

Layer 2 Tunneling Protocol. In computer networking, Layer 2 Tunneling Protocol (L2TP) is a tunneling protocol used to support virtual private networks (VPNs) or as part of the delivery of services by ISPs.
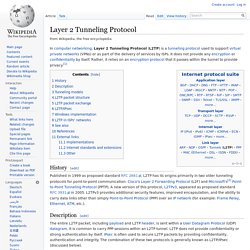
It does not provide any encryption or confidentiality by itself. Rather, it relies on an encryption protocol that it passes within the tunnel to provide privacy.[1] History[edit] Setting Up an iOS 7 On-Demand VPN. This is a "how to" article about configuring an iPhone to get it to activate a VPN "on-demand" connection according to some specific rules.

My overall goal was to have the iPhone automatically create a VPN connection to our network and route all the iPhone's networking traffic through our network whenever the iPhone was not directly connected to our network via one of our network's WiFi connection points. While some of the article is specific to the goals I wanted to achieve and to the use of pfSense for the VPN server, much of the information will be of use to others who are attempting to do something similar. I've also written some comments about pfSense.
There's a lot of "stuff" here but it's all there for a reason ... details, details. I've tried to be both rigorous and complete as well as provide alternatives. Aside from the requirements topics below, there are 3 "tracks": Do you need a VPN? Roll your own. - OSOMac. In the recent past, there has been more and more talking about privacy, security, encryption, etc.
Many articles recommend to use a VPN whenever you feel your Internet connection is not safe (when you are at a coffee shop, hotel, airport, or any place where you don’t know and trust the provider). Actually VPN is not even the correct term: a VPN is just a private (encrypted) connection to a network, which goes through the Internet. What everybody is really recommending is a proxy service, with a VPN to secure the connection. All your activity will be strongly encrypted between your device and the proxy, and for all practical purposes the rest of the world will deal with your proxy instead of your device.
Now, there are several providers out there, most of which are probably fine: I have used StrongVPN for a while, and never had any issue with them. Cost. Layer 2 Tunneling Protocol. L2TP/IPSec with Pre-Shared Key (PSK) VPN server. I want to be able to break through into my network from my phone or laptop – PPTP is too insecure and OpenVPN is still too much of a headache plus not generally built into Android.
I followed these two guides: and Let’s install/modify several files. We will assume that 192.168.1.0/24 is your local subnet, and your server is 192.168.1.2 in that subnet. The VPN will be on the 10.10.0.0/24 subnet. sudo apt-get install openswan ppp xl2tpd Edit /etc/ipsec.conf to contain the following: The default behavior of IPsec NAT traversal (NAT-T) is changed in Windows XP Service Pack 2. This article describes a change in the default behavior of Internet Protocol security (IPsec) network address translation (NAT) traversal (NAT-T) that has been implemented in Microsoft Windows XP Service Pack 2 (SP2).

You can modify this default behavior in Windows XP SP2 by using the following registry value: AssumeUDPEncapsulationContextOnSendRule No change has been made in the Microsoft Windows 2000 IPsec NAT-T implementation. Important This section, method, or task contains steps that tell you how to modify the registry. However, serious problems might occur if you modify the registry incorrectly.
An Illustrated Guide to IPsec. IPsec is a suite of protocols for securing network connections, but the details and many variations quickly become overwhelming.

This is particularly the case when trying to interoperate between disparate systems, causing more than one engineer to just mindlessly turn the knobs when attempting to bring up a new connection. This Tech Tip means to give bottom-up coverage of the low-level protocols used in an IPv4 context (we provide no coverage of IPv6). This is not a deployment guide or best-practices document — we're looking at it strictly at the protocol level on up, rather than from the big picture on down. NOTE: originally this was to be a pair of papers, with the second covering Key Exchange and the like, but it appears that this was not meant to be. Sorry. In this section, we'll touch on some of the items in the form of a glossary, with a compare-and-contrast to show which terms relate to which other terms. AH versus ESP Tunnel mode versus Transport mode IKE versus manual keys ver hlen. L2TP (Ubuntu) server setup for iOS clients. For you road warriors who wish to set up their own VPN to secure their traffic when using any untrusted/unprotected networks (“free” WiFi?)
When travelling, this would be the thing you use: a trusted VPN setup. While I did dabble with OpenVPN sometime back, protocols like L2TP would be more commonly supported, especially on the “venerable” iOS device (iPhone, iPod Touch, iPad), and on Windoze machines, Android, etc. This post will be on what you’ll need to setup a L2TP server in Ubuntu for iOS devices to connect to.
The server is assumed to be directly accessible from the internet. Some of the stuff are taken from other places, for my own reference here. The L2TP server setup mainly comprises of three parts actually (surprise!). Layer 2 Tunneling Protocol.