

Quantum Computing Playground. Paranoid about Your Bitcoin? This Wristband Protects It with Your Heartbeat. If the news anchor who flashed his Bitcoin gift certificate on air and had it promptly stolen taught us anything, it’s that you need to be careful where you store your budding digital currency.
On Tuesday, Toronto biometrics startup Bionym announced a new — and somewhat paranoid — way to make sure no one else can access your precious stash: a wearable Bitcoin wallet that can be accessed only by taking your unique electrocardiography, or ECG. You may have heard about the Nymi before, as it’s been passed around the tech blogs. It’s a high-tech wristband meant to act as a protector of many things aside from your digital currency: your credit card information, online logins, customer loyalty cards, frequent flier miles — you name it.
No matter what you’ve locked up behind the Nymi, no one can access it without your unique heartbeat.
Design Patterns. It has been highly influential to the field of software engineering and is regarded as an important source for object-oriented design theory and practice.

More than 500,000 copies have been sold in English and in 13 other languages. The authors are often referred to as the Gang of Four (GoF).[1] History[edit] Introduction, Chapter 1[edit] Chapter 1 is a discussion of object-oriented design techniques, based on the authors' experience, which they believe would lead to good object-oriented software design, including: clients remain unaware of the specific types of objects they use, as long as the object adheres to the interfaceclients remain unaware of the classes that implement these objects; clients only know about the abstract class(es) defining the interface. Iterator.dvi - iterator.pdf. Java - Iterator Pattern/Iterator Class - Code Review Beta - Stack Exchange. Iterator pattern. Iterator Pattern. Motivation One of the most common data structures in software development is what is generic called a collection.
A collection is just a grouping of some objects. They can have the same type or they can be all cast to a base type like object. A collection can be a list, an array, a tree and the examples can continue. Iterator Pattern. Intent: Provide an object which traverses some aggregate structure, abstracting away assumptions about the implementation of that structure.

The simplest iterator has a "next element" method, which returns elements in some sequential order until there are no more. More sophisticated iterators might allow several directions and types of movement through a complex structure. Typically an iterator has three tasks that might or might not be implemented in separate methods: Testing whether elements are available Advancing to the next n.th position Accessing the value at the current position Bidirectional iterators might have additional methods for checking and advancing the reverse direction. The simplest iterator merges these three tasks in one method, returning nil, null or whatever the language at hand provides to detect the end.
Iterators.pdf. Iterator Pattern. This post will be about the Iterator pattern which is a behavioural pattern.
The Purpose The idea behind this pattern is to have an object which you can loop over without needing to know the internal representation of the data. While in Python nothing is private so you can find out the internals of the class, the iterator pattern gives you a standard interface. I think the best example of an iterator in Python is using a list. Cloud-computing platform paves the way for an internet of robots. New Computer Programming Language Imitates The Human Brain. It could be a computer, but I agree that it is not "certainly" a type of computer.

We don't know enough about the human mind to categorize it as a computer. Computer: Programmable machine that can store, retrieve, and process data. We may have awesome computer brains...but they are still computers. I think you are saying there is a huge difference between an analog computer and a digital one. Don't repeat yourself. Applying DRY[edit]
Grep. History[edit] Usage[edit] Grep searches files specified as arguments, or, if missing, the program's standard input.
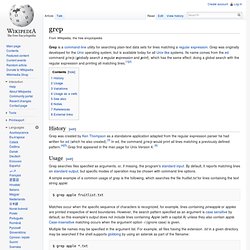
By default, it reports matching lines on standard output, but specific modes of operation may be chosen with command line options. A simple example of a common usage of grep is the following, which searches the file fruitlist.txt for lines containing the text string apple: $ grep apple fruitlist.txt Matches occur when the specific sequence of characters is recognized, for example, lines containing pineapple or apples are printed irrespective of word boundaries. . $ grep apple *.txt Regular expressions can be used to match more complicated text patterns.
. $ grep ^a.ple fruitlist.txt $ ed fruitlist.txt g/^a.ple/p q where the second line is the command given to ed to print the relevant lines, and the third line is the command to exit from the editor. Like most Unix commands, grep accepts options in the form of command-line arguments to change its behavior.
Variations[edit] The Story of Mel. A recent article devoted to the macho side of programming made the bald and unvarnished statement: Real Programmers write in FORTRAN.

