

Get the Ultimate 2018 Hacker Bundle – Pay What You Want. Politie arresteert 19-jarige Hagenaar wegens afpersing na DDoS-aanvallen. Pre-Installed Keylogger Found On Over 460 HP Laptop Models. HP has an awful history of 'accidentally' leaving keyloggers onto its customers' laptops. At least two times this year, HP laptops were caught with pre-installed keylogger or spyware applications. I was following a tweet made by a security researcher claiming to have found a built-in keylogger in several HP laptops, and now he went public with his findings. A security researcher who goes by the name of ZwClose discovered a keylogger in several Hewlett-Packard (HP) laptops that could allow hackers to record your every keystroke and steal sensitive data, including passwords, account information, and credit card details.
The Keylogger was found embedded in the SynTP.sys file, a part of Synaptics touchpad driver that ships with HP notebook computers, leaving more than 460 HP Notebook models vulnerable to hackers. Here’s the location of the registry key: "A party would need administrative privileges in order to take advantage of the vulnerability. Android Flaw Lets Hackers Inject Malware Into Apps Without Altering Signatures. Millions of Android devices are at serious risk of a newly disclosed critical vulnerability that allows attackers to secretly overwrite legitimate applications installed on your smartphone with their malicious versions.
Dubbed Janus, the vulnerability allows attackers to modify the code of Android apps without affecting their signature verification certificates, eventually allowing them to distribute malicious update for the legitimate apps, which looks and works same as the original apps. The vulnerability (CVE-2017-13156) was discovered and reported to Google by security researchers from mobile security firm GuardSquare this summer and has been patched by Google, among four dozen vulnerabilities, as part of its December Android Security Bulletin.
The vulnerability affects apps using APK signature scheme v1 installed on devices running Android versions 5 (Lollipop) and 6 (Marshmallow). Process Doppelgänging: New Malware Evasion Technique Works On All Windows Versions. A team of security researchers has discovered a new malware evasion technique that could help malware authors defeat most of the modern antivirus solutions and forensic tools.
Dubbed Process Doppelgänging, the new fileless code injection technique takes advantage of a built-in Windows function and an undocumented implementation of Windows process loader. Ensilo security researchers Tal Liberman and Eugene Kogan, who discovered the Process Doppelgänging attack, presented their findings today at Black Hat 2017 Security conference held in London. Zero-day iOS HomeKit vulnerability allowed remote access to smart accessories including locks, fix rolling out. A HomeKit vulnerability in the current version of iOS 11.2 has been demonstrated to 9to5Mac that allows unauthorized control of accessories including smart locks and garage door openers.
Our understanding is Apple has rolled out a server-side fix that now prevent unauthorized access from occurring while limiting some functionality, and an update to iOS 11.2 coming next week will restore that full functionality. 9to5Mac Happy Hour The vulnerability, which we won’t describe in detail and was difficult to reproduce, allowed unauthorized control of HomeKit-connected accessories including smart lights, thermostats, and plugs.
The most serious ramification of this vulnerability prior to the fix is unauthorized remote control of smart locks and connected garage door openers, the former of which was demonstrated to 9to5Mac. The issue was not with smart home products individually but instead with the HomeKit framework itself that connects products from various companies. Man Hacks Jail Computer Network to Get Friend Released Early. Ethiopian Espionage Shows Commercial Spyware Is Out of Control. Phishing Attacks on Bitcoin Wallets Intensify as Price Goes Higher and Higher. PayPal Subsidiary Data Breach Hits Up to 1.6 Million Customers. Global e-commerce business PayPal has disclosed a data breach that may have compromised personally identifiable information for roughly 1.6 million customers at a payment processing company PayPal acquired earlier this year.
