

Chapter 12 : SQL Injection (Site Hacking) ~ HACK WITH STYLE. #OpNewBlood. Ethos, Pathos, and Logos. A General Summary of Aristotle's Appeals . . .

The goal of argumentative writing is to persuade your audience that your ideas are valid, or more valid than someone else's. The Greek philosopher Aristotle divided the means of persuasion, appeals, into three categories--Ethos, Pathos, Logos. Ethos (Credibility), or ethical appeal, means convincing by the character of the author. We tend to believe people whom we respect. One of the central problems of argumentation is to project an impression to the reader that you are someone worth listening to, in other words making yourself as author into an authority on the subject of the paper, as well as someone who is likable and worthy of respect.
Pathos (Emotional) means persuading by appealing to the reader's emotions. Logos (Logical) means persuading by the use of reasoning. Ethos, Pathos, and Logos. Ethos (Greek for 'character') refers to the trustworthiness or credibility of the writer or speaker. Or The Shorthand Version: Pathos Logos Ethos. Out-of-date browser plug-ins are attractive targets for cybercriminals. For example, Adobe Reader is installed in 83% of enterprise browsers, and 56% of those installations are out of date, according to the report, which is based on a review of enterprise web traffic flowing through Zscaler’s cloud-based web and email security product.
“That is a huge attack surface….This is really what the attackers are going after”, commented Michael Sutton, vice president of research at Zscaler ThreatLabZ. The Blackhole exploit kit has picked up on this and includes a variety of payloads designed to target recent Adobe Reader vulnerabilities, the report noted. The State of the Web report also found that Apple iOS has taken the lead in the workplace, with 42.4% of the mobile device usage on corporate networks, followed by Blackberry with 40.2% and Android with 17.4%.
Sutton, who is an author of the report, told Infosecurity that he believes that iOS is a more secure platform than Android. Fake Name Generator. The Hacker Manifesto. By +++The Mentor+++ Written January 8, 1986 Another one got caught today, it's all over the papers.

"Teenager Arrested in Computer Crime Scandal", "Hacker Arrested after Bank Tampering"... Damn kids. They're all alike. But did you, in your three-piece psychology and 1950's technobrain, ever take a look behind the eyes of the hacker? I am a hacker, enter my world... Mine is a world that begins with school... Damn underachiever. I'm in junior high or high school. Damn kid. I made a discovery today. Damn kid. And then it happened... a door opened to a world... rushing through the phone line like heroin through an addict's veins, an electronic pulse is sent out, a refuge from the day-to-day incompetencies is sought... a board is found. Damn kid. You bet your ass we're all alike... we've been spoon-fed baby food at school when we hungered for steak... the bits of meat that you did let slip through were pre-chewed and tasteless.
Yes, I am a criminal. The OpNewblood Super Secret Security Handbook « welcome to serpent's embrace. The #OpNewblood Super Secret Security Handbook If you have not gone through the IRC chat client setup for your operating system, we recommend you go back and get started there.
Master Table of Contents 1) Preface 2) Setting up Tor 3) Firefox Recommended Add-Ons 4) Setting up i2p 4.1) Installation 4.2) Firefox Configuration 4.3) IRC Client Configuration 4.4) I2p IRC on Android via irssi connectbot 5) Advanced IRC 5.1) Commands 5.2) Browsing 6) Advanced Defense Techniques 7) Portable Solutions 8 ) ADVANCED GUIDE TO HACKING AND SECURITY VULNERABILITY. Anonymous: From the Lulz to Collective Action. Taken as a whole, Anonymous resists straightforward definition as it is a name currently called into being to coordinate a range of disconnected actions, from trolling to political protests.
Originally a name used to coordinate Internet pranks, in the winter of 2008 some wings of Anonymous also became political, focusing on protesting the abuses of the Church of Scientology. By September 2010 another distinct political arm emerged as Operation Payback and did so to protest the Motion Picture Association of America (MPAA), and a few months later this arm shifted its energies to Wikileaks, as did much of the world's attention. It was this manifestation of Anonymous that garnered substantial media coverage due the spectacular waves of distributed denial of service (DDoS) attacks they launched (against PayPal and Mastercard in support of Wikileaks). ARP spoofing. A successful ARP spoofing (poisoning) attack allows an attacker to alter routing on a network, effectively allowing for a man-in-the-middle attack.
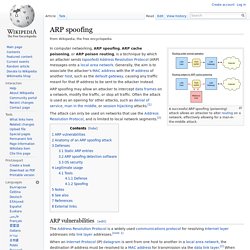
ARP spoofing may allow an attacker to intercept data frames on a network, modify the traffic, or stop all traffic. Often the attack is used as an opening for other attacks, such as denial of service, man in the middle, or session hijacking attacks.[1] The attack can only be used on networks that use the Address Resolution Protocol, and is limited to local network segments.[2] ARP vulnerabilities[edit] The Address Resolution Protocol is a widely used communications protocol for resolving Internet layer addresses into link layer addresses. Anonymous. /b/ - Boxxy.
Penetration Testing Framework 0.58a. How Secure Is My Password?