

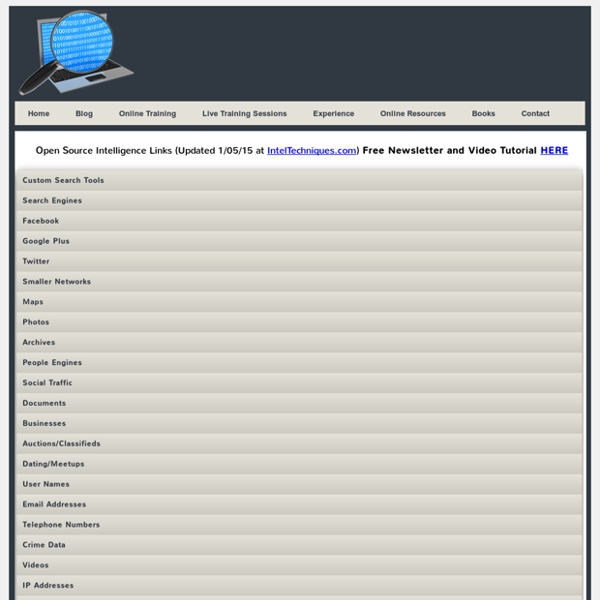
Free People Search Engines & People Finder. Find People Free, Locate People and Search People Free. Person Search, Locator, Finder and Searches Online. Open-Source Intelligence : Collection Search Strategies, Techniques & Tools – Analyzing – Reporting & Presenting Results Open-Source Intelligence Now Avaliable Collection Search Strategies, Techniques & Tools – Analyzing – Reporting & Presenting Results For Law Enforcement, Security Professionals and Public Safety Officials Intelligence Best Practices Training for Government - Government Support Contractors - Corporations - Banks This course is available for On-Site Training . We will bring this course to your agency or company. Contact Don Dickson, On-Site Training Manager at (301) 455-5633 or Don.Dickson@GovernmentTrainingInc.com About this course Acquiring open source intelligence (OSINT) requires more than just an ability to use the Internet. This course provides a five step process developed over ten years and augmented by tips, hints, checklists, examples and case studies that will lead the student to information once considered unavailable and unreachable. Shown below is an evaluation by several members of a Federal Agency Intelligence Unit attending our Open Source Training Course. Q 5. Q 6. Q 7. Ms.
OSINT Search Tool by Michael Bazzell | Open Source Intelligence Techniques Live Events Online Resources Blog Podcast Books Contact Facebook FBStalker tool uses Graph Search for powerful OSINT analysis Facebook, and more in general social networks, is a platform that if not properly managed could harm user’s privacy, the fact that also friends’ social behavior could have a dangerous impact on our digital experience is very concerning. Recently at the Hack In The Box conference in Kuala Lumpur, security experts Jonathan Werrett and Keith Lee from SpiderLabs demonstrated how to conduct a powerful OSINT analysis using a simple tool they created, anyone using it could find a comprehensive amount of data on any user of the popular social network. The tool for information gathering on Facebook created by the researchers is named FBStalker, a name that give us the idea of the potential of the instrument. FBStalker reverse-engineers the Facebook Graph to find information on every user, the tool does not require a direct friendship with targeted profiles, it just needs to access to parts of victim’s posts marked as public. It is questionable whether a tool like FBStalker is legal:
OSINT Tools - Recommendations List | Subliminal Hacking With the New Year fast approaching I thought now would be a great time to post the first draft of some recommended Open Source Intelligence (OSINT) gathering tools and resources. I will look to maintain this list overtime and have it grow, so if you come across something you think should be on the list, drop me an email or leave a comment for consideration. The reconnaissance phase of any engagement is very important and can often save you alot of time and of course money. If you are really lucky you may even find the information you are looking for freely available posted online. Either way the information you find will only be as good as the tools you use, so with this in mind here is the list based on tools I have come across over the years or have been recommended by other InfoSec peeps. * Please note even though the aim is to provide information for free OSINT Tools, some may require a subscription or commercial fee.
How to Search Google Like a Pro: 11 Tricks You Have to Know Google is a powerful tool, but you’re missing out on a lot of that power if you just type words into it. Master Google and find the best results faster with these search tricks. Whether you’re an inexperienced user or a seasoned professional, you’ll probably find at least one search operator you weren’t aware of here. Many of Google’s search operators aren’t very well-known. Exact Words and Phrases One of the most basic and widely known search tricks is using quotation marks to search for an exact phrase. “Hello World” This same method now works for exact-word queries. “mining” Excluding a Word The minus sign allows you to specify words that shouldn’t appear in your results. linux distributions -ubuntu Site Search The site: operator allows you to perform a search in a specific site. site:howtogeek.com windows 7 You can also use the site: operator to specify a domain. Related Words ~geek Apparently, “Linux” is the most similar word to geek, followed by “Greek.” The Wildcard Time Ranges File Type
Network Intelligence Gathering This article is all about different information-gathering techniques on the network. It is the most essential and important task of attackers. Knowing the opponents and their interests can be valuable. Here I am going to show you which are the different ways and techniques one can do the network information/intelligence gathering. Let’s think of any thrilling movie theft. What do robbers do before they break into the bank or anything else? The same scenario can also be applied in the information security world. The map below shows the juicy areas in which attackers might be interested. Before starting to footprint anything, we need to keep in mind what or who our target is. Techniques of Intelligence Gathering Information Available in Air There is much information that is publicly available, but no one knows about it. In older days, Company Webpages used to provide valuable information about their security policy and configuration directly to the client side. Want to learn more?? Summary
8. Cyberstalking tools for reconnaissance - Nine must-have OSINT tools searchSecurity.in Nine must-have OSINT tools 8. Cyberstalking tools for reconnaissance 9 of 10 Karthik Poojary Published: 24 Jul 2012 There are several websites and OSINT tools available online that can be used to find public information about a particular person. More from this story Back to top Latest News Email Alerts Register now to receive SearchSecurity.in-related news, tips and more, delivered to your inbox. By submitting your personal information, you agree to receive emails regarding relevant products and special offers from TechTarget and its partners. Ads by Google More from Related TechTarget Sites All Rights Reserved,Copyright 2009 - 2015, TechTarget