Maybe they do now, in this decadent era of Lite beer, hand calculators, and “user-friendly” software but back in the Good Old Days, when the term “software” sounded funny and Real Computers were made out of drums and vacuum tubes, Real Programmers wrote in machine code. Not FORTRAN. Not RATFOR. Not, even, assembly language. Pastebin.com - #1 paste tool since 2002! Pastebin. History[edit] Pastebins developed in the late 1990s to facilitate IRC chatrooms devoted to computing,[citation needed] where users naturally needed to share large blocks of computer input or output in a line-oriented medium.
On such IRC channels, where the formatting clues are subtle and several conversations can be closely interleaved, blocks of computer data flood the queue, disrupting the intricate flow. Computer Programming. Programming paradigm. A programming paradigm is a fundamental style of computer programming, a way of building the structure and elements of computer programs. Capablities and styles of various programming languages are defined by their supported programming paradigms; some programming languages are designed to follow only one paradigm, while others support multiple paradigms.
There are six main programming paradigms: imperative, declarative, functional, object-oriented, logic and symbolic programming.[1][2][3] Overview[edit] Overview of the various programming paradigms[4]:5. The early years.pdf (application/pdf Object) They Cracked This 250-Year-Old Code, and Found a Secret Society Inside. For more than 200 years, this book concealed the arcane rituals of an ancient order. But cracking the code only deepened the mystery.Image courtesy: Uppsala University The master wears an amulet with a blue eye in the center.
10 Technical Papers Every Programmer Should Read (At Least Twice) 10 Technical Papers Every Programmer Should Read (At Least Twice) this is the second entry in a series on programmer enrichment Inspired by a fabulous post by Michael Feathers along a similar vein, I’ve composed this post as a sequel to the original. That is, while I agree almost wholly with Mr. R (programming language) R is a programming language and software environment for statistical computing and graphics. The R language is widely used among statisticians and data miners for developing statistical software[2][3] and data analysis.[3] Polls, surveys of data miners, and studies of scholarly literature databases show that R's popularity has increased substantially in recent years.[4][5][6][7] R is highly extensible through the use of user-submitted packages for specific functions or specific areas of study. Due to its S heritage, R has stronger object-oriented programming facilities than most statistical computing languages.
Array programming. Gray code. _13_11_1573_1597_doran.pdf (application/pdf Object) Puzzle-gray-code.pdf (application/pdf Object) Self-modifying code. Bitwise operation. Sparse coding. LGP - 30 PROGRAMMING MANUAL. Go to On Line Documents, Go to Go to Antique Computer home page. 67 Open Source Replacements for Really Expensive Applications. 30 free programming eBooks « citizen428.blog()
Since this post got quite popular I decided to incorporate some of the excellent suggestions posted in the comments, so this list now has more than 50 books in it. Extreme programming. Planning and feedback loops in extreme programming. Pair programming. The Art of Agile Development: Pair Programming. ACMarticlePairProgramming. Code smell. Spaghetti Code. International Obfuscated C Code Contest. Grammars and Parsers. Linear programming. Linux - Why do you need to put #!/bin/bash at the beginning of a script file. Sudo rm -rf / Sudo_report_incident.png (PNG Image, 695 × 309 pixels) Adding user to Sudoers file. Kernel panic. Comparison of privilege authorization features.
Privacy. Memory safety. Bounds checking. Intrusion detection system. Intrusion prevention system. Buffer overflow. Obfuscation (software) Penrose Tiling Explained. Penrose Tiling in Obfuscated Python. International Obfuscated C Code Contest. Stop CAS (Copyright Alert System) Google Declares War on the Password. Password Strength. Hackers & hacking. Hacker (computer security) White hat (computer security) Category:Hacking (computer security) L0pht. Grey hat. Social engineering (security) Rootkit. Kogito: Main. Older, quieter than WikiLeaks, Cryptome perseveres. HackerspaceWiki. Noisebridge. IRC. Payphone. Crowdsourced 'Maker Map' Charts Nearby Hackerspaces and Hardware Shops.
Quotes. The Quest for Root - Hacker Techniques and UNIX Security - 103808. Definition by The Linux Information Project. The 50 Best Registry Hacks that Make Windows Better - How-To Geek - StumbleUpon. Short Film of the Day: Stuxnet: Anatomy of a Computer Virus. Surveillance.
DARPA’s New Cyber Targeted-Attack Analyzer Program. A free database of the entire Web may spawn the next Google.