

Fullnews. Setting up public key authentication over SSH. January 18, 2006.
TOR howto: Using TOR through a ssh-tunnel « Blog of too many things. Note: This posting is heavily outdated.
Please use the Tor Browser Bundle! I’m a fan of TOR, the anonymizing network. It let’s me access the Internet anonymously and I don’t need to fear that anyone might use the data from their big Lawful Interception Points against me. It also prevents evil companies from correlating my web-surfing behaviour and connecting it to my IP-address. I ain’t no criminal, i just don’t like it when people assume by default that I’m maybe a criminal, become one in the future, or use data which show my personal surfing-habits. SSH, The Secure Shell: The Definitive Guide. By Daniel J.
Barrett and Richard E. SilvermanISBN: 0-596-00011-1First edition, published February 2001. (See the catalog page for this book.) Search the text of SSH, The Secure Shell: The Definitive Guide. Table of Contents. Password less ssh login. November 10 First we will see, how to install the openssh in your ubuntu machine. 1) Type the below command in your console 2) Once it get installed, see whether you have the sshd dameon is running in your system or not.
SSH Tutorial for Linux - Support Documentation. This document covers the SSH client on the Linux Operating System and other OSes that use OpenSSH.

If you use Windows, please read the document SSH Tutorial for Windows If you use Mac OS X or other Unix based system, you should already have OpenSSH installed and can use this document as a reference. This article is one of the top tutorials covering SSH on the Internet. It was originally written back in 1999 and was completely revised in 2006 to include new and more accurate information. As of October, 2008, it has been read by over 473,600 people and consistently appears at the top of Google's search results for SSH Tutorial and Linux SSH. Accessing Your Data — WebFaction User Guide. Aside from the control panel, there are two other key ways to access your account and data.
OpenSSH Secure "how to" (ssh_config sshd_config) @ Calomel.org - Open Source Research and Reference. Home RSS Search September 10, 2013 OpenSSH is a set of utilities to allow you to connect to a remote machine through an encrypted tunnel.

You can use it as a terminal connection or to tunnel any data through a VPN interface. OpenSSH is a FREE version of the SSH suite of network connectivity tools that increasing numbers of people on the Internet are coming to rely on. Many users of telnet, rlogin, ftp, and other such programs might not realize that their password is transmitted across the Internet unencrypted, but it is. Most operating systems come with one version or another of OpenSSH. SECURITY NOTE: Notice that we have specified the "Ciphers" for the client and server config files. SSH public keys. From Noah.org SSH Key Generation Overview with no password This shows how to use unencrypted public keys for logging in to a remote SSH server without a password.
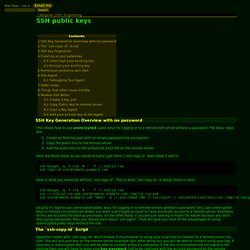
The basic steps are: Create an RSA key-pair with an empty password (no encryption). Copy the public key to the remote server. Here are those steps as you would actually type them (`ssh-copy-id` does steps 2 and 3): Ubuntu Linux: Start / Stop / Restart OpenSSH ( SSH ) Server. I need to provide a remote access to my Ubuntu Linux based server.

How do I start / stop OR restart the ssh server under Ubuntu Linux operating system using command line options? You need to run a script called /etc/init.d/ssh to stop, start, and restart the OpenSSH server. Setup OpenSSH Server on Ubuntu Linux. SSH/OpenSSH/Configuring. Parent page: Internet and Networking >> SSH Once you have installed an OpenSSH server, sudo apt-get install openssh-server.
7 Cool things you can do with SSH. It’s been a while since I’ve written an article, so I thought I’d make it a big one before I get bogged down with College work again. Here we go… SSH (Secure Shell) is often thought of as a secure replacement to Telnet, that is only really capable of remote login, which, while cool in itself is far from SSH’s true potential. The truth is, SSH is one of the most powerful and extensible programs I have ever used, it can be used for any number of wildly different things, most of which I will demonstrate in this article.
17.7. More Than a Secure Shell. 17.7.

More Than a Secure Shell A secure command line interface is just the beginning of the many ways SSH can be used. Given the proper amount of bandwidth, X11 sessions can be directed over an SSH channel. Or, by using TCP/IP forwarding, previously insecure port connections between systems can be mapped to specific SSH channels. Top 20 OpenSSH Server Best Security Practices. OpenSSH is the implementation of the SSH protocol. OpenSSH is recommended for remote login, making backups, remote file transfer via scp or sftp, and much more. SSH is perfect to keep confidentiality and integrity for data exchanged between two networks and systems. However, the main advantage is server authentication, through the use of public key cryptography. How to connect to a computer through VNC using SSH.
Beginning SSH on Ubuntu. SSH/OpenSSH/Configuring. Secure Shell. Secure Shell (SSH) is a network protocol that allows data to be exchanged over a secure channel between two computers. Encryption provides confidentiality and integrity of data. SSH uses public-key cryptography to authenticate the remote computer and allow the remote computer to authenticate the user, if necessary. SSH is typically used to log into a remote machine and execute commands, but it also supports tunneling, forwarding arbitrary TCP ports and X11 connections; file transfer can be accomplished using the associated SFTP or SCP protocols. An SSH server, by default, listens on the standard TCP port 22.