PayPal Holdings Inc. said Friday that a review of its recently acquired company TIO Networks showed evidence of unauthorized access to the company's network, including some confidential parts where the personal information of TIO's customers and customers of TIO billers stored. Acquired by PayPal for US$233 Million in July 2017, TIO Network is a cloud-based multi-channel bill payment processor and receivables management provider that serves the largest telecom, wireless, cable and utility bill issuers in North America. PayPal did not clear when or how the data breach incident took place, neither it revealed details about the types of information being stolen by the hackers, but the company did confirm that its platform and systems were not affected by the incident. World's Biggest Botnet Just Sent 12.5 Million Emails With Scarab Ransomware.
A massive malicious email campaign that stems from the world's largest spam botnet Necurs is spreading a new strain of ransomware at the rate of over 2 million emails per hour and hitting computers across the globe.
The popular malspam botnet Necrus which has previously found distributing Dridex banking trojan, Trickbot banking trojan, Locky ransomware, and Jaff ransomware, has now started spreading a new version of Scarab ransomware. According to F-Secure, Necurs botnet is the most prominent deliverer of spam emails with five to six million infected hosts online monthly and is responsible for the biggest single malware spam campaigns. Scarab ransomware is a relatively new ransomware family that was initially spotted by ID Ransomware creator Michael Gillespie in June this year. Jailbreak : deux plateformes d'applications ferment boutique, est-ce la fin du Jailbreak sous iOS ?
Saurik l'abordait en juillet cette année déjà : le Jailbreak sur iOS est à bout de souffle.
Et il n'est pas question uniquement des protections mises en place par Apple au fil du temps, c'est l'intérêt même du jailbreak qui perd de son sens au fil des années. Ainsi, Saurik, le créateur de Cydia expliquait que le but original du jailbreak était de donner plus de liberté aux utilisateurs d'iPhone et iPad puisque Apple verrouillait énormément ses appareils. 22-Year-Old Hacker Pleads Guilty to 2014 Yahoo Hack, Admits Helping Russian Intelligence. Karim Baratov, a 22-year-old Kazakhstan-born Canadian citizen, has pleaded guilty to hacking charges over his involvement in massive 2014 Yahoo data breach that affected all three billion yahoo accounts.
In March, the US Justice Department announced charges against two Russian intelligence officers (Dmitry Dokuchaev and Igor Sushchin) from Russia's Federal Security Service (FSB) and two hackers (Alexsey Belan and Karim Baratov) for breaking into yahoo servers in 2014. While Karim Baratov (Kay, a.k.a Karim Taloverov, a.k.a Karim Akehmet Tokbergenov) was arrested in Toronto at his Ancaster home by the Toronto Police Department in March this year, Alexsey Belan and both FSB officers currently reside in Russia, unlikely to be extradited.
In the federal district court in San Francisco on Tuesday, Baratov admitted to helping the Russian spies and pleaded guilty to a total of nine counts which includes: Les 5 pires cybermenaces attendues en 2018. MacOS High Sierra Bug Lets Anyone Gain Root Access Without a Password. If you own a Mac computer and run the latest version of Apple's operating system, macOS High Sierra, then you need to be extra careful with your computer.
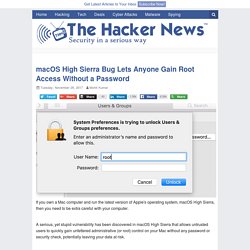
A serious, yet stupid vulnerability has been discovered in macOS High Sierra that allows untrusted users to quickly gain unfettered administrative (or root) control on your Mac without any password or security check, potentially leaving your data at risk. Discovered by developer Lemi Orhan Ergin on Tuesday, the vulnerability only requires anyone with physical access to the target macOS machine to enter "root" into the username field, leave the password blank, and hit the Enter a few times—and Voila! In simple words, the flaw allows an unauthorized user that gets physical access on a target computer to immediately gain the highest level of access to the computer, known as "root," without actually typing any password. Needless to say, this blindingly easy Mac exploit really scary stuff. Cryptocurrency Mining Scripts Now Run Even After You Close Your Browser.
