

Uk.businessinsider. In late November, hackers targeted Sony Pictures Entertainment in an unprecedented cyber attack.
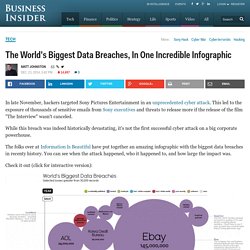
This led to the exposure of thousands of sensitive emails from Sony executives and threats to release more if the release of the film "The Interview" wasn't canceled. While this breach was indeed historically devastating, it's not the first successful cyber attack on a big corporate powerhouse. The folks over at Information Is Beautiful have put together an amazing infographic with the biggest data breaches in recenty history. You can see when the attack happened, who it happened to, and how large the impact was.
Check it out (click for interactive version):
Piratage d’Orange. Starbucks App hacked. Exclusive: More well-known U.S. retailers victims of cyber attacks - sources. US data breach. This Week in Breach Roundup. pD breach at IGF2013. New pan-European data breach rules for telecos & ISPs. How to Respond to a Data Breach, Part 2. This 1 Little Known Cause of Data Breach Can Cost You Everything. Report of Data Protection Review Group on breach notification. EU new data breach rule. The Data Chain.
IEEE log. IEEE and the log story IEEE (Institute of Electrical and Electronics Engineers) is renowned as one of the world-leading organizations in standard development and the promotion of scientific and educational development within the Electrical, Electronics, Communications, Computer Engineering, Computer Science and related fields.

The organization has more than 415,000 members all over the world, almost half of them in the United States [1]. By the nature of the organization, IEEE members are highly specialised individuals, many of them working in critical industry, governmental and military projects. Furthermore, it would be reasonable to assume, that an organization publishing leading security-focused publications [2], would value the privacy of its members, and be proactive in keeping their data secure. Log analysis It is certainly unfortunate this information was leaked out, and who knows who got it before it got fixed. Apple ID stolen from FBI. FBI Agent's Laptop 'Hacked' To Grab 12 Million Apple IDs - UPDATED. Privacy alert at papers dump. Privacy alert at papers dump Eddie Luk Tuesday, September 04, 2012.
Apple ID stolen from FBI. SSS official laments security breach. Two operatives arrested and detained in connection with the personnel information leak A senior intelligence official of the State Security service (SSS) has that the lives of officers and those of their families have been put at risk. Following the leak of personal data of more than 60 past and current employees of the SSS on the Internet, the official added that two SSS operatives had been arrested and detained in connection with the intelligence breach. He lamented that the release of their restricted contact details, including home addresses and names of immediate family members, was affecting their psyche and those of their families.
"This is a serious problem for personnel like me in service. OUPS – On a volé les plans du palais de l’Elysée ! Les plans de l’Elysée dérobés dans une voiture. FL: Personal information from old Tampa car dealership could be compromised.
Lastfm passwords hacked. Linkedin passwords hacked. Uni of Nebraska data breach. Huge Data Breach at U of Nebraska Traced to Undergrad Student. May 31, 2012 - University of Nebraska-Lincoln police needed to look no further than their own campus to identify a suspect in last week’s highly-publicized hacking incident.

UNL Police Chief, Owen Yardley, said a UNL undergraduate student was a suspect in the security breach of the Nebraska Student Information System database, which serves the University of Nebraska and the state colleges. The breach may have exposed the financial information and Social Security numbers of hundreds of thousands of NU students, alumni and employees. Joshua Mauk, NU information security officer, couldn't say whether more than one person was involved in the incident. “The information we had led to this individual.
I can't comment on whether others are involved at this time.” The student's computer and related equipment were confiscated and are being analyzed by police and the FBI. Yardley said the student was identified by NU Computing Services personnel through IP addresses used to access the system.
London Marathoners details. Visa processor breach. Barclay Cards. Nasa looses a laptop. Data breach study. Get Cocoon: 1 million YouPorn users ex... 1 million YouPorn users exposed; data breach required no security penetration. February 22, 2012, 2:35 PM — Some stories make you want to wash your hands afterward.
With others it's simpler to just wear vinyl gloves while you type. This is one of the latter. A hack that penetrated the user database at YouPorn, one of the largest free porn sites on the web, became public knowledge this week when some user data, including email addresses and were posted on Swedish web forum Flashback.org.
The sample that was published there is a subset of the data that was stolen – more than a million user names and passwords from YouPorn's chat section at chat.youporn.com. The hack didn't need to probe the most secure dataspace on the YouPorn site, according to EuroSecure, a Swedish security distributor that analyzed the breach. Sometime around November, 2007, a "careless programmer" left the debug logging function turned on on the main YouPorn server farm, according to Anders Nilsson, CTO at EuroSecure. The 15 worst data security breaches of the 21st Century. Data security breaches happen daily in too many places at once to keep count.

