

Open Source Storage Server: 60 Hard Drives 480TB Storage. Vaults: Zettabyte-Scale Cloud Storage Architecture. We are thrilled to share the results of a project that has engaged the Backblaze engineering team for the last year: Backblaze Vaults, a major step forward in our cloud storage service’s technology stack.
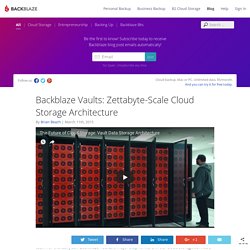
Currently Backblaze stores over 150 petabytes of data and has recovered over 10 billion files for customers of our cloud backup service. The new storage Vaults will form the core of our cloud services moving forward. The Fourth Generation Petabox. Waiting for your upload or download….
Behind all the cool stuff users see on archive.org is some serious hardware. Mininet exercise. Open-Source Routing and Network Simulation. Simple Router · mininet/mininet Wiki. ##Introduction In this lab assignment you will be writing a simple router with a static routing table.
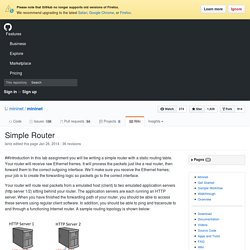
Your router will receive raw Ethernet frames. It will process the packets just like a real router, then forward them to the correct outgoing interface. We’ll make sure you receive the Ethernet frames; your job is to create the forwarding logic so packets go to the correct interface. Your router will route real packets from a emulated host (client) to two emulated application servers (http server 1/2) sitting behind your router.
The application servers are each running an HTTP server. Network Simulator Available Lab Exercises. EN0746 Computer Network Implementation. The aim of this module is to promote graduate-level study of topics in computer network implementation.

As a student, you will apply modern principles, software, techniques and tools to the investigation, analysis and evaluation of computer network implementations. You will also become familiar with topics at the forefront of current networking research. One of the features of the module is that you are encouraged to work directly with primary sources, including ISO standards, RFC's and original research papers. Google Groupes. On Sunday 12 Feb 2017 at 22:26, Alvaro Miranda Aguilera wrote: > hello.
Building A Billion User Load Balancer. Kubernetes: Kompose Helps Developers Move Docker Compose Files to Kubernetes. Editor's note: today's post is by Charlie Drage, Software Engineer at Red Hat giving an update about the Kubernetes project Kompose.

