

Trove 3.0.0. 概要 (Java Platform SE 6) Oracle Technology Network > Java Software Downloads View All Downloads Top Downloads New Downloads What's New Java in the Cloud: Rapidly develop and deploy Java business applications in the cloud.

Essential Links Developer Spotlight Java EE—the Most Lightweight Enterprise Framework? Blogs Technologies Contact Us About Oracle Cloud Events Top Actions News Key Topics Oracle Integrated Cloud Applications & Platform Services. Ⅿ Un article de Wikipédia, l'encyclopédie libre.
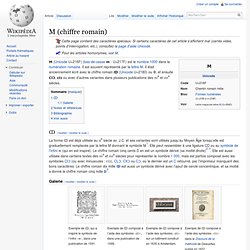
Cette page contient des caractères spéciaux. Si certains caractères de cet article s’affichent mal (carrés vides, points d’interrogation, etc.), consultez la page d’aide Unicode. Pour les articles homonymes, voir M. Exemple de ↀ, qui a inspiré le symbole de l’infini ‹ ∞ ›, dans une publication de 1591.Exemple de ↀ composé à l’aide des symboles ‹ clↄ ›, dans une publication de 1599.Exemple de ↀ composé à l’aide des symboles ‹ clↄ › sur un bâtiment construit en 1630 à Amsterdam.Exemple de ↀ composé à l’aide des symboles ‹ ⅽⅠↄ › dans le Discours de la méthode de Descartes publié en 1637.Exemple de ↀ composé à l’aide de ‹ CXↃ › dans le nombre 1596, dans une publication de 1715.Exemple de ↀ composé à l’aide de ‹ CIↃ › dans le nombre 1637, dans une publication de 1722.Exemple de ↀ composé à l’aide de ‹ CↃ › dans une publication de 1745. Cet article est partiellement ou en totalité issu de l'article intitulé « ↀ » (voir la liste des auteurs).
Secure Coding Guidelines for the Java Programming Language, Vers. Updated for Java SE 8 Document version: 5.1 Published: 02 April 2014 Last updated: 19 November 2015 Introduction One of the main design considerations for the Java platform is to provide a secure environment for executing mobile code.
Java comes with its own unique set of security challenges. While the Java security architecture [1] can protect users and systems from hostile programs downloaded over a network, it cannot defend against implementation bugs that occur in trusted code. Such bugs can inadvertently open the very holes that the security architecture was designed to contain, including access to files, printers, webcams, microphones, and the network from behind firewalls.
The choice of language system impacts the robustness of any software program. To minimize the likelihood of security vulnerabilities caused by programmer error, Java developers should adhere to recommended coding guidelines. 0 Fundamentals The following general principles apply throughout Java security. James Gosling: on the Java Road. Untitled. High performance access to file storage Google has published code for Java to reduce the amount of hand coding needed for commonly occurring or popular features in applications.
The search giant has slipped out its Google Collections Library 1.0, extending Sun Microsystems' existing Java Collection Framework. The code has already been tested in Google's GMail, Reader, Blogger, Docs & Spreadsheets, AdWords, and AdSense. The library includes new collection types for Multimap, Multiset, and Bitmap, a MapMaker builder for concurrent hash maps, and an Ordering collection Google described as "Comparator on steroids.
" You can read more here. Jared Levy, one of the primary creators with Google colleague Kevin Bourrillion, told JavaLobby the main benefit for developers is convenience. "The library's functionality simplifies your code so it's easier to write, read, and maintain," he told JavaLobby.