

Cluster: conceito e características. Introdução Quando o assunto é computação de alto desempenho, não é difícil pensarmos em servidores sofisticados e caros respondendo por este trabalho.
No entanto, é possível obter resultados tão bons quanto ou superiores a partir de alguma solução de cluster - uma tecnologia capaz de fazer computadores mais simples trabalharem em conjunto, como se formassem uma máquina só. Neste texto, você saberá o que é computação em cluster, verá quais são as principais características do conceito e conhecerá algumas de suas aplicações, assim como soluções do tipo. O que é cluster? Cluster (ou clustering) é, em poucas palavras, o nome dado a um sistema que relaciona dois ou mais computadores para que estes trabalhem de maneira conjunta no intuito de processar uma tarefa. Cada computador que faz parte do cluster recebe o nome de nó (ou node). Um antigo cluster montado com desktops - Imagem por Wikipedia Não é necessário haver um conjunto de hardware exatamente igual em cada nó. Tipos de clusters. What exactly is BIG-IP? : networking. What is initial program load (IPL)? - Definition from WhatIs.com.
IPL (initial program load) is a mainframe term for the loading of the operating system into the computer's main memory .
A mainframe operating system (such as OS/390) contains many megabytes of code that is customized by each installation, requiring some time to load the code into the memory. On a personal computer, booting or re-booting (re-starting) is the equivalent to IPLing (the term is also used as a verb) . In earlier operating systems, when you added devices to the hardware system, you had to stop the system, change the configuration file, and then "re-IPL," an activity that meant the system would be unavailable for some period of time. Today's systems provide dynamic reconfiguration so that the system can keep running.
The One Page Linux Manual. Desktop RAM. Computer Network Cables. WiFi & LiFi : A Comparison Study. Ethernet Cables - RJ45: colors & crossover. Computer and network protocols; TCP / IP - OSI. The Defense Advance Research Projects Agency (DARPA) originally developed Transmission Control Protocol / Internet Protocol (TCP / IP) as a mechanism for connecting different networks in the U.S.

Department of Defense (DoD) in a way that communication can 'survive' in any conditions. Internet, international, very widespread international network (WAN) using TCP / IP protocol into an environment of institutional and government institutions worldwide. This protocol suite is widely distributed in commercial and private networks. In the following picture in the list that follows lists all the protocols used by TCP / IP connected environment.
Lead time. A lead time is the latency (delay) between the initiation and execution of a process.
For example, the lead time between the placement of an order and delivery of a new car from a manufacturer may be anywhere from 2 weeks to 6 months. In industry, lead time reduction is an important part of lean manufacturing. Journalism[edit] Teleco.com.br. Understanding Key Differences Between FTP, FTPS and SFTP. Understanding Key Differences Between FTP, FTPS and SFTP Posted by Van Glass on Mon, Jan 02, 2012 @ 11:56 AM Perhaps the most common protocols used in file transfer today are FTP, FTPS and SFTP.
How to Use the Traceroute Command. Traceroute is a command which can show you the path a packet of information takes from your computer to one you specify.
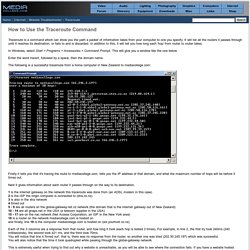
It will list all the routers it passes through until it reaches its destination, or fails to and is discarded. In addition to this, it will tell you how long each 'hop' from router to router takes. In Windows, select Start > Programs > Accessories > Command Prompt. New for Internet Explorer: HTTP/2 Support. As part of the Windows 10 Technical Preview, Internet Explorer will offer HTTP/2 support, performance improvements to the Chakra JavaScript engine, and a top-level domains parsing algorithm based on publicsuffix.org.
HTTP/2 is a new standard by the Internet Engineering Task Force. There are two components: Hypertext Transfer Protocol version 2 and HPACK - Header Compression for HTTP/2. HTTP/2 differs from the original HTTP standard in five key ways: is binary, instead of textual is fully multiplexed, instead of ordered and blocking can therefore use one connection for parallelism uses header compression to reduce overhead allows servers to “push” responses proactively into client caches. Secure copy. The term SCP can refer to one of two related things, the SCP protocol or the SCP program.
SCP protocol[edit] How it works[edit] Normally, a client initiates an SSH connection to the remote host, and requests an SCP process to be started on the remote server. The remote SCP process can operate in one of two modes: source mode, which reads files (usually from disk) and sends them back to the client, or sink mode, which accepts the files sent by the client and writes them (usually to disk) on the remote host. Transport Layer Security. Transport Layer Security (TLS) and its predecessor, Secure Sockets Layer (SSL), are cryptographic protocols designed to provide communications security over a computer network.[1] They use X.509 certificates and hence asymmetric cryptography to authenticate the counterparty with whom they are communicating,[2] and to exchange a symmetric key.
This session key is then used to encrypt data flowing between the parties. This allows for data/message confidentiality, and message authentication codes for message integrity and as a by-product, message authentication. [clarification needed] Several versions of the protocols are in widespread use in applications such as web browsing, electronic mail, Internet faxing, instant messaging, and voice-over-IP (VoIP). SSH. Telnet. Internet protocol suite. The Internet protocol suite is the computer networking model and set of communications protocols used on the Internet and similar computer networks.
It is commonly known as TCP/IP, because its most important protocols, the Transmission Control Protocol (TCP) and the Internet Protocol (IP), were the first networking protocols defined in this standard. Often also called the Internet model, it was originally also known as the DoD model, because the development of the networking model was funded by DARPA, an agency of the United States Department of Defense.
TCP/IP provides end-to-end connectivity specifying how data should be packetized, addressed, transmitted, routed and received at the destination. The TCP/IP model and related protocol models are maintained by the Internet Engineering Task Force (IETF). History[edit] Early research[edit]