

International Journal of Cyber-Security and Digital Forensics (IJCSDF) Cyber Security and Information Systems Information Analysis Center. CyberCIEGE Educational Video Game. An innovative video game and tool to teach computer and network security concepts CyberCIEGE enhances information assurance and cyber security education and training through the use of computer gaming techniques such as those employed in SimCity™.

In the CyberCIEGE virtual world, users spend virtual money to operate and defend their networks, and can watch the consequences of their choices, while under attack. Cyber Security Simulation In its interactive environment, CyberCIEGE covers significant aspects of computer and network security and defense. Players of this video game purchase and configure workstations, servers, operating systems, applications, and network devices. They make trade offs as they struggle to maintain a balance between budget, productivity, and security. CyberCIEGE includes configurable firewalls, VPNs, link encryptors and access control mechanisms. HTG Explains: The Difference Between WEP, WPA, and WPA2 Wireless Encryption (and Why It Matters)
Expect Success With CompTIA Security+ Professor Messer Security+ Course Overview - CompTIA Security+ SY0-301: 0.0.
Malware. Five portable security apps you should carry on your USB drive. Could hijackers hold your electronic medical records for ransom? Erica Cohen Posted: Wednesday, September 26, 2012, 5:07 PM by Erica Cohen With data breach issues plaguing even the largest of companies, individuals are understandably concerned that their personal information could be leaked to unauthorized users.
Release of personal health information is especially concerning because of the information’s private nature. However, your medical records also face another kind of risk. Equation Group: Meet the NSA 'gods of cyber espionage' Carberp Family Malware Targeting the Banking Sector -HackSurfer. A challenge incident responders and fraud analysts for firms in the banking and financial services sector (BFSS) will soon be faced with is an increased incidence of customer take-over fraud from a very advanced malware family that was recently released into the wild (Cohen, 2013, July 9).
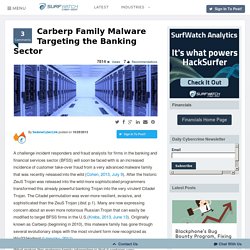
After the historic ZeuS Trojan was released into the wild more sophisticated programmers transformed this already powerful banking Trojan into the very virulent Citadel Trojan. The Citadel permutation was even more resilient, evasive, and sophisticated than the ZeuS Trojan (ibid. p.1). Many are now expressing concern about an even more notorious Russian Trojan that can easily be modified to target BFSS firms in the U.S. (Krebs, 2013, June 13). Originally known as Carberp (beginning in 2010), this malware family has gone through several evolutionary steps with the most virulent form now recognized as Win32/Hodprot (Lipovsky, 2011). Figure 1 – Account Take-Over Fraud Works by Infecting Customer Devices. Available Home Security Sensors and Home Automation Products - 24/7 Home Security.
Wondering which home security systems offer what features and accessories?
Which have enough features to make them home automation systems? Kismet. Wireshark · Go Deep. GlassWire Network Security Monitor & Firewall Tool. How To Turn On 2-Factor Authentication In Gmail. You Aren't Using These 10 Simple Security Settings. Online security isn't just a good idea anymore — it's an essential safety measure for anyone using the web.
In 2012, Wired senior tech reporter Mat Honan lost more than a year's worth of pictures of his newborn daughter after his Google and Amazon accounts were hacked. Earlier in 2013, the Syrian Electronic Army allegedly hacked the Twitter accounts of The Financial Times, E! Online and The Associated Press. In response to such attacks, Internet companies are increasingly moving toward two-step verification policies. This feature, also known as "two-factor authentication," requires a user to enter a security code in addition to her password when logging in from an unrecognized device. The tips below explain how to set up two-step verification on your most-used online applications. Facebook 1. Enabling Login Approval will affect apps that require your Facebook login, like Skype, Xbox or Spotify. Twitter. Everything You Wanted To Know About TOR And The Deep Web. Internet of Things, Cloud and Espionage of Safety.
Internet of Things (IoT) is a concern not only for the security, all cloud based service providers and to the software defined approaches.
Since 2010, we are mostly around the topics of core Networking and Virtualization. Gradually, we introduced Cloud Computing as a category. So, far we have the highest number of helpful information providing articles, guides on Cloud Computing as a single website. Gradually, we are heading to a future where everything will be software defined. Internet of Things (IoT), unfortunately is a biggest upcoming security threat. Infographic: Is free Wi-Fi a friend or foe?
You're Being Watched Online. October is National Cybersecurity Awareness Month - OpenDNS Blog. Wireless Network Security. Infographics : Enterprise Information Security Teams. A Short History of Hacking. If you thought hacking was a recent phenomenon think again.
As this infographic reveals, a form of phone hacking was in used 40 years ago. You may be surprised to see Rusell Crowe featured on an inforgraphic about hacking but the link is the film, The Beautiful Mind in which he played John Nash, the mathematician who coined the term "hacker". How to Delete Something Permanently From Your Computer. Do you have a file on your computer that you want to obliterate?
Well, it's going to take a lot more than dragging and dropping it into the little trash can at the corner of your desktop. Your computer's trash bin only removes a file from your desktop. And even if you empty the trash bin, it only deletes the virtual pathway to it. The file is still saved in your hard drive, but now it's just more difficult to access. Mobile Security Infestation. Infographic: Are We Being Safe Online? Four Wireless Hack Secrets Revealed. Untitled. Cloud Security Solutions for Tablets and Smartphones covers the issues with lost or stolen mobile devices, accidental data deletion, App security and Malwares.
These are the practical part of owning and using a mobile device, from Apple to Samsung, no manufacturers actually points out these parts. Cloud Security Solutions for Tablets and Smartphones from most of the manufacturers are kind of offering anti malware applications. How Virtual Private Networks Work. Untitled. Many IT workers feel more like firemen than like networking professionals.
They detect network attacks, respond to them and move on to the next problem. However, putting out fires is an ineffective approach because research has shown that most cyber attacks are not one-time events. They are a series of ongoing attacks designed to probe a network’s weakness and compromise it. While knowing that one’s network is constantly under attack may seem discouraging, the good news is that, the ongoing nature of attacks gives a chance to learn from the mistakes of the attackers.
Tips for Protecting Yourself from Hackers. How to Create a Strong Password and Why You Should Do This Now [Infographic]