

Baudot-Code - Telex CCITT-1 Norm kodieren und dekodieren. Codebreaking. Introduction Welcome to a world of secrecy, spies and subterfuge.

Ciphers and codes have been around since the Romans, and are one of the oldest forms of secret communication. Cryptography is the science of encoding and decoding secret messages. It is all around us in everyday life, when we send emails to our friends and colleagues, or when we buy something over the internet using a credit card. It is constantly evolving as cryptographers endeavour to break existing codes and create new unbreakable codes. Although we tend to use the words code and cipher interchangeabley, they actually have quite distinct meanings.
Our message, ‘The Prime Minister of England will be assassinated at midnight by a spy’ might be encoded as ‘The green cow will read the book at the supermarket’ On the other hand, in a cipher, the encryption is done at the level of the letter, making it far more difficult to crack, and therefore more secure. Steganography.
Affine Cipher Applet. Overview An affine cipher encrypts this way: C = (alpha * P + beta) mod 26 where: P = plaintext character (0 for A, 1 for B, ... 26 for Z) C = ciphertext character (alpha,beta) = the key, where alpha must be relatively prime to 26 Enter a sentence and an alpha and beta below and click ENCRYPT to encrypt that sentence with that key.

Enter a key and click DECRYPT to decrypt. Decryption will not do anything unless the alpha is relatively prime to 26 (i.e. is odd and is not 0 or 13). The SECRET button encrypts an english phrase with a random key. The FREQUENCY tab has tools to help discover that key and decrypt the phrase. Affine Map. Encrypt/Encode. Home > yis > tools > encrypter > Yellowpipe - Encrypter/Decrypter, Encode / decode: Base64, ASCII, Binary, Hex, DES, MD5, SHA1, Bruteforce, ROT-13, URL encode Encrypter /Decoder Encryption / Decryption tool » Online Encrypter / Decrypter tool This program let you encode/decode or encrypt/decrypt your documents in various formats such as: ASCSII, Binary, Base 64, Hex, Caesar Bruteforce, MD5, SHA-1, HTML Entities.
See below the complete list. Test it. X&Y Artwork Generator. Coldplay X&Y Album Art Generator. Geocache tools. Trifid Cipher. The Trifid Cipher is the Bifid Cipher taken to one more dimension.
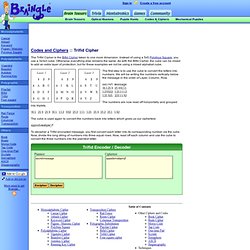
Instead of using a 5x5 Polybius Square, you use a 3x3x3 cube. Otherwise everything else remains the same. As with the Bifid Cipher, the cube can be mixed to add an extra layer of protection, but for these examples we not be using a mixed alphabet cube. Universal online Cyrillic decoder - recover your texts. Decrypting text. Ciphers / Scytale / test it. Polyalphabetic Substitution Ciphers. Introduction The monoalphabetic (simple) substitution cipher uses only one replacement scheme for all letters of the plain text.

Polyalphabetic ciphers use more than one replacement scheme. RuffNekk's Crypto Pages - Beaufort Variant Tool. Keyed Caesar. One variation to the standard Caesar cipher is when the alphabet is "keyed" by using a word.
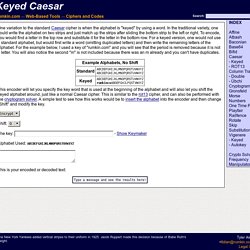
In the traditional variety, one could write the alphabet on two strips and just match up the strips after sliding the bottom strip to the left or right. To encode, you would find a letter in the top row and substitute it for the letter in the bottom row. For a keyed version, one would not use a standard alphabet, but would first write a word (omitting duplicated letters) and then write the remaining letters of the alphabet. For the example below, I used a key of "rumkin.com" and you will see that the period is removed because it is not a letter. You will also notice the second "m" is not included because there was an m already and you can't have duplicates.
ROT-X : Encryption/Decryption. Gronsfeld Cipher. Steganography_Decode - Utility Mill - Utility. Playfair Cipher. The Playfair cipher encrypts pairs of letters (digraphs), instead of single letters.
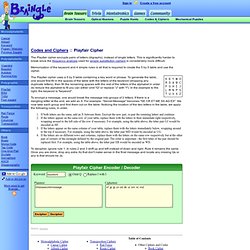
This is significantly harder to break since the frequency analysis used for simple substitution ciphers is considerably more difficult. Decrypto 8.5, Online Cryptoquip and Cryptogram Solver. Baudot-Code - Telex CCITT-1 Norm kodieren und dekodieren. Cipher Tools. Kodemaskinen. ROT47. Sharky's Vigenere Cipher. This page is for amusement only.
Instructions are given below this form. instructions: Enter the string to encrypt or decrypt in the Input field (you may copy and paste it from another text editor). Enter the key in the Key field. (You may use any sequence of characters, but only alphabetic characters will actually be processed. On most computers: To copy: Highlight text, press Ctrl-C; To paste: Position cursor, press Ctrl-V. explanation: Vigenere coding is one of the most ancient forms of cryptography. Choose a key that is as long as the plaintext message.
Unfortunately, these steps take all the fun out of the Vigenere cipher. Vigenere ciphers with moderate keys are appropriate for situations that do not require failproof security. We hope you enjoy this simple JavaScript-based implementation.