

U.S. fears science fiction-style sabotage in new wave of cyber attacks. By Associated Press Updated: 14:34 GMT, 24 October 2011 When a computer attack hobbled Iran's unfinished nuclear power plant last year, it was assumed to be a military-grade strike, the handiwork of elite hacking professionals with nation-state backing.
Yet for all its science-fiction sophistication, key elements have now been replicated in laboratory settings by security experts with little time, money or specialized skill. It is an alarming development that shows how technical advances are eroding the barrier that has long prevented computer assaults from leaping from the digital to the physical world.
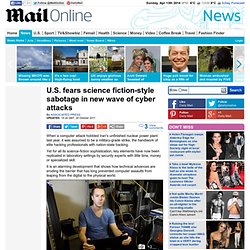
Exposed: Dillon Beresford said it took him just two months and $20,000 in equipment to find more than a dozen vulnerabilities in electronic controllers of the same type used in Iran The techniques demonstrated in recent months highlight the danger to operators of power plants, water systems and other critical infrastructure around the world. Scott Borg is director of the U.S. Researchers warn of new Stuxnet worm. 19 October 2011Last updated at 13:25 Stuxnet seems to have been designed to target uranium enrichment systems Researchers have found evidence that the Stuxnet worm, which alarmed governments around the world, could be about to regenerate.
Stuxnet Malware Analysis Paper. Table Of Contents 1.
Introduction Stuxnet is not only a new virus or worm but it's a new era of malware. This virus changed the meaning of malware and their goals. Environmental WikiLeaks: Greenpeace Crowdsources Research Of Secret BP Documents. Greenpeace is on a mission to expose major corporations and government agencies involved in shady activities--by posting thousands of Freedom of Information Act documents on highly publicized websites.
If Greenpeace's tactics work, the organization could change the way companies do business, or at least force them to better hide incriminating documents. Think of it as a government-enabled WikiLeaks for polluting companies. The first target: BP and all the companies involved in the Deepwater Horizon disaster. This week, Greenpeace posted approximately 30,000 pages of previously unseen documents related to the oil disaster on its new PolluterWatch Research site. "BP and the federal government tried to hide the true impacts of the biggest oil disaster in American history. Twitter. Google Translate. Stuxnet worm is the 'work of a national government agency' Allow Spotify content?
This article includes content provided by Spotify. We ask for your permission before anything is loaded, as they may be using cookies and other technologies. To view this content, click 'Allow and continue'. A computer worm which targets industrial and factory systems is almost certainly the work of a national government agency, security experts told the Guardian – but warn that it will be near-impossible to identify the culprit. Did The Stuxnet Worm Kill India’s INSAT-4B Satellite? - The Firewall - the world of security.
Stuxnet Worm Used Against Iran Was Tested in Israel. Nicholas Roberts for The New York Times Ralph Langner, an independent computer security expert, solved Stuxnet.

The Dimona complex in the Negev desert is famous as the heavily guarded heart of Israel’s never-acknowledged nuclear arms program, where neat rows of factories make atomic fuel for the arsenal. Over the past two years, according to intelligence and military experts familiar with its operations, Dimona has taken on a new, equally secret role — as a critical testing ground in a joint American and Israeli effort to undermine Iran’s efforts to make a bomb of its own. Behind Dimona’s barbed wire, the experts say, Israel has spun nuclear centrifuges virtually identical to Iran’s at Natanz, where Iranian scientists are struggling to enrich uranium. “To check out the worm, you have to know the machines,” said an American expert on nuclear intelligence.
The gruff Mr. Siemens says that program was part of routine efforts to secure its products against cyberattacks. A Declaration of Cyber-War. The secret of Stuxnet’s existence may have been blown, but clearly someone—someone whose timing was either spectacularly lucky or remarkably well informed—was sparing no effort to fight back.

