

Wargames - SmashTheStack.org. IO wargame - smashthestack.org. IO walkthrough - onHacks. IO Level 1 - onHacks. IO walkthrough Level 2 - onHacks. IO walkthrough Level 3 - onHacks. IO walkthrough Level 4 - onHacks. Smashing the Stack for Fun and Profit by Aleph One. Buffer Overflow. This is a Vulnerability.
To view all vulnerabilities, please see the Vulnerability Category page. This article includes content generously donated to OWASP by Last revision (mm/dd/yy): 02/20/2009 Vulnerabilities Table of Contents. Analysis of Buffer Overflow Attacks. What causes the buffer overflow condition?

Broadly speaking, buffer overflow occurs anytime the program writes more information into the buffer than the space it has allocated in the memory. This allows an attacker to overwrite data that controls the program execution path and hijack the control of the program to execute the attacker’s code instead the process code. For those who are curious to see how this works, we will now attempt to examine in more detail the mechanism of this attack and also to outline certain preventive measures.
From experience we know that many have heard about these attacks, but few really understand the mechanics of them. Others have a vague idea or none at all of what an overflow buffer attack is. Programs written in C language, where more focus is given to the programming efficiency and code length than to the security aspect, are most susceptible to this type of attack. Process Memory. Se mettre à GDB en 5 minutes.
Debugging with Gnu DeBugger. Memset() - Standard C String & Character - C Programming Referen. Execl() exécution d'un programme. Description. Next: execv() exécution d'un programme Up: execl() exécution d'un programme Previous: Interface Description Le programme en train de s'exécuter est remplacé par le programme dont le nom est pointé par path -- si le programme exécutable se trouve dans le repertoir courant, la variable path contiendra le nom du fichier simplement. arg0, arg1, 1#1, argn sont les paramètres qui seront passés au programme activé.

La convention sous UNIX font que arg0 représente le nom du programme. Si tout s'est bien passé, on ne revient pas de cette fonction. Si on revient de la fonction, c'est qu'une erreur a été détectée dont le code est dans la variable errno. Interface. Fibonacci number. A tiling with squares whose side lengths are successive Fibonacci numbers In mathematics, the Fibonacci numbers or Fibonacci sequence are the numbers in the following integer sequence: or (often, in modern usage): (sequence A000045 in OEIS).
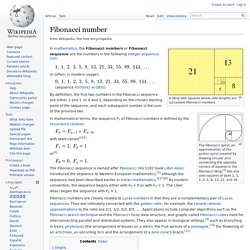
The Fibonacci spiral: an approximation of the golden spiral created by drawing circular arcs connecting the opposite corners of squares in the Fibonacci tiling;[3] this one uses squares of sizes 1, 1, 2, 3, 5, 8, 13, 21, and 34. By definition, the first two numbers in the Fibonacci sequence are either 1 and 1, or 0 and 1, depending on the chosen starting point of the sequence, and each subsequent number is the sum of the previous two. In mathematical terms, the sequence Fn of Fibonacci numbers is defined by the recurrence relation. Initiation à Bash. Sous linux vous entendrez souvent parler de terminal, en mode graphique sous kde par exemple, cela peut être assimilé à la petite tv noire à gauche de la barre des tâches.
Bash For Loop Examples. How do I use bash for loop to repeat certain task under Linux / UNIX operating system?

How do I set infinite loops using for statement? How do I use three-parameter for loop control expression? A ‘for loop’ is a bash programming language statement which allows code to be repeatedly executed. A for loop is classified as an iteration statement i.e. it is the repetition of a process within a bash script. Using strings - looking for strings in a binary. By Joe Barr on October 25, 2004 (8:00:00 AM)
Setuid. Setuid and setgid (short for "set user ID upon execution" and "set group ID upon execution", respectively)[1] are Unix access rights flags that allow users to run an executable with the permissions of the executable's owner or group respectively and to change behaviour in directories.
They are often used to allow users on a computer system to run programs with temporarily elevated privileges in order to perform a specific task. While the assumed user id or group id privileges provided are not always elevated, at a minimum they are specific. setuid on executables[edit] While the setuid feature is very useful in many cases, its improper use can pose a security risk[2] if the setuid attribute is assigned to executable programs that are not carefully designed. Due to potential security issues,[3] many operating systems ignore the setuid attribute when applied to executable shell scripts. Messages (and spam) from those who won. Logic.smashthestack.org. Logic - Les Tutos de Nico. Wargames - intruded.net. Wargames - OntheWire.org. We're hackers, and we are good-looking.
We are the 1%. The wargames offered by the OverTheWire community can help you to learn and practice security concepts in the form of fun-filled games. To find out more about a certain wargame, just visit its page linked from the menu on the left. If you have a problem, a question or a suggestion, you can join us on IRC. Suggested order to play the games in.
Wargames - HES2010. We're hackers, and we are good-looking.
We are the 1%. This wargame was introduced at the Hackito Ergo Sum (HES) 2010 conference in Paris and is centered around the fictitious company dirty-underwear.com The winners of this wargame at HES2010 were CCCP and morla. Computers that you can legally break into! [ www.try2hack.nl ] Welcome to HackersLab!!! HackersLab. Free Hacking Zone.