Some websites have found using a simple yet effective technique to keep their cryptocurrency mining javascript secretly running in the background even when you close your web browser. Due to the recent surge in cryptocurrency prices, hackers and even legitimate website administrators are increasingly using JavaScript-based cryptocurrency miners to monetize by levying the CPU power of their visitor's PC to mine Bitcoin or other cryptocurrencies. After the world's most popular torrent download website, The Pirate Bay, caught secretly using Coinhive, a browser-based cryptocurrency miner service, on its site last month, thousands of other websites also started using the service as an alternative monetization model to banner ads. Tout comprendre à la faille de sécurité critique sur macOS High Sierra.
HP Silently Installs Telemetry Bloatware On Your PC—Here's How to Remove It. Do you own a Hewlett-Packard (HP) Windows PC or laptop?
Multiple HP customers from around the world are reporting that HP has started deploying a "spyware" onto their laptops—without informing them or asking their permission. The application being branded as spyware is actually a Windows Telemetry service deployed by HP, called "HP Touchpoint Analytics Client," which was first identified on November 15. According to reports on several online forums, the telemetry software—which the HP customers said they never opted to have installed and had no idea was continually running in the background—was pushed out in a recent update.
HP Silently Installs Telemetry Bloatware On Your PC—Here's How to Remove It. Security Update 2017-001 BREAKS File Sharing. Adobe Flash : une faille zero-day utilisée pour répandre le spyware FinSpy. Microsoft corrige discrètement les vulnérabilités Krack/WPA2 de Windows. L'éditeur a fait savoir hier qu'il avait corrigé les vulnérabilités Krack identifiées dans le protocole WPA2 utilisé pour sécuriser les réseaux sans fil WiFi.
Ce n’est que depuis hier que le catalogue en ligne Security Update Guide, qui remplace depuis cette année les fameux bulletins de sécurité de Microsoft, comporte des détails sur la mise à jour de sécurité WiFi Protected Access II (WPA2). Microsoft se serait faite voler une base de données contenant les vulnérabilités de ses logiciels. En 2013, les firmes Apple, Twitter, Facebook et Microsoft se sont faites pirater par un groupe de cybercriminels talentueux.
A l'époque, Microsoft est restée très discrète sur les conséquences potentiellement graves de ce piratage. SSD Drives Vulnerable to Attacks That Corrupt User Data. NAND flash memory chips, the building blocks of solid-state drives (SSDs), include what could be called "programming vulnerabilities" that can be exploited to alter stored data or shorten the SSD's lifespan. During the past few years, SSDs have slowly replaced classic disk-based HDDs as the prime storage medium for the world's data, taking over not only in data centers, but our phones, tablets, laptops, and desktop PCs. At their heart, SSDs are a collection of smaller components named NAND flash memory chips, all clustered together on rows, similar to classic RAM memory chips. Viacom Left Sensitive Data And Secret Access Key On Unsecured Amazon Server. Viacom—the popular entertainment and media company that owns Paramount Pictures, Comedy Central, MTV, and hundreds of other properties—has exposed the keys to its kingdom on an unsecured Amazon S3 server.
A security researcher working for California-based cyber resiliency firm UpGuard has recently discovered a wide-open, public-facing misconfigured Amazon Web Server S3 cloud storage bucket containing roughly a gigabyte's worth of credentials and configuration files for the backend of dozens of Viacom properties. These exposed credentials discovered by UpGuard researcher Chris Vickery would have been enough for hackers to take down Viacom's internal IT infrastructure and internet presence, allowing them to access cloud servers belonging to MTV, Paramount Pictures and Nickelodeon. Among the data exposed in the leak was Viacom's master key to its Amazon Web Services account, and the credentials required to build and maintain Viacom servers across its many subsidiaries and dozens of brands.
Alert Regarding Vulnerabilities in Apache Tomcat. Alert Regarding Vulnerabilities in Apache Tomcat last update: 2017-09-20 JPCERT-AT-2017-0038 JPCERT/CC 2017-09-20 <<< JPCERT/CC Alert 2017-09-20 >>> Alert Regarding Vulnerabilities in Apache Tomcat I. Overview On September 19, 2017 (US time), the Apache Software Foundation released information on vulnerabilities (CVE-2017-12615 and CVE-2017-12616) in Apache Tomcat. In the vulnerability CVE-2017-12615, when running on Windows with HTTP PUTs enabled (e.g. via setting the readonly initialisation parameter of the Default to false), arbitrary code may be executed remotely on the server that runs Apache Tomcat by using a specially crafted request. In the vulnerability CVE-2017-12616, when using VirtualDirContext, it was possible to bypass security constraints and/or view the source code of JSPs for resources served by the VirtualDirContext using a specially crafted request.
