

If Your iCloud Password Is On This List, Change It Before You Get Hacked. Weak passwords, in 2013 it is still a frequent error. It was October 2012 when for the first time I’ve seen a report from SpashData on most common passwords chosen by users to protect their account on various services.
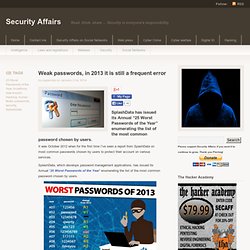
SplashData, which develops password management applications, has issued its Annual “25 Worst Passwords of the Year” enumerating the list of the most common password chosen by users. If you are a hacker and need to brute force a login form, probably you can benefit from this reading, hack a password sometime could be very easy because the human factor. User’s wrong habits represent serious weakness, unaware users adopt a secret code easy to remember and use to share them among different web services.
Reading the passwords I believe that people would start being really concerned at the level of security offered by their passwords. Let’s give a look to the list of the most common passwords in 2013. The top 10 password in 2012 was: The list related to 2013 is.
Part 1: Authentication Series – A world of passwords. Article published on The Malta Indipendent Ron Kelson, Pierluigi Paganini, Fabian Martin, David Pace, Benjamin Gittins In our previous articles we discussed malware, phishing, viruses and other computer infections designed to maliciously acquire your personal information.
Most people use extremely simple passwords. In this article we will look at the risks involved in the above practices and discuss how to select a secure password that you can remember. The problem with sharing your password Traditionally, humans have identified each other by recognising the other person’s face, and voice. A password is supposed to be a secret known only to you and the service provider. Lets imagine for one moment that, just like in science fiction, each of us can change the physical shape and size of our body and the sound of our voice at will.
The problem with reusing your password. Password Safe. The security of Twofish in a password database Support Password Safe is now an open source project.

As of February 7, 2014, the latest Windows version is 3.33. A Linux version is currently in beta. To download the program, or for technical support, please visit its Sourceforge page. How I cracked my neighbor’s WiFi password without breaking a sweat. Last week's feature explaining why passwords are under assault like never before touched a nerve with many Ars readers, and with good reason.

After all, passwords are the keys that secure Web-based bank accounts, sensitive e-mail services, and virtually every other facet of our online life. Lose control of the wrong password and it may only be a matter of time until the rest of our digital assets fall, too. Why passwords have never been weaker—and crackers have never been stronger. In late 2010, Sean Brooks received three e-mails over a span of 30 hours warning that his accounts on LinkedIn, Battle.net, and other popular websites were at risk.
He was tempted to dismiss them as hoaxes—until he noticed they included specifics that weren't typical of mass-produced phishing scams. The e-mails said that his login credentials for various Gawker websites had been exposed by hackers who rooted the sites' servers, then bragged about it online; if Brooks used the same e-mail and password for other accounts, they would be compromised too.
The warnings Brooks and millions of other people received that December weren't fabrications. Within hours of anonymous hackers penetrating Gawker servers and exposing cryptographically protected passwords for 1.3 million of its users, botnets were cracking the passwords and using them to commandeer Twitter accounts and send spam. Zappos breach highlights fragile password, personal data security. Another breach, another reminder that personal data created and stored on the Internet is often more valuable than credit card numbers and that when compromised can have much more damaging consequences.
This time it was Zappos.com joining the ranks of Sony, Gawker, rootkit.com and many others who have lost account passwords and other data to hackers. Zappos has reset 24+ million passwords exposed during a hack of its systems Sunday, sending its users scrambling to create new passwords. In an email, Zappos CEO Tony Hsieh also advised users to change their passwords on any other web site where they used the same or similar credentials. And he called out possible phishing scam exposure by reminding users that Zappos.com "will never ask you for personal or account information in an e-mail. " This Is Why You Want Passwords On Your Phone And Computer. Do You Really Need a Password You Can Barely Remember? Think of a word.
A password. Make it at least eight characters long, but no more than 12. Don’t repeat any characters more than twice. Make sure it has at least one letter, and one number. In fact, it has to start with a number. And try to make it memorable. Feeling flummoxed? The requirements above are for a real website. To researchers Cormac Herley and Paul C. van Oorschot, the computer industry’s non-stop campaign to force us to to strengthen our passwords is misguided — demanding too much work from users for the benefits it delivers. In a new research paper, van Oorschot and Herley, a Microsoft researcher, say that IT pros often get things backward when it comes to instructing us on password security. In other words, users get easy answers rather than the information they really need to hear. The World’s First Data Breach? Password problems have been around since the 1960s. One day, a software bug mixed up the welcome message displayed to users of the system with its password file.
Hacking Tip: Password Cracking with Cain & Abel.