

Teacher Resources. Itgsopedia - home. Whatisanibeducation-EN. Miss Jennie's ITGS Class Blog - Course Expectations. This course is designed to provide the student with an understanding of the uses of information systems and to evaluate the social and ethical implications of technology on society and the individual.
It explores the advantages and disadvantages of the access and use of digitized information at the local and global level. ITGS provides a framework for the student to make informed judgments and decisions about the use of IT within social contexts. Understand the terminology, concepts, and tools relating to specific IT developmentsAnalyze and evaluate the social and ethical implications of IT systems and developments at the local, national, and global level based on real-life situationsExpress ideas clearly and coherently with supporting arguments and examples Tomorrow’s Technology and You, 10th Edition by George Beekman and Ben BeekmanA Gift of Fire: Social, Legal, and Ethical Issues for Computing and the Internet by Sara BaaseITGS Moodle page and Class Blog.
ClassTools.net. Teaching with GIS: Introduction to Using GIS in the Classroom. ABQ2014 - TodaysMeet. IF SL & HL are in the same class.
Ideas of what you do with your SL students while working with HL students on case study? A day ago by Chris IGA (independent grocer's assoc) or ACE Hardware both are locally owned and members of groups similar to that in the case study.a day ago by Chris Difference between case study and papers.. what is includes.. how to prepare the kids... what is expected for students to be able to doa day ago by Lindi Any recommendations on a good GIS project/lesson plan? How early would you introduce the Project if you were teaching SL in one year? How early would you introduce/expose Paper 1,2,3 questions to students? What challenges will be faced by teaching SL in one year?
Best way to go about preparing students for paper 3/dealing with the case studya day ago by Chris What are your feelings about teaching SL the first year and adding the HL content the second year? Developing researching questions and appropriate resources for the EEa day ago by Anthony. THE Journal: Technological Horizons in Education. ITGSWorkshops-Cat-1-2-SandraStark - home. The punishable perils of plagiarism - Melissa Huseman D’Annunzio. The following are excellent resources for teachers and students regarding plagiarism and the proper citation of sources: The OWL at Purdue (Online Writing Lab) Here you'll find numerous articles on topics such as Contextualizing Plagiarism, Authorship and Popular Plagiarism, Copyright, Collaborative Authorship, Avoiding Plagiarism, Summarizing, Paraphrasing, Quoting, and using MLA and APA citations.
Also, you can find extensive Research and Citation Resources on topics such as Conducting Research, Using Research, APA Style, MLA Style, and Chicago Manual of Style. The Plagiarism Spectrum: Instructor Insights into the 10 Types of Plagiarism TurnItIn, the study’s authors, polled both higher and secondary education instructors in order to produce this White Paper. The authors acknowledge that, “the lines of what constitute plagiarism are blurring as the Internet reshapes culture and education” (3), and they provide definitions and examples of the ten most common types of plagiarism. WIRED. Norse - IPViking Live. Every second, Norse collects and analyzes live threat intelligence from darknets in hundreds of locations in over 40 countries.
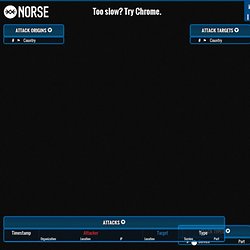
The attacks shown are based on a small subset of live flows against the Norse honeypot infrastructure, representing actual worldwide cyber attacks by bad actors. At a glance, one can see which countries are aggressors or targets at the moment, using which type of attacks (services-ports). Hovering over the Attack Origins, Attack Targets, or Attack Types will highlight just the attacks emanating from that country or over that service-port respectively. Hovering over any bubble on the map, will highlight only the attacks from that location and type. Press s to toggle table sizes. Norse exposes its threat intelligence via high-performance, machine-readable APIs in a variety of forms.
For more information, please contact: inquiry@norse-corp.com Each particle represents an attack. SMART Education. Free Online Learning at GCFLearnFree.