

I Can't Find My Phone. 3D Stereogram. [How-To] Root, Recovery, ROM without touching a computer - Android Forums. iPad Breakdown: What's Inside and What it Costs to Make. A look deep into the electronic guts of Apple's new iPad has revealed that the basic version of the device costs about $260 to manufacture, according to the research firm iSuppli.
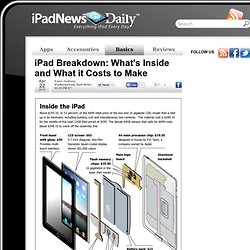
The company recently dissected the iPad in a so-called teardown analysis to find out just what makes Apple's much-heralded tablet computer tick. The teardown shows how the underlying structure of the iPad befits its purpose as a user-friendly, media-devouring device. Accordingly, and as expected, much of the cost of building an iPad appears related to ensuring it is easy on the eye and simple and fun for people to operate. (Read more iPad news.) The display, the multi-touch screen and other human-computer interface components make up nearly 44 percent of the total bill of materials for the basic 16 gigabyte (GB) memory, non-3G version of the iPad, according to iSuppli. What you see and feel Rounding out what one feels when holding an iPad is the aluminum backing that adds on $10.50. Power of the computer chips. Use Your USB Flash Drive As a Key to Lock Your PCs. Windows You might have seen in the movies; a USB drive is inserted into a computer and it immediately springs to life.
It is not difficult, you can use an application PREDATOR for exactly same thing. Predator locks your system when you are not there, even if your Windows session is still opened. It uses a regular USB flash drive as an access control device. Download and install Predator, and pair a USB drive with it. With the USB drive plugged in, you can continue to work, but as soon as it is removed, the screen darkens, the PC locks, and keyboard/mouse input is disabled. Security Features In Predator: Predator disables the CD Autorun feature in Windows. Install And Configure Predator: First download Predator from here. Now you are on Preference window, configure all settings and create a Key.
Click OK to save you settings. Now restart Predator to monitor your system. Hadouken!!! : gaming. Hacking Network Printers (Mostly HP JetDirects, but a little info on the Ricoh Savins) Hacking Network Printers(Mostly HP JetDirects, but a little info on the Ricoh Savins) By Adrian "Irongeek" Crenshaw Hack a printer you say, what kind of toner have you been smoking, Irongeek?
Well, I'm here to tell you, there's more that can be done with a printer to compromise network security than one might realize. In the olden days a printer may not have been much of a concern other than the threat from folks dumpster diving for hard copies of the documents that were printed from it, but many modern printers come network aware with embedded Operating Systems, storage and full IP stacks.
This article will attempt to point out some of the more interesting things that can be done with a network based printer to make it reveal information about its users, owners and the network it's part of. Some of this article may seem a little Black-hat as it concentrates more on the breaking-in than the keeping-out. The most recent version of this article can be found at: Table of Contents: Or Netcat: How to disable the keyboard Windows key. DeviantART muro. CJETR. My friend wants to start playing Bad Company 2 on PC. How cheap can we make a gaming rig to do so? : gaming.
Jsv35's Budget Builds (Updtd 6/19/10) Speedtest.net - The Global Broadband Speed Test. Your all-in-one tool site. KeyGenGuru.Com serial numbers, keygen, cracks, serial key generators -