

Redaction. RETE. American Scientist Online. 3store. Virtuoso. Memory. Virtuoso. Monetdb. Good-comments. Shell. Postgresql. Rdf3x. The Archive of Interesting Code. The Archive of Interesting Code is an (ambitious) effort on my part to research, intuit, and code up every interesting algorithm and data structure ever invented.
In doing so, I hope both to learn the mathematical techniques that power these technologies and to improve my skills as a programmer. In case you're curious what I'm someday hoping to having implemented on this page, you can check out my TODO list. If you're interested in using any of this code in your applications, feel free to do so! You don't need to cite me or this website as a source, though I would appreciate it if you did. However, please don't plagiarize the code here by claiming authorship - that would just be dishonest. Enjoy! Welcome to Domain Driven Data Mining.
Statistique. ArnetMiner - Academic Researcher Social Network Search. Forge: Bienvenue. Create a new Git Remote Repository from some local files (or local git repository) at A Waage Blog. So you have some files or a new Rails application, and you want to add this to a new shared remote Git repository.
(I’m assuming you have access to your server and are setting up a remote repo over ssh.) I know I can never remember how to do it, so here’s a post for me and hopefully you! Create a local Git repository in your application for your local files. #On local machine cd foo_project git init git add * git commit -m "My initial commit message" Now, create the repository on your Git server. #On remote machine (Git remote repository)sudo su - gitcd /usr/local/git_root/ Create your new project git repo as a bare Git repository mkdir foo-project.gitcd foo-project.git/git --bare init Make sure permissions are set properly. Git config core.sharedrepository 1git config receive.denyNonFastforwards truefind objects -type d -exec chmod 02770 {} \;#The core.sharedrepository flag tells git to keep everything group readable and writable. A Detailed Introduction to K-Nearest Neighbor (KNN) Algorithm. K Nearest Neighbor (KNN from now on) is one of those algorithms that are very simple to understand but works incredibly well in practice.
Also it is surprisingly versatile and its applications range from vision to proteins to computational geometry to graphs and so on . Most people learn the algorithm and do not use it much which is a pity as a clever use of KNN can make things very simple. It also might surprise many to know that KNN is one of the top 10 data mining algorithms. Lets see why this is the case ! In this post, I will talk about KNN and how to apply it in various scenarios. KNN Introduction KNN is an non parametric lazy learning algorithm. It is also a lazy algorithm. The dichotomy is pretty obvious here – There is a non existent or minimal training phase but a costly testing phase. Welcome to the UCR Time Series Classification/Clustering Page.
Awk. Filesystem. State of the art. Python. Data mining. Debuger. Created with Camtasia Studio 5. Algorithmic learning theory. Algorithmic learning theory is a mathematical framework for analyzing machine learning problems and algorithms.
Synonyms include formal learning theory and algorithmic inductive inference. Algorithmic learning theory is different from statistical learning theory in that it does not make use of statistical assumptions and analysis. Both algorithmic and statistical learning theory are concerned with machine learning and can thus be viewed as branches of computational learning theory. Distinguishing Characteristics[edit] Unlike statistical learning theory and most statistical theory in general, algorithmic learning theory does not assume that data are random samples, that is, that data points are independent of each other.
Algorithmic learning theory investigates the learning power of Turing machines. Learning in the limit[edit] The concept was introduced in E. Other Identification Criteria[edit] Learning theorists have investigated other learning criteria,[5] such as the following. Modele. Traffic Shaping, Bandwidth Shaping, Packet Shaping with Linux tc htb. Traffic Control with Linux Command Line tool, "tc" By Scott Seong Denial of service attacks are major nuisance for web hosts, and as a web host you'll have to take every measure to protect your resources from DoS attacks.
Our APF, BFD, DDoS and RootKit article describes Linux utilities available to protect from DDoS attack, and also explains installation procedures. This article supplements above article by providing means to control traffic (bandwidth shaping) with Linux "tc" command so that no single machine can waste the entire network bandwidth. Synchronous and Asynchronous I/O. There are two types of input/output (I/O) synchronization: synchronous I/O and asynchronous I/O.
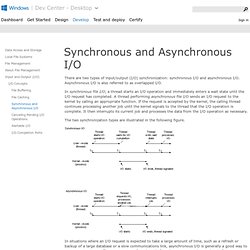
Asynchronous I/O is also referred to as overlapped I/O. In synchronous file I/O, a thread starts an I/O operation and immediately enters a wait state until the I/O request has completed. A thread performing asynchronous file I/O sends an I/O request to the kernel by calling an appropriate function. If the request is accepted by the kernel, the calling thread continues processing another job until the kernel signals to the thread that the I/O operation is complete. It then interrupts its current job and processes the data from the I/O operation as necessary. Lartc. Linux Advanced Routing & Traffic Control HOWTO.
Visualization. Jena. Haskell. Gstreamer. Ontology. Sparql. Latex.