CCleaner 5.33 32 bits piégé par une backdoor, plusieurs millions d'infections. Du code malicieux dans des paquets Python ? Critical Flaw in Apache Struts2 Lets Hackers Take Over Web Servers. Security researchers have discovered a critical remote code execution vulnerability in the popular Apache Struts web application framework, allowing a remote attacker to run malicious code on the affected servers. Apache Struts is a free, open-source, Model-View-Controller (MVC) framework for developing web applications in the Java programming language, which supports REST, AJAX, and JSON.
The vulnerability (CVE-2017-9805) is a programming blunder that resides in the way Struts processes data from an untrusted source. Specifically, Struts REST plugin fails to handle XML payloads while deserializing them properly. All versions of Apache Struts since 2008 (from Struts 2.5 to Struts 2.5.12) are affected, leaving all web applications using the framework’s REST plugin vulnerable to remote attackers. "On top of that, [the vulnerability] is incredibly easy for an attacker to exploit this weakness: all you need is a web browser," Man Yue Mo, an LGTM security researcher said.
CobianRAT, le logiciel qui permet aux pirates de pirater des pirates. Taringa: Over 28 Million Users' Data Exposed in Massive Data Breach. Exclusive — If you have an account on Taringa, also known as "The Latin American Reddit," your account details may have compromised in a massive data breach that leaked login details of almost all of its over 28 million users. Taringa is a popluar social network geared toward Latin American users, who create and share thousands of posts every day on general interest topics like life hacks, tutorials, recipes, reviews, and art.
The Hacker News has been informed by LeakBase, a breach notification service, who has obtained a copy of the hacked database containing details on 28,722,877 accounts, which includes usernames, email addresses and hashed passwords for Taringa users. The hashed passwords use an ageing algorithm called MD5 – which has been considered outdated even before 2012 – that can easily be cracked, making Taringa users open to hackers.
Wanna know how weak is MD5? Les bugs touchant les derniers correctifs de Microsoft inquiètent les utilisateurs. Safety Communications > Firmware Update to Address Cybersecurity Vulnerabilities Identified in Abbott's (formerly St. Jude Medical's) Implantable Cardiac Pacemakers: FDA Safety Communication. Date Issued. KeePassXC ajoute le support natif des Yubikey pour protéger l'accès à vos mots de passe. Un hacker britannique extradé. FDA Recalls Nearly Half a Million Pacemakers Over Hacking Fears. Kaspersky Lab découvre le bug d'Instagram à l'origine du vol de données. ZATAZ L'Université Lyon 2 corrige une fuite visant certains de ses étudiants - ZATAZ.
DOC 578d579d1f000000 A. AngelFire: CIA Malware Infects System Boot Sector to Hack Windows PCs. Instagram Suffers Data Breach! Hacker Stole Contact Info of High-Profile Users. Oops! WikiLeaks Website Defaced By OurMine. Un spambot s'appuie sur 711 millions d'entrées pour diffuser le malware bancaire Ursnif, vérifiez que votre compte n'en fait pas partie. Le phishing empoisonne toujours autant la vie des RSSI. Une entreprise française veut attaquer l'accord Open Bar entre la Défense et Microsoft. Bitdefender Home Scanner : un outil gratuit pour détecter les vulnérabilités de votre maison connectée. T411 : 7 millions d'euros par an, 6 interpellations, 3 ans d'enquête internationale - Politique.
