

Black Americans and encryption: the stakes are higher than Apple v FBI. When the FBI branded Martin Luther King Jr a “dangerous” threat to national security and began tapping his phones, it was part of a long history of spying on black activists in the United States.
News Investigation Finds Signs of Secret Phone Surveillance Across London. A VICE News investigation has found evidence that sophisticated surveillance equipment that spies on people's phones is being used across London, and uncovered a growing black market for the technology worldwide.
Signs of IMSI catchers — also known as stingrays or cell-site simulators — were found at several locations in the British capital, including UK parliament, a peaceful anti-austerity protest, and the Ecuadorian embassy. A former senior surveillance insider also confirmed to VICE News that they have been used by UK police. The portable devices are typically used by state law enforcement. They monitor thousands of phones at a time, and are capable of intercepting calls, text messages, and emails. Massive Hack of 70 Million Prisoner Phone Calls Indicates Violations of Attorney-Client Privilege. AN ENORMOUS CACHE of phone records obtained by The Intercept reveals a major breach of security at Securus Technologies, a leading provider of phone services inside the nation’s prisons and jails.

The materials — leaked via SecureDrop by an anonymous hacker who believes that Securus is violating the constitutional rights of inmates — comprise over 70 million records of phone calls, placed by prisoners to at least 37 states, in addition to links to downloadable recordings of the calls. GCHQ mass internet surveillance was unlawful, court rules. Mass surveillance of the internet by the British monitoring agency GCHQ was unlawful until the end of last year, the UK’s most secretive court has ruled.
The Investigatory Powers Tribunal (IPT) ruled on Friday that the agency’s access to intercepted information obtained by the US National Security Agency (NSA) breached human rights law. Human rights groups said the decision raised questions about the legality of intelligence-sharing operations between the UK and the US. The ruling appears to suggest that aspects of the operations were illegal for at least seven years – between 2007, when the Prism intercept programme was introduced, and 2014. UK intelligence agencies spying on lawyers in sensitive security cases. The intelligence services have routinely been intercepting legally privileged communications between lawyers and their clients in sensitive security cases, according to internal MI5, MI6 and GCHQ documents.
The information obtained may even have been exploited unlawfully and used by the agencies in the fighting of court cases in which they themselves are involved, the Investigatory Powers Tribunal (IPT) has been told, resulting in miscarriages of justice. Exchanges between lawyers and their clients enjoy a special protected status under the law. The Conservative MP David Davis, a former shadow home secretary, said past practice was to delete such material immediately if it was ever picked up. Amnesty International said the government was gaining “an unfair advantage akin to playing poker in a hall of mirrors”. Belhaj has been given permission to sue the government for his mistreatment. Who is Neustar? Brad Stone at the New York Times reports on an industry group working on a new platform for portable digital movie downloads: The [Digital Entertainment Content Ecosystem or DECE] is setting out to create a common digital standard that would let consumers buy or rent a digital video once and then play it on any device...
Under the proposed system, proof of digital purchases would be stored online in a so-called rights locker, and consumers would be permitted to play the movies they bought or rented on any DECE-compatible device. [DECE is] selecting Neustar, a company based in Sterling, Va., to create the online hub that will store records of people’s digital purchases, with their permission. Most consumers have likely never heard of Neustar, yet the firm plays an important role in the telecommunications industry, and has built a highly profitable business faciliating the disclosure of information regarding consumers' communications to law enforcement and intelligence agencies.
The executive order that led to mass spying, as told by NSA alumni. One thing sits at the heart of what many consider a surveillance state within the US today.
The problem does not begin with political systems that discourage transparency or technologies that can intercept everyday communications without notice. Like everything else in Washington, there’s a legal basis for what many believe is extreme government overreach—in this case, it's Executive Order 12333, issued in 1981. “12333 is used to target foreigners abroad, and collection happens outside the US," whistleblower John Tye, a former State Department official, told Ars recently. ICREACH: How the NSA Built Its Own Secret Google -The Intercept.
The National Security Agency is secretly providing data to nearly two dozen U.S. government agencies with a “Google-like” search engine built to share more than 850 billion records about phone calls, emails, cellphone locations, and internet chats, according to classified documents obtained by The Intercept.
The documents provide the first definitive evidence that the NSA has for years made massive amounts of surveillance data directly accessible to domestic law enforcement agencies. Planning documents for ICREACH, as the search engine is called, cite the Federal Bureau of Investigation and the Drug Enforcement Administration as key participants. NSA/GCHQ: The HACIENDA Program for Internet Colonization. Translations of this article are available in German, French, Italian and Spanish.
