

DDoS Mitigation Skills Are In Demand. I recently advertised on Kaggle to find a data scientist to help answer a question I was pondering: With the spate of distributed denial of service (DDoS) attacks in the last year, were companies seeking candidates with corresponding mitigation skills?
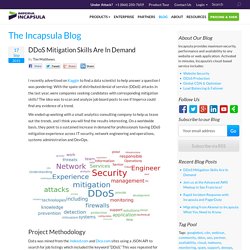
The idea was to scan and analyze job board posts to see if Imperva could find any evidence of a trend. We ended up working with a small analytics consulting company to help us tease out the trends, and I think you will find the results interesting. On a worldwide basis, they point to a sustained increase in demand for professionals having DDoS mitigation experience across IT security, network engineering and operations, systems administration and DevOps. Project Methodology Data was mined from the Indeed.com and Dice.com sites using a JSON API to search for job listings which included the keyword “DDoS.” Indeed.com yielded 1,177 listings going back four months; this forms the basis for our analysis.
Tools and Expressions Used. Beware of Token Stealing Man-in-the-Cloud Hackers (MITC) Anyone who uses any cloud service needs to be aware of the potential for hackers to steal the tokens these services use when you log in.
If you use Dropbox, Box, Google Drive, or Microsoft OneDrive, a token permits you to access your data from any of your devices. When someone steals that token they can take over your account, stealing data or distributing infected files through it. While most of us are not security experts and do not need to know the technical details, I did want to make you aware of this issue. As individual users, there may not be much we can do other than notify others who can resolve the issues if we run into them. If you notice activities in your accounts that you are sure you did not originate, don’t shrug it off – make sure the solution or your IT or security staff knows about it.
Gail Gardner sur Twitter : "A New Cloud Threat for 2015: The Man in the Cloud Attack @SkyFenceNet #security. A New Cloud Threat for 2015: The Man in the Cloud Attack. The ability to share files and access applications across devices and borders has quite literally revolutionized the way employees collaborate.
But it’s not all good news. New threats, such as the “Man in the Cloud Attack” (MITC), underscore the difficulties in protecting data stored in the cloud. The problem is that very few companies are defending themselves against this new threat, and most don’t fully understand the implications. Just a few days ago, the Imperva Application Defense Center (ADC) research arm unveiled its August Hacker Intelligence Initiative Report at Black Hat USA 2015.
The report details how an MITC attack can co-opt popular file synchronization services, such as OneDrive, Google Drive, Box and Dropbox, turning them into devastating attack vectors not easily detected by common security measures. To better inform you about MITC attacks, it’s helpful to answer two key questions. Gail Gardner sur Twitter : "Disasters In the News: Is Your Business Prepared? by @GrowMap @SiteProNews #security #hosting. Disasters In the News: Is Your Business Prepared? July 13, 2015.

What is the Best CDN Model? A Closer Look At Akamai, CloudFront And Incapsula. The CDN market is quite diverse, encompassing dozens of players serving a wide variety of industries and geographies.
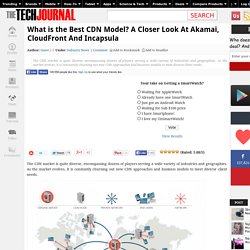
As the market evolves, it is constantly churning out new CDN approaches and business models to meet diverse client needs. Loading ... This article discusses traditional CDN, dedicated CDN and security CDN approaches, as epitomized by Akamai, Amazon CloudFront and Incapsula, respectively. SimonPorter sur Twitter : "The low down on #cloud #security and how to stay secure.
Interview: The low down on cloud security and how to stay secure. Whitepaper - Master the cloud journey free to download now: Security and the cloud are both key topics in the world of technology at the moment – along with areas such as BYOD and the Internet of Things – so if you put the two together, you’ve got double the power.
SEE ALSO: Excited for Windows 10? You won't believe how far it's come since Windows 1.0 We recently had the chance to speak to Charles Sweeney, CEO of content filtering and security company Bloxx, about its new Tru-View cloud technology, data breaches and the main issues in cloud security. The full interview can be found below. Attacks Resemble Advanced Persistent Threats (APT) Distributed denial of service (DDoS) assaults continue to be a nuisance for online businesses and their customers.
Worse, the downtime caused by attacks is costly for organizations and frustrating for consumers. With no signs of abating, understanding the methods and capabilities of perpetrators is essential to maintaining good defenses. In our Q2 2015 DDoS Global Threat Landscape Report we share unique research data, collected in the course of mitigating thousands of DDoS assaults against Imperva Incapsula-protected domains and network infrastructures. Leveraging this large dataset, we are able to produce statistical research of DDoS events—one which provides a bird’s-eye view of the current state of the DDoS threat landscape, focusing on latest attack methods, attack frequency and duration patterns.
As indicated by its title, this is our premier quarterly report on this topic. Welcome to Forbes.