I'm pleased to announce that Kompose, a conversion tool for developers to transition Docker Compose applications to Kubernetes, has graduated from the Kubernetes Incubator to become an official part of the project. Since our first commit on June 27, 2016, Kompose has achieved 13 releases over 851 commits, gaining 21 contributors since the inception of the project. CoovaChilli, an open source captive portal access controller. Everything is an HTTPS interface – Serverless Zone. In the Linux world everything is file, in the Serverless world everything is an HTTPS interface.
Serverless applications by their nature are heavily decomposed into a variety of services, such as autonomous functions, object storage, authentication services, document databases, and pub/sub message queues. The interfaces between these services are typically HTTPS. When you’re using the AWS SDK to call an AWS services, the interface it’s calling under the hood is an HTTPS interface.
This is true for the majority of cloud platforms, with some alternative protocols occasionally being used (WebSockets and MQTT) in specific use cases. In the same way that in Linux you can access all the resources of the underlying machine through the file system, in a serverless world you can access all the resources of the underlying cloud platform through an HTTPS interface.
Amazon Web Services Simple Monthly Calculator. Software Defined Radio, SDR. Devil Linux - Home. Ansible Webinars and Training I Ansible. CVD IWANDeployment APR17. Systems Engineering and Operations Newsletter - O'Reilly Media. DevOps for Media & Entertainment eBook. Review: Windows Server containers are new and strange. Google not Amazon — Make fantastic savings in a serverless world. Site Reliability Engineer: Don’t fall victim to the bias blind spot. To ensure websites and applications deliver consistently excellent speed and availability, some organizations are adopting Google’s Site Reliability Engineering (SRE) model.
In this model, a Site Reliability Engineer (SRE) – usually someone with both development and IT Ops experience – institutes clear-cut metrics to determine when a website or application is production-ready from a user performance perspective. This helps reduce friction that often exists between the “dev” and “ops” sides of organizations.
More specifically, metrics can eliminate the conflict between developers’ desire to “Ship it!” Cluster Schedulers – Cindy Sridharan – Medium. This post aims to understand: 1. the purpose of schedulers the way they were originally envisaged and developed at Google2. how well (or not) they translate to solve the problems of the rest of us3. why they come in handy even when not running “at scale”4. the challenges of retrofitting schedulers into existing infrastructures5. running hybrid deployment artifacts with schedulers6. why where I work we chose Nomad over Kubernetes7. the problems yet to be solved8. the new problems these new tools introduce9. what the future holds for us.
Preventing cascading failures in a global network. Welcome back.
Please sign in. Welcome back. {* #userInformationForm *} {* traditionalSignIn_emailAddress *} {* traditionalSignIn_password *} {* traditionalSignIn_signInButton *} {* /userInformationForm *} Please confirm the information below before signing in. {* #socialRegistrationForm *} {* socialRegistration_firstName *} {* socialRegistration_lastName *} {* socialRegistration_displayName *} {* socialRegistration_emailAddress *} {* providerName *} {* profileURL *} {* profilePreferredUsername *} {* profileIdentifier *} {* /socialRegistrationForm *} How to convert *.img to *.vmdk format? Industry Currents Blog. GitHub - WSO2Telco/AEP: Artifacts for application enablement platform. GitHub - facebookincubator/CommunityCellularManager: Tool for deploying, managing and controlling your Community Cellular Networks. OpenRepeater Project. Cognitive Radio Tutorial. - an overview or tutorial about the basics of Cognitive Radio detailing a definition, history, Cognitive radio technology, architecture and Cognitive Radio networks.
Cognitive radio (CR) is one of the new long term developments taking place and radio receiver and radio communications technology. After the Software Defined Radio (SDR) which is slowly becoming more of a reality, cognitive radio (CR) and cognitive radio technology will be the next major step forward enabling more effective radio communications systems to be developed. The idea for cognitive radio has come out of the need to utilise the radio spectrum more efficiently, and to be able to maintain the most efficient form of communication for the prevailing conditions.
Cognitive Radio Tutorial. Electronics Design RF Wireless. A great selection of whitepapers that can be downloaded covering a variety of topics associated with electronics including circuit design, wireless, cellular, connectivity, design . . . Check back regularly to see what new whitepapers are available for download from industry experts in their own field.
LTE Advanced Pro and Road to 5GChapter 1 of the new book by Dahlman et al on the latest cellular developments and current 5G status. Get this free download.mmWave The Battle of the Bands5G mobile communications will use mmWave for many short range wide band links - but which microwave band will be used? Chaos Engineering 101 – Production Ready – Medium. Say you’re developing a new web application — the next great thing everybody has been waiting for. After all the work you’ve done, it’s time to finally launch the service to the first customers. Now the hard question: How To Set Up Highly Available Web Servers with Keepalived and Floating IPs on Ubuntu 14.04. Introduction High availability is a function of system design that allows an application to automatically restart or reroute work to another capable system in the event of a failure.
In terms of servers, there are a few different technologies needed to set up a highly available system. There must be a component that can redirect the work and there must be a mechanism to monitor for failure and transition the system if an interruption is detected. Chapter 13. HTTP Clustering and Load Balancing. GitHub - kubernetes/minikube: Run Kubernetes locally. That CI/CD Thingy: Principles, Implementation & Tools. Event Foo: Designing for Results. Microsoft: Serverless computing with Azure Function in a DevOps Model. Space_15204355.
Space_1736706. Space_753668. And Rinda: Implementation and application of distributed Ruby and its parallel coordination mechanism. Hardware. Trigger Up to 20 Different Functions With Your Fingerprints. Tech Summit On-Demand - Microsoft Enterprise - English (en-us) SOLDER- DS&T Exploration Fund (EF 1617), A Mesh Networking Development Proposal. Building an InfoSec lab, on the cheap. APM for the Non-Java Guru: What leak? Mininet Walkthrough - Mininet. Teaching and Learning with Mininet · mininet/mininet Wiki. CS144: Introduction to Computer Networking. Understanding the Connected Home · GitBook. Open IoT. 16bpp.net: C# Networking/Preface. Editor's picks: Best tutorials on the power of Bluemix. WePay on Kubernetes: 'It Changed Our Business' Linux DHCP Server Configuration. Get started. Writing WebSocket servers - Web APIs. Subnetting Reference Sheet. How To Subnet. UDP port forwarding with socat · Matt Ryall. 6160.
Documentation/Networking - QEMU. The 7 Layers of the OSI Model - Webopedia Study Guide. Using the Windows Azure Content Delivery Network (CDN) SaltStack. Docker Crash Course. NGINX and NGINX Plus Admin Guide. Under the hood: Broadcasting live video to millions. Mininet: An Instant Virtual Network on your Laptop (or other PC) - Mininet. LogMeIn Hamachi²: User Manual. Clustered file system. Cisco Networking Pathway. Internetworking Basics. Networking Fundamentals Training – Microsoft Virtual Academy. The Gentleperson's Guide to Forum Spies.