

How To Set Up vsftpd for a User's Directory on Ubuntu 16.04. Introduction FTP, short for File Transfer Protocol, is a network protocol that was once widely used for moving files between a client and server.
It has since been replaced by faster, more secure, and more convenient ways of delivering files. Many casual Internet users expect to download directly from their web browser with https, and command-line users are more likely to use secure protocols such as the scp or sFTP. FTP is still used to support legacy applications and workflows with very specific needs. If you have a choice of what protocol to use, consider exploring the more modern options. Linux System Logging - Seanskysite - Just another Blog for information about Technology Update. OpenStack Monitoring With the ELK Stack - DZone Cloud. OpenStack is an open source project that allows enterprises to implement private clouds.
Well-known companies such as PayPal and eBay have been using OpenStack to run production environments and mission-critical services for years. However, establishing and running a private cloud it not an easy task — it involves being able to control a large and complex system assembled from multiple modules. Issues occur more frequently in such IT environments, so operations teams should log and monitor system activities at all times. This will help them solve performance issues before they even occur. The Elasticsearch, Logstash, and Kibana (ELK) open source stack is one of the leading logging platforms due to its scalability, performance, and ease of use. Retrieving the Logs Most OpenStack services such as Nova, Cinder, and Swift write their logs to subdirectories of the /var/log directory. Everything you need to know about zombie process - Kernel Talks. Understand what is zombie process in Linux Unix, how process goes to zombie state, how to handle zombie process, what is impact of zombie processes.
In very lame terms, Zombie process is a process which is present in process table even if its already dead! Zombie process also known as defunct process. To understand how zombie process gets created let see how process exiting takes place from memory. How zombie gets created: Whenever process completes its execution, it exits and notify its parent process that his child has died. This whole operation completes very fast. W lina01. Killing Subprocesses in Linux/Bash. 25 Sep 2012 A common requirement when writing Bash scripts in Linux is to kill all a process and all of its child that were spawned.
This tutorial describes various methods to prevent orphaned subprocesses. Lately, I’ve been working with YARN at LinkedIn. This framework allows you to execute Bash scripts on one or more machines. It’s used primarily for Hadoop. Easily Find Bugs In Shell Scripts With ShellCheck. Unix Troubleshooting - Simple way. Quick Guide: How to write Bash function - UX Techno. In almost all programming language we make use of function which is nothing but the code written as logical block for executing repetitive or recurring execution.
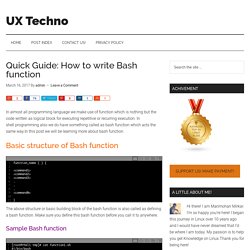
In shell programming also we do have something called as bash function which acts the same way.In this post we will be learning more about bash function. function_name ( ) { <command1><command2><command3> . . . <commandN> } How to Search for Files from the Linux Command Line. It goes without saying that every good Linux desktop environment offers the ability to search your file system for files and folders.
3 Ways to Extract and Copy Files from ISO Image in Linux. Let’s say you have a large ISO file on your Linux server and you wanted to access, extract or copy one single file from it.
How do you do it? Well in Linux there are couple ways do it. For example, you can use standard mount command to mount an ISO image in read-only mode using the loop device and then copy the files to another directory. Click For Information: 10 funny and useful things you can do in Ubuntu command line. Ah, the command line!
Refuge of a scoundrel, a proving ground for the expert, the tool selected advanced user. The following 10 tips explain how to do cool and interesting things on the command line. They are not specific to Ubuntu, but were written with the expectation of it, and not tested on other distributions. However, all should work in most versions of Linux, and even Unix. Use the mouse in the virtual console It's a neat hack, which has given a rectangular cursor, so that the text can be easily copied and pasted into a virtual console.
Then switch to a virtual console to see the fruits of their labor. Some software that offers a text-based menu, such as responding to a mouse click (for example, text the Lynx web browser, see below). YUM automatic updates! Save your valuable time! - Kernel Talks. Learn how to schedule YUM automatic updates to upgrade all system packages to available latest version in background without manual intervention!

Recently we published post about how to update packages in RHEL system using YUM. In this post we have explained how to update single or multiple packages and even all packages at once using command line. But these ways are manual tasks and needs human intervention to complete them. Click For Information: 50 of the most frequently used commands in the UNIX / Linux with examples. Of course, you should not take this article as a detailed guide, but it will definitely give you a starting point when working with Linux.
