

56A, Recommendation for Pair-Wise Key Establishment Schemes Using Discrete Logarithm Cryptography (Revised) - SP800-56A_Revision1_Mar08-2007.pdf. Symmetric-key algorithm. Block cipher. In cryptography, a block cipher is a deterministic algorithm operating on fixed-length groups of bits, called blocks, with an unvarying transformation that is specified by a symmetric key.
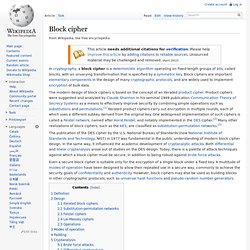
Block ciphers are important elementary components in the design of many cryptographic protocols, and are widely used to implement encryption of bulk data. The modern design of block ciphers is based on the concept of an iterated product cipher. Product ciphers were suggested and analyzed by Claude Shannon in his seminal 1949 publication Communication Theory of Secrecy Systems as a means to effectively improve security by combining simple operations such as substitutions and permutations.[1] Iterated product ciphers carry out encryption in multiple rounds, each of which uses a different subkey derived from the original key.
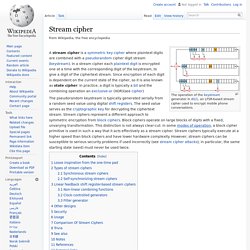
Stream cipher. The operation of the keystream generator in A5/1, an LFSR-based stream cipher used to encrypt mobile phone conversations.
Data Encryption Standard. DES is now considered to be insecure for many applications.
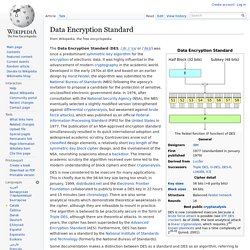
This is chiefly due to the 56-bit key size being too small; in January, 1999, distributed.net and the Electronic Frontier Foundation collaborated to publicly break a DES key in 22 hours and 15 minutes (see chronology). There are also some analytical results which demonstrate theoretical weaknesses in the cipher, although they are infeasible to mount in practice. Advanced Encryption Standard. The Advanced Encryption Standard (AES), also referenced as Rijndael[4][5] (its original name), is a specification for the encryption of electronic data established by the U.S.
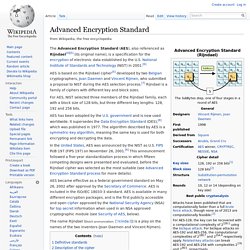
National Institute of Standards and Technology (NIST) in 2001.[6] AES is based on the Rijndael cipher[5] developed by two Belgian cryptographers, Joan Daemen and Vincent Rijmen, who submitted a proposal to NIST during the AES selection process.[7] Rijndael is a family of ciphers with different key and block sizes. For AES, NIST selected three members of the Rijndael family, each with a block size of 128 bits, but three different key lengths: 128, 192 and 256 bits. AES has been adopted by the U.S. government and is now used worldwide. It supersedes the Data Encryption Standard (DES),[8] which was published in 1977. In the United States, AES was announced by the NIST as U.S. AES became effective as a federal government standard on May 26, 2002 after approval by the Secretary of Commerce. §Definitive standards[edit] . Public-key cryptography. Elliptic curve cryptography. Elliptic curve cryptography (ECC) is an approach to public-key cryptography based on the algebraic structure of elliptic curves over finite fields.
Elliptic curves are also used in several integer factorization algorithms that have applications in cryptography, such as Lenstra elliptic curve factorization. The use of elliptic curves in cryptography was suggested independently by Neal Koblitz[1] and Victor S. Miller[2] in 1985. Elliptic curve cryptography algorithms entered wide use in 2004 to 2005. Introduction[edit] The primary benefit promised by ECC is a smaller key size, reducing storage and transmission requirements, i.e. that an elliptic curve group could provide the same level of security afforded by an RSA-based system with a large modulus and correspondingly larger key – e.g., a 256-bit ECC public key should provide comparable security to a 3072-bit RSA public key (see key sizes below).
