

Que-font-les-pirates-informatiques-aujourdhui. INFORMATION : la publicité diffusée sur ce site est l'unique source de revenus, permettant de vous proposer gratuitement ce contenu en finançant le travail journalistique.
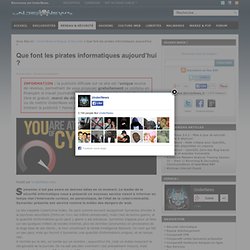
Si vous souhaitez la survie d'un web libre et gratuit, merci de désactiver votre bloqueur de publicité ou de mettre UnderNews en liste blanche. Vous souhaitez aider tout en limitant la publicité ? Faites un don ! En savoir plus Publié par UnderNews Actu Symantec n’est pas avare en bonnes idées en ce moment. Le site s’appelle CyberCrime Index. Prenons le spam, illustré ci-contre. Les courbes sur l’année permettent de voir également que les nombreuses arrestations de pirates et le démantèlement de leurs larges réseaux de botnets l’été dernier a eu un réel effet, puisqu’en juillet il y a eu un pic à 234 milliards de spams envoyés en une journée, alors qu’on est aujourd’hui autour de 55 milliards. On vous laisse vous balader sur le site CyberCrime Index pour en apprendre plus. Source : Comment Ça Marche Loading ...
#1 Daily Source for Hacking News, Data Leaks, Account Leaks and much more.
Joomla. Tuts 4 You: Downloads. Grid. Packet Storm ? Full Disclosure Information Security. #!/bin/the hacker's choice - THC. SecurityReason.com - Our Reason is Security. Help Net Security. Hak5 – Technolust since 2005. Security – SnakeOil Labs. Password eXploitation Class. Password Exploitation Class This is a class we gave for the Kentuckiana ISSA on the the subject of password exploitation.
The Password Exploitation Class was put on as a charity event for the Matthew Shoemaker Memorial Fund ( ). The speakers were Dakykilla, Purehate_ and Irongeek. Lots of password finding and crack topics were covered. Hashcat, OCLHashcat, Cain, SAMDump2, Nir's Password Recovery Tools, Password Renew, Backtrack 4 R1, UBCD4Win and much more. My slides in PDF and PPTX format. The class video has been split into three parts: Part 1: Topics include: Why exploit local passwords? Download: Part 2: The best single video out there for showing Hashcat and OCLHashcat. PenTestIT ? Your source for Information Security Related information! VulnerabilityAssessment.co.uk. Community Malicious code research and analysis. 1337day Inj3ct0r Exploit Database : vulnerability : 0day : shellcode by Inj3ct0r Team. PiraX. The Hackers News. Hack This Zine. Also check out Hackbloc's other publications There is also a mirror of all of our issues at HackThisSite and Textfiles.com {*style:<b>#13: People, Like Information, Want to be Free </b>*} Download for Reading: pdf Editorial: People, Like Information, Want to be Free Actions Speak Louder than Words (anon attacks the pigs!)
Border Haunt Action Reportback An Adventure in Creative Security Culture Hacker Profiles- Making of a Female Hacktivist - an interview with Synch Easy CD/DVD Backup w/ Linux BitCoin: Dangerous to Surveillance State, Useful to Activists Update on Bradley Manning Classifieds ...and a bunch of hilarious letters to our staff! {*style:<b>#12: Tools from Beyond the Electronic Frontier Editorial: Reporting from Somewhere Beyond the Electronic Frontier Interview with TorrentFreak.com Solidarity with Bradley Manning FBI Makes Big Media Splash While Attempting to Prosecute Anonymous Court Documents in Case Against Goatse Hackers Reveal Unknown Snitches Thoughts on Hackerspaces Phone Home Script News.
Security Alert System - BugSearch.net. Exploits Database by Offensive Security. Exploit Search. Indonesian Exploits Archive.
Online Tools. Coding. Blogs. Forums. Dorks. Ethical Hacking, Penetration Testing & Computer Security. Wappalyzer - Home. Infosec Island.