I advise you to put yourself in the browser bookmark list. If I missed something, let me know in the comments. Examples of the tar command. Click For Information: 15 great examples to create a cron job on Linux. Linux Format Crontab Table: Fields and allowable ranges Crontab (Linux Crontab syntax) 1. An Introduction to Vim for Sysadmins. Why, you ask, should anyone care about Vim? It's complex, it's so old it's a fossil, and you like Kate/Leafpad/Geany/Gedit/Nano/Jed/Lime/Emacs/what-have-you, and the Linux world is cram-full of great text editors, so why bother with Vim? The main reason it is included in nearly all Linux distributions. Sure, it is rather a desert island scenario to worry about being trapped on an unfamiliar system and you only have Vim to rescue yourself.
It does happen. You will especially appreciate it when you have to work over a slow SSH session with high latency because Vim is chock-a-block with powerful single-key commands. The other reason is it is a customizable powerhouse that rewards a bit of study and tweaking with a nice productivity boost. Distro Quirks. Publication workstation security github LF publication 020317 v10. ACTIVE RECONNAISSANCE:USING NMAP FOR INFORMATION GATHERING!!! Hello this is virtual.It was a long time since I posted last.During this time I was learning new things among which I am gonna tell you one today. The word reconnaissance is borrowed from its military use, where it refers to a mission into enemy territory to obtain information.In computer reconnaissance generally means the act of knowledge gathering by hackers.It involves the act of scanning a machine for open ports and services associated with them.
Nmap is the most popular tool used by hackers for reconnaissance.It comes inbuilt in Kali linux and Parrot Security OS but if you are using any othe OS like ubuntu install it by sudo apt-get install nmap To check if nmap has been installed type ' nmap ' and press Enter. GnuPG - Encrypt/Decrypt Files in Linux Command. We all have some secrets which we can’t share with anyone. In the similar kind of way, we all have some personal documents which we don’t want to show to anyone. How can protect those from others when multiple users accessing the same system. How to upload and download cloud images in OpenStack. One of the common tasks of cloud administrator is to manage cloud images i.e uploading and downloading cloud images. In OpenStack cloud images are controlled and managed by image service known as glance.
In most of the setup glance service is placed on the controller node and cloud images are stored at the location “/var/lib/glance/images“. Top 7 Tools that can automate Linux Admin Task. In this article, let’s take a look at the some of the tools that can make life easier for the Linux admins by automating his day to day tasks 1. The Linux top command understanding.
The top program provides a dynamic real-time view of a running system. It can display system summary information as well as a list of processes or threads currently being managed by the Linux kernel. 10 Linux GUI tools for sysadmins. Become a Linux Terminal Power User With These 8 Tricks. Do You Need These 9 Tools To Monitor Linux Disk Partitions And Usage In Linux? 1. fdisk. The Most Used Linux Terminal Commands and What They Do. Two things are true of the Linux command line: one, there are thousands of possible commands you can use at any given time, and two, you’ll only end up using a fraction of them. Despite the power offered, most of us just repeat the same commands over and over again. And that’s one of the biggest myths about Linux. How to limit SSH (TCP port 22) connections with ufw on Ubuntu Linux. ByVivek GiteonJanuary 24, 2017 last updated January 24, 2017 How do I limit ssh connection attempts using UFW (Uncomplicated Firewall) on Ubuntu or Debian Linux server?
UFW means Uncomplicated Firewall. Why and how to disable SELinux in your Linux distro - Kernel Talks. How To Limit CPU Usage Of A Process In Linux. Finding Interesting Documents with grep. The grep command is a very powerful way to find documents on your computer. How to check If a Machine is Physical or Virtual in Linux ? Find Out All Live Hosts IP Addresses Connected on Network in Linux. Ping almayan server kapalı mı açıkmı bulalım. Download Managers/Accelerators for Linux. Linux tar Command Examples & Usage. Tecmint: Linux Howtos, Tutorials & Guides. Monitor system resources on Linux through nmon. Check hardware information on Linux through inxi. 80 Linux Monitoring Tools for SysAdmins. 3 open source command-line web browsers. 10 open source tools for your sysadmin toolbox. How to Install Elastic Stack on CentOS 7. The source for Linux information.