologie, étymologiquement la science du secret, ne peut être vraiment considérée comme une science que depuis peu de temps. Cette science englobe la cryptographie — l'écriture secrète – et la cryptanalyse – l'analyse de cette dernière. Histoire de la cryptologie. Un article de Wikipédia, l'encyclopédie libre.
Dans l'Antiquité[modifier | modifier le code] Les premières méthodes de chiffrement[modifier | modifier le code] Le plus vieux document chiffré[modifier | modifier le code]