

Alleged LulzSec hacker of Sony Pictures faces trial date in December. The background from LulzSec's Twitter page.

Leaked IRC logs show the group's inner workings. Photograph: AP An alleged member of the clandestine hacking group LulzSec pleaded not guilty on Monday to charges of taking part in an extensive computer breach of the Sony Pictures Entertainment film studio's European systems. Cody Kretsinger, 23, entered not guilty pleas to one count each of conspiracy and unauthorized impairment of a protected computer during a brief hearing in U.S. District Court in Los Angeles. US Magistrate Judge Victor Kenton set a trial date of 13 December for Kretsinger, who spoke only in response to questions from the judge. Kenton also ordered that Kretsinger be represented by a court-appointed public defender. Kretsinger faces a maximum sentence of 15 years in prison if convicted. Anonymous Message to NATO. 'Cyber Challenge' encourages teen hackers to seek security jobs.
Kyle Natale, 16, a member of the Xpoliters, the Harford Technical… (Kim Hairston, Baltimore…) October 22, 2011|By Candus Thomson, The Baltimore Sun Like skilled cat burglars, teams of college-age hackers slithered past defenses to probe the soft underbelly of a sophisticated computer system.

Their mission: to steal secrets and leave an electronic calling card. As they tapped away on laptops and spoke in low voices, knots of educators, business leaders, parents and government officials hovered nearby, smiling and nodding with approval. In the eyes of the organizers of the Maryland Cyber Challenge and Conference, today's hacker could be tomorrow's cybersecurity hero. "We need a whole generation of people to help us build out the digital future," said Michael Kaiser, executive director of the National Cyber Security Alliance.
Recruiters from high-technology companies and defense contractors set up booths next to representatives from universities and the National Security Agency. The #AntiShock Dictionary. Confessions Of A Tunisian Hacktivist. Press Release – Who & What Anonymous represents! Donation Campaign Begins for #Freeanons. Anonymous v. Pedophiles. The Tor anonymity network is most commonly used by individuals who want to use the Internet with privacy, including political activists in nations without free speech protections.

The Global Cybergame Has Begun. United States Navy Military domain is vulnerable to hackers ~ THN : The Hacker News. United States Navy Military domain is vulnerable to hackers United States Navy Military website is full of vulnerabilities.

Sec Indi Security Team Hacker upload a custom message on the server as shown below : Url is hidden for Security Reasons. Hacker claim to inform the website admins already, but government did not fix it yet so he releasing this in public. Dan Ariely asks, Are we in control of our own decisions? We All Knew It Could Be Done : Exclusive: Computer Virus Hits U.S. Drone Fleet. A computer virus has infected the cockpits of America’s Predator and Reaper drones, logging pilots’ every keystroke as they remotely fly missions over Afghanistan and other warzones.
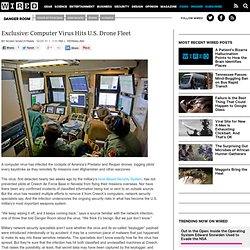
The virus, first detected nearly two weeks ago by the military’s Host-Based Security System, has not prevented pilots at Creech Air Force Base in Nevada from flying their missions overseas. Nor have there been any confirmed incidents of classified information being lost or sent to an outside source. But the virus has resisted multiple efforts to remove it from Creech’s computers, network security specialists say. And the infection underscores the ongoing security risks in what has become the U.S. military’s most important weapons system. Trustnetwork IIC Hosting Via @AnonymouSabu. Pastebin postings of Anonymous OpDarknet. Anonymous Action. Stuxnet: Digital Industrial Sabotage or Cyber-Weapon of Mass Destruction?
The story of Stuxnet reads like a cross between a work of cyberpunk fiction and an international spy novel. HideMyAss Anonymous VPN Shops Lulzsec Suspects. HideMyAss.com, the anonymous VPN service, has admitted that it handed over the details of one of the alleged Lulzsec hackers who attacked systems belonging to Sony Picture Entertainment.
The HideMyAss service is based in the UK and provides a free proxy that tell users they can “surf anonymously online, hide your IP address, secure your internet connection, hide your internet history, and protect your online identity.” Last week the alleged Lulzsec hacker known as ‘Recursion’, aka Cody Andrew Kretsinger, 23, of Phoenix, Arizona, was arrested by the FBI. Court Order HideMyAss explained that it had complied with a court order to disclose Kretsinger’s IP address that he had used to log into the HideMyAss service. 50 Days of Mayhem: How LulzSec Changed Hacktivism Forever. Anonymous Warns of 'Day of Vengeance' Saturday. DIY Wireless Device Hacks & 'Modifies' News, Take On MSM Directly: Anti-Propaganda - NewsTweek. Kilgore Trout Ousts Barret Brown as Leader of Anonymous.
Are the NYPD and FBI Trying to Frame Anonymous, Occupy Wall Street? Operation-Invade-Wall-Street. Jamie Jo Corne, head of Presstorm, speaks - National Anonymous. BlackBerg security hacked - National Anonymous. Are the NYPD and FBI Trying to Frame Anonymous, Occupy Wall Street? Antisec - Boston Police Patrolman's Association hacked and pranked. Tor anonymizing network Compromised by French researchers ~ THN : The Hacker News. Tor anonymizing network Compromised by French researchers French researchers from ESIEA, a French engineering school, have found and exploited some serious vulnerabilities in the TOR network.

They performed an inventory of the network, finding 6,000 machines, many of whose IPs are accessible publicly and directly with the system’s source code. They demonstrated that it is possible to take control of the network and read all the messages that circulate. But there are also hidden nodes, the Tor Bridges, which are provided by the system that in some cases. Researchers have developed a script that, once again, to identify them. The specific attack involves creating a virus and using it to infect such vulnerable systems in a laboratory environment, and thus decrypting traffic passing through them again via an unknown, unmentioned mechanism. To guide communication to nodes infected, researchers make unavailable all other nodes. How hackers get caught.