

Find Subdomains Online. Domain Search - Find registered and dropped domain names through all TLDs. Tool description Find registered and dropped domain names based on one or more keywords.
Keywords can be like a city, brand or trademark. Search through all Top Level Domains including gTLDs, nTLDs and ccTLDs. Example objectives Discover newly registered domain names.Perform research on your trademark or brand and find illegal use of it.Discover registered domain name variations.Find previously registered (dropped) domain names. Q: How many domains do you have? Q: When are newly registered domains available in Domain Search? Q: Is Domain Search available for all Top Level Domains? Q: Can you give some examples of queries? Intelligence Gathering - The Penetration Testing Execution Standard. This section defines the Intelligence Gathering activities of a penetration test.
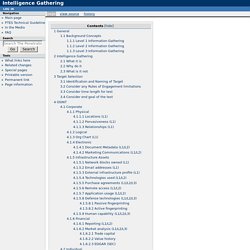
The purpose of this document is to provide a standard designed specifically for the pentester performing reconnaissance against a target (typically corporate, military, or related). The document details the thought process and goals of pentesting reconnaissance, and when used properly, helps the reader to produce a highly strategic plan for attacking a target. Background Concepts Levels are an important concept for this document and for PTES as a whole.
It’s a maturity model of sorts for pentesting. The Intelligence Gathering levels are currently split into three categories, and a typical example is given for each one. Resources - Toddington. Online Search and Security Tools and Resources for the Investigative and Intelligence Professional Last updated: April 12, 2019.

While there are a large number of search resources available online, it is often challenging to find the most effective tool for locating a specific type of data. TII’s extensive network of online research professionals have created and maintain this collection of some of the best free OSINT tools and resources available for investigative and research professionals to assist in finding people, places, things, and much more. Click any category below to expand the selection.
To report a broken link or to make a suggestion, contact us More Free Search Resources TII’s Online Research and Intelligence Newsletter is a FREE resource relied on by thousands of intelligence, research, and investigative professionals worldwide. Automating OSINT Blog. Free Python Webinar Sign up for one of my free Python webinars where I teach you the basics in an hour or less.
Click here to register now, it’s 100% free. Theharvester - Information Gathering. The objective of this program is to gather emails, subdomains, hosts, employee names, open ports and banners from different public sources like search engines, PGP key servers and SHODAN computer database.
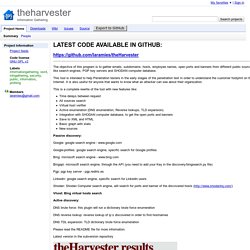
This tool is intended to help Penetration testers in the early stages of the penetration test in order to understand the customer footprint on the Internet. It is also useful for anyone that wants to know what an attacker can see about their organization. This is a complete rewrite of the tool with new features like: Time delays between request All sources search Virtual host verifier Active enumeration (DNS enumeration, Reverse lookups, TLD expansion) Integration with SHODAN computer database, to get the open ports and banners Save to XML and HTML Basic graph with stats New sources Passive discovery: Google: google search engine - www.google.com Google-profiles: google search engine, specific search for Google profiles.
OSINT Training by Michael Bazzell. Online Penetration Testing Tools. About this tool 'Find Subdomains' allows you to discover subdomains of your target domain and increase your attack surface.
Finding subdomains is useful in a penetration test because they point to different applications and indicate different external network ranges used by the target company. For instance, x.company.com points to IP 1.1.1.1 and y.company.com points to IP 2.2.2.2. Now you know two different ip ranges possibly owned by your target and you can extend the attack surface. Furthermore, subdomains sometimes host 'non-public' applications (e.g. test, development, restricted) which are usually less secure than the public applications so they can be the primary attack targets. Parameters Domain name: is the target domain (ex. oracle.com, yahoo.com, etc) Include subdomain details: this option instructs the tool to do DNS resolution for each subdomain discovered and whois queries in order to determine the network owners of the ip addresses How it works.
Footprinting-it-it-why-62.