

Must-watch video of EFF's Kurt Opsahl... - Electronic Frontier Foundation (EFF) Dianne Feinstein: NSA Would Never Abuse Its Powers Because It's 'Professional' NSA's Plan to Use Porn Habits to Discredit 'Radicalizers' The document, provided by NSA whistleblower Edward Snowden, identifies six targets, all Muslims, as “exemplars” of how “personal vulnerabilities” can be learned through electronic surveillance, and then exploited to undermine a target's credibility, reputation and authority.

(Public domain)New documents obtained by NSA whistleblower Edward Snowden and leaked to journalist Glenn Greenwald and the Huffington Post show that the spy agency made plans to use the online activities, including visits to pornographic sites and other habits, of so-called Muslim "radicalizers" in order to discredit their standing. "The NSA's operation is eerily similar to the FBI's operations under J. Edgar Hoover in the 1960s where the bureau used wiretapping to discover vulnerabilities, such as sexual activity, to 'neutralize' their targets.
" –James Bamford, journalist According to the reporting: And Greenwald subsequently made note: LOVEINT. LOVEINT is the practice of intelligence service employees making use of their extensive monitoring capabilities to spy on their love interest or spouse.
The term was coined in resemblance to intelligence terminology such as SIGINT, COMINT or HUMINT. National Security Agency[edit] The term LOVEINT originated at the NSA, where approximately one such incident has occurred every year. In 2013, eight had been reported in the past decade, and they are the lion's share of unauthorized accesses reported by the NSA.[1] Most incidents are self-reported, for example during a polygraph test. Timeline of quantum computing. NSA to Build Quantum Computer to Crack Encryption. Tailored Access Operations. A reference to Tailored Access Operations in an XKeyscore slide The Office of Tailored Access Operations (TAO) is a cyber-warfare intelligence-gathering unit of the National Security Agency (NSA).
It has been active since at least circa 1998.[1][2] TAO identifies, monitors, infiltrates, and gathers intelligence on computer systems being used by entities foreign to the United States.[3][4][5][6] The NSA terms these activities "computer network exploitation". TAO is reportedly "now the largest and arguably the most important component of the NSA's huge Signal Intelligence (SIGINT) Directorate, consisting [more than] 1,000 military and civilian computer hackers, intelligence analysts, targeting specialists, computer hardware and software designers, and electrical engineers. "[1] Physical locations[edit] TAO's headquarters are termed the Remote Operations Center (ROC) and are based at Fort Meade, Maryland.
Organization[edit] Introducing Genie, the NSA's $652 million botnet. One of the scariest tools in a hacker's toolbox is a botnet, which lets someone infect scores of other computers with malware that allows the hacker to send out commands en masse.
The National Security Agency has one. It's named Genie. At least it was, as the latest evidence we have of such a program is from 2011. Your Internet. Your Internet news. How The NSA Pulls Off Man-In-The-Middle Attacks: With Help From The Telcos. We already covered the latest Guardian report on the NSA and GCHQ's attempts to compromise Tor. While those have failed to directly break Tor, they were more successful effectively exploiting vulnerabilities in Firefox to target certain Tor users.
Edward Snowden Reveals 'Quantum Insert': NSA And GCHQ Used Fake LinkedIn And Slashdot Pages To Install Spyware. How the NSA Thinks About Secrecy and Risk - Bruce Schneier. At this point, the agency has to assume that all of its operations will become public, probably sooner than it would like. Tailored Access Operations. A reference to Tailored Access Operations in an XKeyscore slide The Office of Tailored Access Operations (TAO) is a cyber-warfare intelligence-gathering unit of the National Security Agency (NSA).
It has been active since at least circa 1998.[1][2] TAO identifies, monitors, infiltrates, and gathers intelligence on computer systems being used by entities foreign to the United States.[3][4][5][6] The NSA terms these activities "computer network exploitation". TAO is reportedly "now the largest and arguably the most important component of the NSA's huge Signal Intelligence (SIGINT) Directorate, consisting [more than] 1,000 military and civilian computer hackers, intelligence analysts, targeting specialists, computer hardware and software designers, and electrical engineers.
"[1] Physical locations[edit] TAO's headquarters are termed the Remote Operations Center (ROC) and are based at Fort Meade, Maryland. Organization[edit] QUANTUM attacks[edit] QUANTUMCOOKIE attack[edit] NSA caught with its hand in Google's (browser) cookie jar. Ads that hound you from site to site don't seem quite so heinous in the wake of Tuesday's browser cookie-based revelation.
The National Security Agency is reportedly using a particular kind of tracking cookie from Google to identify and track potential hacking targets. The NSA is also grabbing location data from third-party advertisers delivering ads to mobile apps, according to The Washington Post. The latest leaks about the NSA's surveillance activities come once again from the trove of documents leaked by former NSA contractor, Edward Snowden.
If you don't know what a cookie is, it is a small piece of text deposited by a website into your browser. Cookies can be used for handy things like keeping you logged into Facebook even if you shut down your PC, or to help a web app such as Google Docs function correctly. Google stores a number of cookies on your computer whenever you visit one of the company's sites or even a non-Google site with embedded Google elements in it, such as a map. Bullrun (decryption program) FLYING PIG: The NSA Is Running Man In The Middle Attacks Imitating Google's Servers. Glyn mentioned this in his post yesterday about the NSA leaks showing direct economic espionage, but with so many other important points in that story, it got a little buried.

One of the key revelations was about a GCHQ program called "FLYING PIG" which is the first time I can recall it being clearly stated that the NSA or GCHQ has been running man-in-the-middle attacks on internet services like Google. This slide makes it quite clear that GCHQ or NSA impersonates Google servers: <a href=" Mitm Google (PDF)</a><br /><a href=" Mitm Google (Text)</a> NSA slides explain the PRISM data-collection program. The top-secret PRISM program allows the U.S. intelligence community to gain access from nine Internet companies to a wide range of digital information, including e-mails and stored data, on foreign targets operating outside the United States.