But what constitutes a huge breach versus a small one? For some perspective, we take a look at 15 of the biggest incidents in recent memory. Helping us out are security practitioners from a variety of industries, including more than a dozen members of LinkedIn's Information Security Community, who provided nominations for the list. A federal grand jury indicted Albert Gonzalez and two unnamed Russian accomplices in 2009. Gonzalez, a Cuban-American, was alleged to have masterminded the international operation that stole the credit and debit cards.
TRENDnet Cameras vulnerability. Liability for breach of privacy. Summit-sports-20111221. Nyc. ClassAction. Adidas websites go offline after security breach. SPORTS EQUIPMENT MAKER Adidas took some of its websites offline after a security breach.
Adidas said it became aware of a "sophisticated, criminal cyber-attack" on its various web sites on 3 November but the firm claimed it found no evidence that customers' data had been stolen. Instead, Adidas said it took the web sites offline to protect its users. Adidas issued a statement saying that it took the websites affected - adidas.com, reebok.com, micoach.com, adidas-group.com and various Ecommerce shops - offline as it undertakes a "thorough forensic review". Since Adidas uncovered the attack, it claims to have put in place additional security measures.
The biggest security breaches ever. How Hacktivism Affects Us All. In December 2010, a group of nearly 3000 activists under the name “Operation Payback” launched online attacksagainst PayPal, MasterCard, and Visa, briefly knocking the three financial services’ sites offline and attempting to prevent consumers from accessing their online banking services.
The activists retaliated against the three companies for severing ties with WikiLeaks, an online repository for whistleblower data that had recently included thousands of secret communications from the U.S. State Department and other world governmental agencies. Nine months later more than a dozen people--most between the ages of 19 and 24--were arrested in connection with these denial-of-service (DoS) attacks, even as new attacks were hitting corporate, military, and government sites worldwide.
California Strengthens Breach Notification Requirements : Data Privacy Monitor : Lawyers & Attorneys for Information Security, Breach Notifications, Online Privacy, Cloud Computing & Financial Privacy: Baker Hostetler Law Firm. This week California Governor Jerry Brown signed into law a new California data breach statute that strengthens notification requirements for residents of California.

California currently has some of the most prolific and detailed consumer protection oriented laws impacting privacy and breach protection in the country. The current law requires that any entity that owns or licenses computerized data that contains personal information to notify affected individuals of any breach of the security of that data and whose unencrypted personal information was acquired, or reasonably believed to have been acquired, by an unauthorized person. Personal information includes the following unencrypted data elements: 1) social security number; 2) driver’s licenses or California identification number; 3) account number, credit debit card number in combination with security code, access code or password of an person’s financial account; and 4) medical information. • In writing in plain language.
Citi Cards Japan data theft hits 92,408 in Japan. Wi-Fi security: A Guide for the Public. Computers and many other devices, including smart phones and PDAs, can connect to the internet wirelessly using Wi-Fi.

An unsecured Wi-Fi connection makes it easier for hackers to access your private files and information, and it allows strangers to use your internet connection. These are general tips on changing your router and network settings. You may need to check the instructions for your wireless equipment for the technical details. If you need more guidance on checking or changing your settings, your Wi-Fi equipment supplier or internet provider will provide advice on their websites. How do I check whether my network is secure? Home Wi-Fi networks are typically created and accessed through a physical device called a broadband router – also known as a hub or wireless router.
Simple method When connecting to your wireless network from any device for the first time, you will be asked for the wireless security key. Advanced method.