Le FBI s'invite par surprise dans le déchiffrement d'un iPhone 6. Étude - PME & ETI : Comment combattent-elles les ransomwares ? Les enseignements à tirer de Dyn et de Mirai ou comment vaincre les botnets IoT. What Being a Female Hacker Is Really Like. Facebook Messenger : Kaspersky lance une alerte au malware. Director of Mexican Anti-Corruption Group Targeted with NSO Spyware. Gazer: A New Backdoor Targets Ministries and Embassies Worldwide. Someone Hacked Selena Gomez Instagram, Shared Nude Justin Bieber Photos. Comment s'acheter un MacBook pour 1 dollar via à une faille SAP. Using LabVIEW? Unpatched Flaw Allows Hackers to Hijack Your Computer. iPhone 7 : Il pirate le smartphone avec un simple boîtier (Vidéo) ! Étude - PME & ETI : Comment combattent-elles les ransomwares ? Beware! Viral Sarahah App Secretly Steals Your Entire Contact List. ZATAZ Fuite de données colmatée pour Location U - ZATAZ.
Bitcoin Ethereum: How Blockchain Tech Is Revolutionizing Business. Sans titre. 175.000 caméras IoT vulnérables : la sécurité sans défense - ZDNet. The Hacker Search Engine "Shodan" Is The World's Scariest Search Engine » TechWorm. Shodan : un moteur de recherche rêvé pour cybercriminels, et les responsables IoT - ZDNet. VeraCrypt 1.2x implémente un bureau sécurisé pour éviter les keyloggers : comment l'activer. Enquête : comment les apps Figaro, L'Équipe ou Closer participent au pistage de 10 millions de Français - Politique.
A Company Offers $500,000 For Secure Messaging Apps Zero-Day Exploits. Google Play Store : des portes dérobées découvertes dans des centaines d’applis. Here's How CIA Spies On Its Intelligence Liaison Partners Around the World. Chromium Blog: Run multiple versions of Chrome side-by-side. Avast dévoile les applications les plus gourmandes sous Android. Simple Exploit Allows Attackers to Modify Email Content — Even After It's Sent! Over 500 Android Apps On Google Play Store Found Spying On 100 Million Users. Le scandaleux logiciel espion vendu pour «savoir si son fils est gay» Faketoken : ce trojan pourrait gâcher vos déplacements en taxi. ZATAZ Un policier Belge aurait participé au business du darknet - ZATAZ. Fappening 2017: More Celebrity Nude Photos Hacked and Leaked Online. DDoS Attacks on the Rise Again: Akamai - Infosecurity Magazine. Sony PlayStation Social Media Accounts Hacked; Claims PSN Database Breach.
Faketoken : Découverte d'un trojan bancaire Android. iOS 11 : une fonction pour court-circuiter Touch ID - ZDNet. Doctor Implanted 6 MicroChips Under His Skin to Unlock Doors and Secure Data. Warning: Enigma Hacked; Over $470,000 in Ethereum Stolen So Far. Google Chrome : Attention aux extensions compromises par des pirates. Une cyberattaque visant les participants du G20 mise à jour par Proofpoint. Android Trojan Now Targets Non-Banking Apps that Require Card Payments. Smart Devices Can Be Hijacked to Track Your Body Movements And Activities Remotely.
New Snowden Doc Exposes How NSA's Facility in Australia Aids Drone Strikes. Orange et SFR corrigent la faille WPS de leurs box Internet - ZATAZ. Avec 450€, pirater un iPhone devient un jeu d'enfant - ZATAZ. Two Critical Zero-Day Flaws Disclosed in Foxit PDF Reader. Dumbo : Un malware utilisé par la CIA dévoilé par WikiLeaks #Vault7. Une cyberattaque visant les participants du G20 mise à jour par Proofpoint. Motorola veut inventer l'écran de smartphone qui se répare tout seul. Android Trojan Now Targets Non-Banking Apps that Require Card Payments. DarkHotel, un groupe de hackers qui s’attaque au Wi-Fi des hôtels de luxe. Snowden : les lois anti-VPN constituent une « atteinte aux droits de l’homme » Renseignement : à Paris, un matériel d’écoute si sophistiqué que personne ne peut s’en servir.