The program is court-approved but does not require individual warrants. NSA stores metadata of millions of web users for up to a year, secret files show. The National Security Agency is storing the online metadata of millions of internet users for up to a year, regardless of whether or not they are persons of interest to the agency, top secret documents reveal. Metadata provides a record of almost anything a user does online, from browsing history – such as map searches and websites visited – to account details, email activity, and even some account passwords. This can be used to build a detailed picture of an individual's life. The Obama administration has repeatedly stated that the NSA keeps only the content of messages and communications of people it is intentionally targeting – but internal documents reveal the agency retains vast amounts of metadata.
An introductory guide to digital network intelligence for NSA field agents, included in documents disclosed by former contractor Edward Snowden, describes the agency's metadata repository, codenamed Marina. Secret court lets NSA extend its trawl of Verizon customers' phone records. The National Security Agency has been allowed to extend its dragnet of the telephone records of millions of US customers of Verizon through a court order issued by the secret court that oversees surveillance.
In an unprecedented move prompted by the Guardian's disclosure in June of the NSA's indiscriminate collection of Verizon metadata, the Office of the Director of National Intelligence (ODNI) has publicly revealed that the scheme has been extended yet again. The statement does not mention Verizon by name, nor make clear how long the extension lasts for, but it is likely to span a further three months in line with previous routine orders from the secret Foreign Intelligence Surveillance Court (Fisa).
NSA broke privacy rules thousands of times per year, audit finds. The National Security Agency has broken privacy rules or overstepped its legal authority thousands of times each year since Congress granted the agency broad new powers in 2008, according to an internal audit and other top-secret documents.
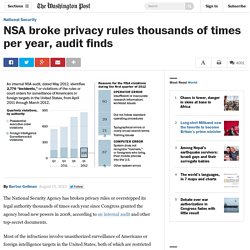
Most of the infractions involve unauthorized surveillance of Americans or foreign intelligence targets in the United States, both of which are restricted by statute and executive order. They range from significant violations of law to typographical errors that resulted in unintended interception of U.S. e-mails and telephone calls. The documents, provided earlier this summer to The Washington Post by former NSA contractor Edward Snowden, include a level of detail and analysis that is not routinely shared with Congress or the special court that oversees surveillance.
The top secret rules that allow NSA to use US data without a warrant. Top secret documents submitted to the court that oversees surveillance by US intelligence agencies show the judges have signed off on broad orders which allow the NSA to make use of information "inadvertently" collected from domestic US communications without a warrant. United States Foreign Intelligence Surveillance Court. Everything We Know About NSA Spying: "Through a PRISM, Darkly" - Kurt Opsahl at CCC. Section summary of the Patriot Act, Title II. President George W. Protect America Act. Foreign Intelligence Surveillance Act of 1978 Amendments Act of 2008. NSA Reportedly Changing Section 702 Of The FISA Amendments Act To Search US Citizens’ Communications. Foreign Intelligence Surveillance Act. The Foreign Intelligence Surveillance Act of 1978 ("FISA" Pub.L. 95–511, 92 Stat. 1783, 50 U.S.C. ch. 36) is a United States federal law which prescribes procedures for the physical and electronic surveillance and collection of "foreign intelligence information" between "foreign powers" and "agents of foreign powers" (which may include American citizens and permanent residents suspected of espionage or terrorism).[1] The law does not apply outside the United States.
It has been repeatedly amended since the September 11 attacks. §Subsequent amendments[edit] Omnibus Crime Control and Safe Streets Act of 1968. The Omnibus Crime Control and Safe Streets Act of 1968 (Pub.L. 90–351, 82 Stat. 197, enacted June 19, 1968, codified at 42 U.S.C. § 3711) was legislation passed by the Congress of the United States that established the Law Enforcement Assistance Administration (LEAA).
42 U.S. Code § 3711 - Establishment of Office of Justice Programs. Title 42 of the United States Code. Electronic Communications Privacy Act. The ECPA also added new provisions prohibiting access to stored electronic communications, i.e., the Stored Communications Act,18 U.S.C. §§ 2701-12. United States Statutes at Large. 82 Stat. 197 - An Act to assist State and local governments in reducing the incidence of crime, to increase the effectiveness, fairness, and coordination of law enforcement and criminal justice systems at all levels of government, and for other purposes.
Browse Public and Private Laws. Law Enforcement Assistance Administration. The Law Enforcement Assistance Administration (LEAA) was a U.S. federal agency within the U.S. Dept. of Justice. It administered federal funding to state and local law enforcement agencies, and funded educational programs, research, state planning agencies, and local crime initiatives. United States Statutes at Large. Executive Order 12333.
It was amended by Executive Order 13355: Strengthened Management of the Intelligence Community, on August 27, 2004. On July 30, 2008, President Bush issued Executive Order 13470[2] amending Executive Order 12333 to strengthen the role of the DNI.[3][4] Electronic Communications Privacy Act. NSA warrantless surveillance (2001–07) Terrorist Surveillance Program. President's Surveillance Program. FASCIA (database) Stellar Wind (code name) 'EvilOlive, Transient Thurible, MoonLightPath...": The NSA's Active Internet Spy Programs. How the NSA is still harvesting your online data.
'EvilOlive, Transient Thurible, MoonLightPath...": The NSA's Active Internet Spy Programs. The Government's Word Games When Talking About NSA Domestic Spying. How the NSA's Domestic Spying Program Works. Room 641A. Utah Data Center. NSA reportedly collecting phone records of millions, though officials had denied holding 'data' on Americans.