

Decrypting LSA Secrets. The LSA secrets store is a protected storage area used the the Local Security Authority (LSA) system in Windows to keep important pieces of information safe from prying eyes.

As with Syskey, however, we will see that these secrets are only obfuscated, and once the mechanism is known, we can extract them from the registry with ease. Even without knowing the obfuscation algorithm, however, it is possible to read the values of this data using the LsarQuerySecret function exported by lsasrv.dll, but only if one has the LocalSystem privilege (for example, if the process is running under the SYSTEM account).
What kind of data is stored in these secrets? Here are a few that I've come across: LSA Secrets in the Registry LSA secrets are stored in the SECURITY hive of the registry, in the key SECURITY\Policy\Secrets. The values of the CurrVal and OldVal keys are unnamed, and displayed as "(Default)" in regedit. Apache Tomcat Exploitation. In this article we will focus on the Apache Tomcat Web server and how we can discover the administrator’s credentials in order to gain access to the remote system.So we are performing our internal penetration testing and we have discovered the Apache Tomcat running on a remote system on port 8180.
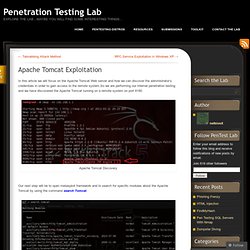
Apache Tomcat Discovery Our next step will be to open metasploit framework and to search for specific modules about the Apache Tomcat by using the command search Tomcat. Available Modules for Apache Tomcat We have found an auxiliary scanner which will be the tool for our attempt to login to the Tomcat Application Manager.So we are selecting the scanner by using the command use auxiliary/scanner/http/tomcat_mgr_login and then we are configuring it properly as it appears on the next screenshot.
Exploits and Code. Capturing NTLM Hashes Like Pokemon!

Exploit Framework Modules I really like exploit frameworks for writing exploit codes. Combined with a good debugger I can usually whip up an exploit in half and hour for the easier things. Most of the time developing exploits is finding the vuln software, installing it, finding where the error occurs, writing the proof code and making the exploit code stable. Metasploit is awesome, Canvas is awesome, CORE Impact is expensive Here are just some of the current code I'm permitted to share: Miscellanous Security Code Various other bits of scripts and code I've written over the last few years. ColdFusion CFEXECUTE script - When you have upload privs to a ColdFusion box, use this to run commands in the privilege of the ColdFusion service. ColdFusion MX Admin Password - For pre-7 I think. ColdFusion/WSFTP.INI Password Decoder - Kinda says it all. Changelog: Mar 7, 07 - First post! Passwords - SkullSecurity. Password dictionaries These are dictionaries that come with tools/worms/etc, designed for cracking passwords.
As far as I know, I'm not breaking any licensing agreements by mirroring them with credit; if you don't want me to host one of these files, let me know and I'll remove it. Leaked passwords Passwords that were leaked or stolen from sites. I'm hosting them because it seems like nobody else does (hopefully it isn't because hosting them is illegal :)). The best use of these is to generate or test password lists. Note: The dates are approximate. Statistics I did some tests of my various dictionaries against the different sets of leaked passwords. Miscellaneous non-hacking dictionaries These are dictionaries of words (etc), not passwords.
DirBuster has some awesome lists, too -- usernames and filenames. [LAFKON] - A movie about Trusted Computing. On Information Entropy. In this blog post you will learn about entropy within the domain of information theory.
You will learn what entropy is and how to compute it. You will be shown some simple C code snippets to bring theory into application. Also, you will be shown why it is an important measurement in the field of computer security. Finally, we will cover some practical applications of entropy calculation and analysis. Introduction Before we can adequately define entropy, we need to first define information. Consider an information source X that can produce, with equal probability, 6 symbols (also known as outcomes): A, B, C, D, E, and F. Entropy gives us a way to quantify the average number of bits needed to convey a message when considering all possible outcomes.
Nomenclature Clarification According to Internet lore, at the time of discovery, Shannon didn’t know what to call his new unit of measure and so he asked the famous mathematician John von Neumman. Pith A Common Information Source Denouement. Infosec. BackTrack Linux - Penetration Testing Distribution. OWASP. 1337day Inj3ct0r Exploit Database : vulnerability : 0day : shellcode by Inj3ct0r Team. Exploits Database by Offensive Security.
Ophcrack. Ettercap. Aircrack-ng. Black Hat.