

Home Page. Aircrack-ng. Newbie_guide [Aircrack-ng] Idea and initial work: ASPj Additions by: a number of good souls Last updated: May 09, 2008 This tutorial will give you the basics to get started using the aircrack-ng suite.
![newbie_guide [Aircrack-ng]](http://cdn.pearltrees.com/s/pic/th/newbie-guide-aircrack-ng-141589612)
It is impossible to provide every piece of information you need and cover every scenario. So be prepared to do some homework and research on your own. The Forum and the Wiki have lots of supplementary tutorials and information. Although it does not cover all the steps from start to finish like this tutorial, the Simple WEP Crack tutorial covers the actual aircrack-ng steps in much more detail. The first step in getting aircrack-ng working properly on your Linux system is patching and installing the proper driver for your wireless card. Needless to say, you need a wireless card which is compatible with the aircrack-ng suite. To determine to which category your card belongs to, see hardware compatibility page.
First, you need to know which chipset is used in your wireless card and which driver you need for it. Source. Airmon-ng. Description This script can be used to enable monitor mode on wireless interfaces.
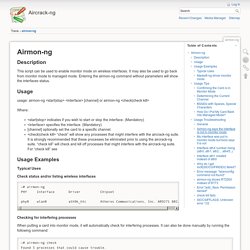
It may also be used to go back from monitor mode to managed mode. Entering the airmon-ng command without parameters will show the interfaces status. Usage. Airodump-ng [Aircrack-ng] Description Airodump-ng is used for packet capturing of raw 802.11 frames and is particularly suitable for collecting WEP IVs (Initialization Vector) for the intent of using them with aircrack-ng.
![airodump-ng [Aircrack-ng]](http://cdn.pearltrees.com/s/pic/th/airodump-ng-aircrack-140275749)
If you have a GPS receiver connected to the computer, airodump-ng is capable of logging the coordinates of the found access points. Additionally, airodump-ng writes out several files containing the details of all access points and clients seen. Usage. How to determine interface name for aircrack suite on windows. Craccare reti wifi con Aircrack-ng, guida sicurezza delle reti. Wardriving - Wikipedia. A free public Wi-Fi access point Wardriving is the act of searching for Wi-Fi wireless networks by a person in a moving vehicle, using a portable computer, smartphone or personal digital assistant (PDA).
Etymology[edit] War driving originated from wardialing, a method popularized by a character played by Matthew Broderick in the film WarGames, and named after that film. War dialing consists of dialing every phone number in a specific sequence in search of modems.[4] Warbiking is similar to wardriving, but is done from a moving bicycle or motorcycle. Warwalking, or warjogging, is similar to wardriving, but is done on foot rather than from a moving vehicle. Warrailing, or Wartraining, is similar to wardriving, but is done on a train or tram rather than from a slower more controllable vehicle. Warkitting is a combination of wardriving and rootkitting.[5] In a warkitting attack, a hacker replaces the firmware of an attacked router. Mapping[edit] Legal and ethical considerations[edit] Wardriving. Warchalking - Wikipedia. Warchalking is the drawing of symbols in public places to advertise an open Wi-Fi network.
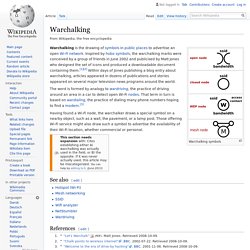
Inspired by hobo symbols, the warchalking marks were conceived by a group of friends in June 2002 and publicised by Matt Jones who designed the set of icons and produced a downloadable document containing them.[1][2] Within days of Jones publishing a blog entry about warchalking, articles appeared in dozens of publications and stories appeared on several major television news programs around the world. Having found a Wi-Fi node, the warchalker draws a special symbol on a nearby object, such as a wall, the pavement, or a lamp post. Those offering Wi-Fi service might also draw such a symbol to advertise the availability of their Wi-Fi location, whether commercial or personal.
Warchalking. Da Wikipedia, l'enciclopedia libera.
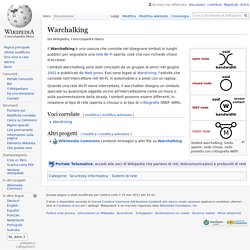
Simboli warchalking, (nodo aperto, nodo chiuso, nodo protetto con crittografia WEP) Il Warchalking è una usanza che consiste nel disegnare simboli in luoghi pubblici per segnalare una rete Wi-Fi aperta, cioè che non richiede chiavi d'accesso. I simboli warchalking sono stati concepiti da un gruppo di amici nel giugno 2002 e pubblicati da Matt Jones. Essi sono legati al Wardriving, l'attività che consiste nell'intercettare reti Wi-Fi, in automobile o a piedi con un laptop. Quando una rete Wi-Fi viene intercettata, il warchalker disegna un simbolo speciale su qualunque oggetto vicino all'intercettazione come un muro o sulla pavimentazione della strada. Thiefing. Da Wikipedia, l'enciclopedia libera.
Thiefing è quell'attività che consiste nel rubare servizi di tipo informatico sfruttando le minime misure di protezione adottate dagli utenti per i propri dispositivi. Il thiefing più frequente e facile da realizzare è quello che può mettere in atto chiunque cercando con il proprio PC (dotato di scheda wireless) le reti senza fili disponibili nello spazio circostante. Nel caso in cui venga individuata una rete wireless non protetta è possibile utilizzare la connessione ad Internet altrui (quando presente) o qualunque altro servizio accessibile a partire dal dispositivo violato. Un caso eclatante[1] è stato quello di un imprenditore statunitense (Edwin Pena) e del suo giovane "aiutante" (Robert Moore). I due, ottenuto l'accesso all'hardware preposto alla gestione dei servizi voce Voice over IP di numerose aziende del settore delle comunicazioni, hanno rivenduto più di un milione di minuti di servizio ad altre compagnie a prezzi stracciati.
Untitled. Hyperlink. Aircrack.