

A-star Shortest Path Algorithm & C++ recipes & ActiveState Code. Top 10 Ways to be Screwed by "C" To get on this list, a bug has to be able to cause at least half a day of futile head scratching, and has to be aggravated by the poor design of the "C" language.

In the interests of equal time, and to see how the world has progressed in the 20-odd years since "C" escaped from its spawning ground, see my Top 10 Ways to be Screwed by the Java programming language, and for more general ways to waste a lot of time due to bad software, try my Adventures in Hell page. A better language would allow fallible programmers to be more productive. Infallible programmers, of the type unix' and "C" designers anticipated, need read no further. In fairness, I have to admit that the writers of compilers have improved on the situation in recent years, by detecting and warning about potentially bad code in many cases.
Blog. Computer graphics. Pranav Mistry: The thrilling potential of SixthSense technology. BioMotionLab. Security. Conway's Game of Life. "Conway game" redirects here.
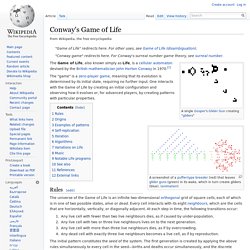
For Conway's surreal number game theory, see surreal number. The Game of Life, also known simply as Life, is a cellular automaton devised by the British mathematician John Horton Conway in 1970.[1] The "game" is a zero-player game, meaning that its evolution is determined by its initial state, requiring no further input. One interacts with the Game of Life by creating an initial configuration and observing how it evolves or, for advanced players, by creating patterns with particular properties. Rules[edit] Syrie : Ultrasurf, ou comment le gouvernement Syrien piège ses opposants avec un malware. Après l’Égypte ce matin, notre équipe s’est attaquée à la problématique syrienne.
Nous avons cherché à comprendre comment le pouvoir de Bachar el Assad s’y prenait pour voler les comptes Facebook, Twitter, ou Gmail de ses opposants, et comment il parvient à les identifier pour les arrêter. Nous avons réussi à mettre en lumière l’un des procédés du gouvernement Syrien afin de piéger ses opposants. C’est l’histoire banale d’un logiciel qui fait le contraire de ce qu’il prétend faire. Ultrasurf est un logiciel proxy qui a été très utilisé par les dissidents syriens. Le fonctionnement attendu, à savoir une dissimulation de l’identité de ses utilisateurs semblait opérante. Mais voilà, la version qui a été largement diffusée en Syrie contenait un petit paquet cadeau. Vous trouverez également le dump pcap de l’activité réseau de ce logiciel ici (à ouvrir avec Wireshark).
Building Cross-Platform Apps Using jQuery Mobile. jQuery Mobile introduces a cross-platform and cross-device framework for developing mobile applications. It supports a wide variety of mobile browsers and delivers a unified user interface to the devices. It has simplified working with mobile browsers by abstracting away inconsistences between the vendors. Just as jQuery changed the way we wrote JavaScript , jQuery Mobile will change the way we build mobile web applications. I recently used jQuery Mobile to build an application and was stunned at how smoothly the development process went. Java Tutorial 7 - String Manipulation. String manipulation forms the basis of many algorithms and utilities such as text analysis, input validation, and file conversion.

This tutorial explores some of the needed basics. Unless otherwise noted, the following classes are contained in the java.lang library. NOTE: For the following parameters the prefix g indicates string, i indicates integer and c indicates character types. The String Class. Mohawke's Best of the Best Free and Open Source Software Collection: Mac OS X and Windows software Collection. CoRR - Computing Research Repository. Welcome to the Computing Research Repository Welcome to the Computing Research Repository (CoRR).
CoRR allows researchers to search, browse and download papers through its online repository. CoRR is available to all members of of the community at no charge. Please feel free to explore the site and features. Programmer Competency Matrix. Fmeyer's gist: 289467. Jeff Han demos his breakthrough touchscreen.
Geek. Hack. FACEBOOK. À ranger. H4CKTiViSM. Start your own online School. How to recognise a good programmer. It’s not as easy as it sounds.

CV experience is only of limited use here, because great programmers don’t always have the “official” experience to demonstrate that they’re great. In fact, a lot of that CV experience can be misleading. Yet there are a number of subtle cues that you can get, even from the CV, to figure out whether someone’s a great programmer. I consider myself to be a pretty good programmer. At the same time, I’ve spent a fair amount of time on the business side of the fence, filtering technical CVs for projects, interviewing people, etc. In his article The 18 mistakes that kill startups , Paul Graham makes the following point: 21 Laws of Computer Programming. Jun 17 As any experienced computer programmer knows, there are unwritten laws that govern software development.
However there are no penalties for breaking these laws; rather, there is often a reward. Following are 21 Laws of Computer Programming: Levitated Daily Source, the good source.
Pratiquer / résoudre / se perfectionner.