Omens of Doomsday The volcanoes of Kamchatka were calling to Eugene Kaspersky. In the first week of July, the 45-year-old C.E.O. and co-founder of Kaspersky Lab, the world’s fourth-largest computer-security company, had been in his Moscow office, counting the minutes until his Siberian vacation would start, when one of his engineers, who had just received a call about Stuxnet from Microsoft, came rushing in, barely coherent: “Eugene, you don’t believe, something very frightening, frightening, frightening bad.” After VirusBlokAda found Stuxnet, and Microsoft announced its existence, Kaspersky Lab began researching the virus. Kaspersky shared its findings with Microsoft, and the two undertook an unusual collaboration to analyze the code. Anonymous hacktivists: We've got Stuxnet code. High performance access to file storage.
Atopiary: Anonymous' response on fut... Twitter. Iran urges IAEA to detect agents involved in Stuxnet attack. TEHRAN, June 13 (Xinhua) -- Deputy Secretary of the Supreme National Security Council of Iran Ali Bagheri called on the International Atomic Energy Agency (IAEA) on Monday to detect agents involved in Stuxnet computer worm plan, the semi-official ISNA news agency reported.
Addressing the closing session of the second International Nuclear Disarmament Conference in Tehran on Monday, Bagheri urged IAEA to form a fact-finding committee to detect agents involved in nuclear terrorism and operation of Stuxnet computer worm, said the report. In September, the Islamic Republic said that the computer worm of Stuxnet infected 30,000 IP addresses in Iran but the Iranian Foreign Ministry denied the reports that a cyber worm had damaged computer systems at the country's nuclear power plant.
Stuxnet VS BP & Transocean's Deepwater Horizon? Stuxnet. Warhead?
National security experts the world over currently have one new and weighty question on their mind. Who built Stuxnet, the infamous computer worm? And what’s its target? Iran itself has acknowledged that its nuclear program is suffering from a sophisticated attack by a novel and adaptive computer worm called Stuxnet. But then controversy begins. American and Israeli intelligence agree that Natanz is much more dangerous than Bushehr. Iran’s Natanz nuclear facility recovered quickly from Stuxnet cyberattack « VIENNA – In an underground chamber near the Iranian city of Natanz, a network of surveillance cameras offers the outside world a rare glimpse into Iran’s largest nuclear facility. The cameras were installed by U.N. inspectors to keep tabs on Iran’s nuclear progress, but last year they recorded something unexpected: workers hauling away crate after crate of broken equipment.
In a six-month period between late 2009 and last spring, U.N. officials watched in amazement as Iran dismantled more than 10 percent of the Natanz plant’s 9,000 centrifuge machines used to enrich uranium. 'Computer virus in Iran actually targeted larger nuclear facility' Clear evidence that Stuxnet targeted Natanz nuclear centrifuges. Was Stuxnet Aimed Specifically at Natanz? I am grateful to Alexander Glaser, a young German physicist associated with Princeton University’s engineering and public policy schools, for alerting me to an exceptionally authoritative analysis of the stuxnet computer worm that reputedly infiltrated and crippled industrial control systems in Iran. The article, by Frank Rieger, appeared in Germany’s Frankfurter Allgemeine Zeitung, on Sept. 22.
Rieger is chief technology officer at the cryptography firm GSMK, and his work on stuxnet has got a boost on the net from Bruce Schneier, the renowned internet security expert. Bear in mind, in this connection, that stuxnet is generally described as having been designed to infiltrate control systems made by Siemens, which is more or less Germany’s most important company. Stuxnet: Beware the Cyber War Boomerang? <br/><a href=" US News</a> | <a href=" Business News</a> Copy The leak prone governments of the United States and Israel seem to be competing to claim credit for a cyber war attack on Iran's nuclear weapons program, while officially refusing to confirm or deny their role in the "Stuxnet" computer worm.
Stuxnet, in case you have missed all the leaks, is the name the computer security companies have agreed on to denote the most sophisticated, most targeted computer attack ever seen. Iran was prime target of SCADA worm. News By Robert McMillan July 23, 2010 08:40 PM ET. Symantec: Stuxnet clues point to uranium enrichment target. Symantec researchers have figured out a key mystery to the Stuxnet worm code that strongly suggests it was designed to sabotage a uranium enrichment facility.
The program targets systems that have a frequency converter, which is a type of device that controls the speed of a motor, Eric Chien, technical director of Symantec Security Response, told CNET today. Symantec Connect Community Community. Anonymous Hackers Release Stuxnet Worm Online !
Stuxnet-like. Stuxnet attack forced Britain to rethink the cyber war. Us dodges the question of whether its military built stuxnet. AS ANY POLITICIAN KNOWS, sometimes the best way to not answer a question is to completely skirt around it, but sometimes being evasive can say more than a thousand words. Stuxnet could hurt world economic development, says Microsoft CEO - 10/5/2010. Tuesday 05 October 2010 12:04. Homemade Cyber Weapon On Par With Stuxnet Virus. Last week security researcher Dillon Beresford cancelled a scheduled presentation at the Takedown Conference about Supervisory Control and Data Acquisition (SCADA) exploit proof-of-concept after consulting with representatives from Siemens and the Department of Homeland Security over security concerns.
SCADA systems provide operations control for critical infrastructure and production networks including manufacturing facilities, refineries, hydroelectric and nuclear power plants, and the information in Beresford's presentation would have exposed previously undisclosed threats. Senior Defense official hedges on US involvement in Stuxnet. Researcher Finds Dangerous Security Holes in U.S. Power Plant & Factory Software - FoxNews.com.
Glaring holes in industrial software could allow hackers to gain partial control or even cause physical destruction at power plants, refineries and more -- further exposing the recently discovered weak underbelly of the nation’s infrastructure, a security analyst said. Dillon Beresford, a researcher who works for NSS Labs in Texas, identified the latest holes last Wednesday in the specialized Siemens software -- called "supervisory control and data acquisition" systems, or SCADA -- that runs industrial power plants, factories and other infrastructure. After Delay, Hacker to Show Flaws in Siemens Industrial Gear. A security researcher who says he's found serious problems with Siemens computers used in power plants and heavy industry is now expecting to go public with his research at the Black Hat security conference in Las Vegas.
Security failings at Siemens could lead to an attack worse than Stuxnet. Siemens Says it Will Fix SCADA Bugs. Siemens is working on a fix for some serious vulnerabilities recently discovered in its industrial control system products used to manage machines on the factory floor. The company said Thursday that it was testing patches for the issues, just one day after a security researcher, Dillon Beresford of NSS Labs, was forced to cancel a talk on the issue because of security concerns. NSS Labs had been working with Siemens and the U.S.
Chertoff Group: Israel Cyber-Attacks Iranian Nuke Plant With Stuxnet Computer Virus.