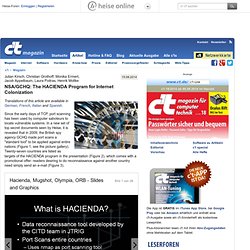
Since the early days of TCP, port scanning has been used by computer saboteurs to locate vulnerable systems. In a new set of top secret documents seen by Heise, it is revealed that in 2009, the British spy agency GCHQ made port scans a "standard tool" to be applied against entire nations (Figure 1, see the picture gallery). Twenty-seven countries are listed as targets of the HACIENDA program in the presentation (Figure 2), which comes with a promotional offer: readers desiring to do reconnaissance against another country need simply send an e-mail (Figure 3).
Schrodinger's Cat Video and the Death of Clear-Text. You Can Get Hacked Just By Watching This Cat Video on YouTube. Many otherwise well-informed people think they have to do something wrong, or stupid, or insecure to get hacked—like clicking on the wrong attachments, or browsing malicious websites.
People also think that the NSA and its international partners are the only ones who have turned the internet into a militarized zone. Leaked Docs Show Spyware Used to Snoop on U.S. Computers. Software created by the controversial U.K. based Gamma Group International was used to spy on computers that appear to be located in the United States, the U.K., Germany, Russia, Iran and Bahrain, according to a leaked trove of documents analyzed by ProPublica. It's not clear whether the surveillance was conducted by governments or private entities. Customer email addresses in the collection appeared to belong to a German surveillance company, an independent consultant in Dubai, the Bosnian and Hungarian Intelligence services, a Dutch law enforcement officer and the Qatari government.
NSA+Law.docx - unnecessary_and_disproportionate.pdf. International Principles on the Application of Human Rights to Communications Surveillance. Secrets, lies and Snowden's email: why I was forced to shut down Lavabit. My legal saga started last summer with a knock at the door, behind which stood two federal agents ready to to serve me with a court order requiring the installation of surveillance equipment on my company's network. My company, Lavabit, provided email services to 410,000 people – including Edward Snowden, according to news reports – and thrived by offering features specifically designed to protect the privacy and security of its customers. I had no choice but to consent to the installation of their device, which would hand the US government access to all of the messages – to and from all of my customers – as they travelled between their email accounts other providers on the Internet.
But that wasn't enough. Researchers Find 25 Countries Using Surveillance Software. NIS aquires supercomputer. OSLO/ RIO DE JANEIRO (Dagbladet): The Norwegian military intelligence service collects vast amounts of signal intelligence, known as «sigint». In Afghanistan alone NIS collected 33 million registrations from telecommunication during 30 days around Christmas 2012, according to their own revelations. Reference Note on Russian Communications Surveillance. Edward Snowden, perhaps under duress, recently participated in a call-in program where selected viewers can pose pre-screened questions directly to Vladimir Putin. Snowden asked President Putin, “Does Russia intercept, store or analyze in any way the communications of millions of individuals?” Putin denied Russian mass surveillance, saying “Thank God, our special services are strictly controlled by the state and society, and their activity is regulated by law.”
Don’t Listen to Google and Facebook: The Public-Private Surveillance Partnership Is Still Going Strong - Bruce Schneier. And real corporate security is still impossible. A surveillance camera outside Google's China headquarters in 2010 (Jason Lee / Reuters) If you’ve been reading the news recently, you might think that corporate America is doing its best to thwart NSA surveillance. Google just announced that it is encrypting Gmail when you access it from your computer or phone, and between data centers. Last week, Mark Zuckerberg personally called President Obama to complain about the NSA using Facebook as a means to hack computers, and Facebook's Chief Security Officer explained to reporters that the attack technique has not worked since last summer.
Moroccan website Mamfakinch targeted by government-grade spyware from Hacking Team? Necessary and Proportionate. Druckversion - Cover Story: How the NSA Targets Germany and Europe - SPIEGEL ONLINE - News - International. Spies Without Borders Series: Using Domestic Networks to Spy on the World. Global Dialogue on Governmental Extra-Territorial Surveillance. An International Perspective on FISA: No Protections, Little Oversight.
Universal, Self-Evident: I'm Not American but I Have Privacy Rights too, NSA. In a letter sent today to the United States Congress, an international coalition of non-profit organizations called upon the U.S. government to protect the privacy and freedoms of not only its citizens, but of people everywhere. As news of the alarmingly broad reach and scope of America’s surveillance program reverberates around the globe, now is the time for the United States to pass formal privacy safeguards to protect the billions of foreign Internet users whose communications are stored in U.S. servers or whose data travels across U.S. networks. EFF joined more than 50 NGOs—including European Digital Rights, Association For Progressive Communications, Access Now, WebWeWant Foundation, Center for Technology and Society (Brazil) and Thai Netizen Network—in signing the letter, which was organized through Best Bits , a global network of civil society organizations.