The U.S. Cryptographic schemes[edit] MQV. MQV ( Menezes–Qu–Vanstone ) is an authenticated protocol for key agreement based on the Diffie–Hellman scheme.
Like other authenticated Diffie-Hellman schemes, MQV provides protection against an active attacker. The protocol can be modified to work in an arbitrary finite group , and, in particular, elliptic curve groups, where it is known as elliptic curve MQV (ECMQV) . MQV was initially proposed by Menezes , Qu and Vanstone in 1995. It was modified with Law and Solinas in 1998. There are one-, two- and three-pass variants. Elliptic Curve DSA. In cryptography, the Elliptic Curve Digital Signature Algorithm (ECDSA) offers a variant of the Digital Signature Algorithm (DSA) which uses elliptic curve cryptography.
Key and signature-size comparison to DSA[edit] As with elliptic curve cryptography in general, the bit size of the public key believed to be needed for ECDSA is about twice the size of the security level, in bits. For example, at a security level of 80 bits (meaning an attacker requires the equivalent of about operations to find the private key) the size of a DSA public key is at least 1024 bits, whereas the size of an ECDSA public key would be 160 bits. On the other hand, the signature size is the same for both DSA and ECDSA: bits, where is the security level measured in bits, that is, about 320 bits for a security level of 80 bits. Signature generation algorithm[edit] Suppose Alice wants to send a signed message to Bob. . Implicit certificate. In cryptography , implicit certificates are a variant of public key certificate , such that a public key can be reconstructed from any implicit certificate, and is said then to be implicitly verified, in the sense that the only party who can know the associated private key is the party identified in the implicit certificate.
This does not rule out the possibility that nobody knows the private key, but this possibility is not considered a major problem. By comparison, traditional public-key certificates include a copy of the public key and the digital signature of the certification authority. Integrated Encryption Scheme. Integrated Encryption Scheme (IES) is a hybrid encryption scheme which provides semantic security against an adversary who is allowed to use chosen-plaintext and chosen-ciphertext attacks.
The security of the scheme is based on the Diffie–Hellman problem . Two incarnations of the IES are standardized: Discrete Logarithm Integrated Encryption Scheme (DLIES) and Elliptic Curve Integrated Encryption Scheme (ECIES), which is also known as the Elliptic Curve Augmented Encryption Scheme or simply the Elliptic Curve Encryption Scheme.
These two incarnations are identical up to the change of an underlying group and so to be concrete we concentrate on the latter. To send an encrypted message to Bob using ECIES Alice needs the following information: To encrypt a message. Elliptic curve Diffie–Hellman. Elliptic curve Diffie–Hellman (ECDH) is an anonymous key agreement protocol that allows two parties, each having an elliptic curve public–private key pair, to establish a shared secret over an insecure channel.[1][2][3] This shared secret may be directly used as a key, or better yet, to derive another key which can then be used to encrypt subsequent communications using a symmetric key cipher.
It is a variant of the Diffie–Hellman protocol using elliptic curve cryptography. Key establishment protocol[edit] The following example will illustrate how a key establishment is made. Suppose Alice wants to establish a shared key with Bob, but the only channel available for them may be eavesdropped by a third party. Initially, the domain parameters (that is, Handbook of Applied Cryptography. Alfred J. Menezes, CRC Press ISBN: 0-8493-8523-7 October 1996, 816 pages Fifth Printing (August 2001) The Handbook was reprinted (5th printing) in August 2001. The publisher made all the various minor changes and updates we submitted.
You can identify the 5th printing of the book by looking for "5 6 7 8 9 0" at the bottom of the page that includes the ISBN number. You can order the handbook today from any one of these online bookstores: Amazon Books (amazon.com) (Price as of May 9, 2016: US $84.10). Amazon.ca (for Canadian orders) (Price as of May 9, 2016: Cdn $118.22). Cryptography I.