

Identity at Mozilla. We were very happy to see the revamped “Log In with Google Plus” product from our friends across town: big improvements in user experience, great mobile integration, and clearer privacy controls.
Still, we think Identity on the Web can be better: easier for developers, true choice and control for users. Personal Is A Secure Vault For All Of Your Private, Digital Data. We wrote about stealthy startup Personal earlier this year when the company announced $7.6 million in funding from Steve Case’s Revolution LLC, Allen&Company, and others.
This week, Personal finally launched its service, which aims to give consumers control over their digital data, to the public. Personal is a free web and mobile service that helps you take control of all the digital information about yourself and your life, decide who gets access to it, and use it for your benefit. 6d, an online identity building web app. Own your online identity. Own your content. Palmetto API. XACML. XACML stands for eXtensible Access Control Markup Language.
The standard defines a declarative access control policy language implemented in XML and a processing model describing how to evaluate access requests according to the rules defined in policies. As a published standard specification, one of the goals of XACML is to promote common terminology and interoperability between access control implementations by multiple vendors.
XACML is primarily an Attribute Based Access Control system (ABAC), where attributes (bits of data) associated with a user or action or resource are inputs into the decision of whether a given user may access a given resource in a particular way. Role-based access control (RBAC) can also be implemented in XACML as a specialization of ABAC. The XACML model supports and encourages the separation of the access decision from the point of use. History[edit] The first committee specification of XACML 3.0 was released August 10, 2010.[1] Terminology[edit] Targets[edit] Google revises Google+ real name management policy. Google Confirms: Non-Real Name Google Profiles Risk Suspension (I.E., Google Still Doesn’t Get Social) UPDATE, 7/12, 2:45PM: The story continues in this post here.
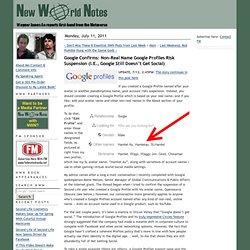
If you created a Google Profile named after your avatar or another pseudonymous name, your account risks suspension. Instead, you should consider creating a Google Profile which is based on your real name, and if you like, add your avatar name and other non-real names in the About section of your profile. To do that, click “Edit Profile” and enter those names in the designated fields, as pictured at right from my own profile, which has my SL avatar name, “Hamlet Au”, along with variations of account names I use in other gaming/virtual world/social media settings. My advice comes after a long e-mail conversation I recently completed with Google spokesperson Katie Watson, Senior Manager of Global Communications & Public Affairs at the Internet giant. Public-key cryptography. An unpredictable (typically large and random) number is used to begin generation of an acceptable pair of keys suitable for use by an asymmetric key algorithm.
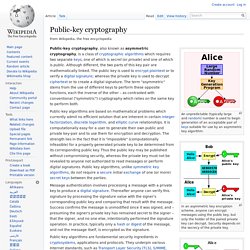
In an asymmetric key encryption scheme, anyone can encrypt messages using the public key, but only the holder of the paired private key can decrypt. Security depends on the secrecy of the private key. In the Diffie–Hellman key exchange scheme, each party generates a public/private key pair and distributes the public key. As of July 31st, all Google profiles will be public. Google will no longer allow users to have private Google profiles after July 31st, reports Search Engine Land.
The company had previously allowed users to create and maintain profiles on its service without publicly disclosing their existence. Google is making the change primarily to aid in the growth of its new Google+ social network. What is SSL and what are Certificates? Get Janrain Engage.
Privacy. Authentication. Facebook’s Facial Recognition Fiasco: Those Words Sound Scary! Angst!
Raised Eyebrows! Distinct feelings of discomfort! So go the reactions to a feature on Facebook that uses facial recognition technology to help users tag their photos. It has people so upset, in fact, that it’s just sparked a probe from European Union privacy regulators. The uproar revolves around a feature that’s been around since December, so the technology itself isn’t particularly new. Except this time, the complaints seem to be about issues that aren’t new — and humans are still very much involved in deciding who gets tagged. Postini. Internet security — Authentic8. Foundry Group Invests In Postini Founder’s New Browser Security Startup, Authentic8. The Foundry Group’s Ryan McIntyre (who was a board member of Postini) just announced the venture firm’s investment in browser security startup Authentic8, which is the brainchild of Postini founder Scott Petry and Ramesh Rajagopal (Postini’s VP Corporate Development).
Postini offered businesses message security, archiving, encryption, and policy enforcement tools which can be used to protect a company’s email, instant messaging, and other web-based communications platforms. The company was eventually acquired by Google in 2007 for $625 million. As McIntyre writes, Authentic8 is “a direct descendant of the Postini DNA.” While Positini tackled email security, Authentic8 addresses security in the browser. The startup has created a secure browser called the Disposable Browser (currently based on the Firefox codebase), which runs remotely on a virtual server in the cloud. The goal of Authentic8 is to appeal to businesses who are conscious of employees’ security through browsers.