U.S. Foreign Intelligence: From Carte Blanche Surveillance to Weak [Domestic] Protections. International Customers: It's Time to Call on US Internet Companies to Demand Accountability and Transparency. This is a joint international campaign between EFF and Access Now. The Guardian and the Washington Post recently published slides that indicate that the US government’s National Security Agency (NSA) is engaged in mass surveillance of users around the world through a program called PRISM.
Using Domestic Networks to Spy on the World. Spying on the World From Domestic Soil: International Backlash. Edward Snowden Provides Information on NSA Cyber Spying & Hacking to Hong Kong Newspaper. Edward Snowden, the former National Security Agency (NSA) contractor who blew the whistle on secret US surveillance programs like PRISM, has provided details on United States government hacking and cyber-spying to a newspaper in Hong Kong. The South China Morning Post, which previously interviewed Snowden, was shown information that Snowden said indicated the US government had hacked into “Chinese mobile firms to steal millions of text messages.”
Expert Says Kiwis Under Constant Surveillance. Washington pushed EU to dilute data protection.
Stratfor. The Surveillance-Industrial Complex. Spy Files. Wikileaks docs reveal that governments use malware for surveillance. >Wikileaks - The Spy files. Thailand: $13 Million for Lese Majesty Web-taps. Occupy Wall Street's 'occucopter' – who's watching whom? Commentary on surveillance. Dangerous Cybercrime Treaty Pushes Surveillance and Secrecy Worldwide.
European Commission wants to immunize DHS collaborators in travel surveillance and control. India Eying Access To All Encrypted Services, Not Just Email - MediaNama. Aadhaar: Enrollment, Authentication & Beyond - MediaNama. Mass surveillance. US: surveillance state. Immigration - Surveillance in the Homeland. Police employ Predator drone spy planes on home front - latimes.com. Busted! Two New Fed GPS Trackers Found on SUV. No Warrant Needed for GPS Monitoring, Judge Rules. Tension grows between Calif. Muslims, FBI after informant infiltrates mosque. FOIA Documents Show FBI Illegally Collecting Intelligence Under Guise of “Community Outreach” NYPD CIA Anti-Terror Operations Conducted In Secret For Years. C.I.A. Examining Legality of Its Work With New York Police. For Anarchist, Details of Life as F.B.I. Target. Four More Years of Unchecked Spying, Surveillance and Secrecy. The always-expanding bipartisan Surveillance State - Glenn Greenwald.
House Committee Approves Bill Mandating That Internet Companies Spy on Their Users. House Advances Internet Surveillance Bill - Blog - OpenCongress. Whistle-Blower: Feds Have a Backdoor Into Wireless Carrier. Whistleblower: The NSA is Lying–U.S. Government Has Copies of Most of Your Emails. Detained in the U.S.: Filmmaker Laura Poitras Held, Questioned Some 40 Times at U.S. Airports. Exclusive: National Security Agency Whistleblower William Binney on Growing State Surveillance. "We Don’t Live in a Free Country": Jacob Appelbaum on Being Target of Widespread Gov’t Surveillance. EFF Surveillance Self-Defense Project. Expanding the Surveillance State. The FBI's Next Generation Identification: Bigger and Faster but Much Worse for Privacy.
The Law Enforcement Surveillance Reporting Gap by Christopher Soghoian. Wiretap Report 2011. Why Metadata Matters. F.B.I. Seeks Way to Wiretap Internet Messages. FBI Routinely Spying on You! F.B.I. Giving Agents New Powers in Revised Manual. FBI: We need wiretap-ready Web sites. DOJ Wants to Know Who’s Rejecting Your Friend Requests. Gonzales wants ISPs to save user data - Security - MSNBC.com. Big Brother on a budget: How Internet surveillance got so cheap. User Data Requests – Google Transparency Report. U.S. Government Requests For Google Users' Private Data Jump 37% In One Year. Government seeks to shut down NSA wiretapping lawsuit. Government Spies Illegally Bugged Kim Dotcom, Prime Minister Admits. Dotcom: Illegal spying revealed - National - NZ Herald News. Dotcom saga sucks in leaders, police, spies - National - NZ Herald News. Government Standards Agency “Strongly” Suggests Dropping its Own Encryption Standard.
NSA. The NSA Spying Machine: An Interactive Graphic. NSA surveillance everywhere. [liberationtech] Recent Der Spiegel coverage about the NSA and GCHQ. How the NSA is still harvesting your online data. XKeyscore: NSA tool collects 'nearly everything a user does on the internet' Exclusive: NSA pays £100m in secret funding for GCHQ. GCHQ and European spy agencies worked together on mass surveillance. Privacy International challenges GCHQ's unlawful hacking of computers, mobile phones.
German Intelligence Agencies Used NSA Spying Program. NSA Leaks Prompt Surveillance Dialogue in India. Internet & location privacy/security.